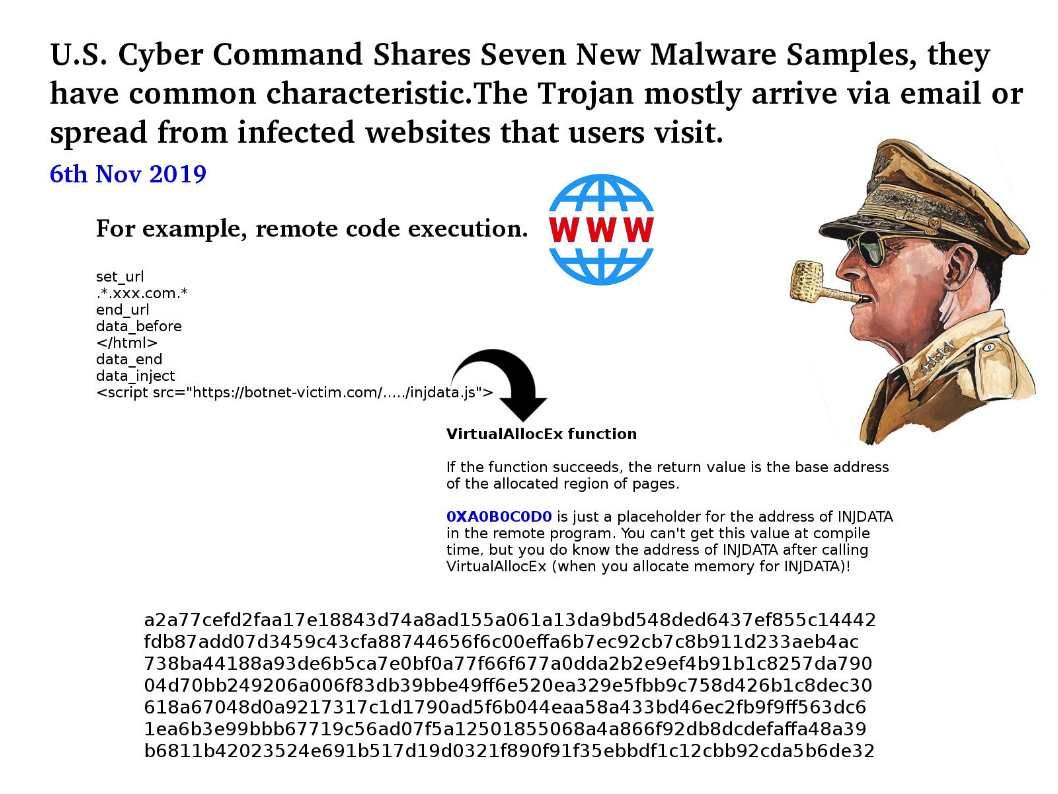
Preface: The Trojan mostly arrive via email or spread from infected websites that users visit.
Background: U.S. Cyber Command has released seven malware samples. The malware hash shown as below: a2a77cefd2faa17e18843d74a8ad155a061a13da9bd548ded6437ef855c14442 fdb87add07d3459c43cfa88744656f6c00effa6b7ec92cb7c8b911d233aeb4ac 738ba44188a93de6b5ca7e0bf0a77f66f677a0dda2b2e9ef4b91b1c8257da790 04d70bb249206a006f83db39bbe49ff6e520ea329e5fbb9c758d426b1c8dec30 618a67048d0a9217317c1d1790ad5f6b044eaa58a433bd46ec2fb9f9ff563dc6 1ea6b3e99bbb67719c56ad07f5a12501855068a4a866f92db8dcdefaffa48a39 b6811b42023524e691b517d19d0321f890f91f35ebbdf1c12cbb92cda5b6de32
Our observation: VC++ method of injecting code into other programs is popular (see below):
- Put your code into a DLL; then use the windows hook to map it to the remote program.
- Put your code into a DLL; then use CreateRemoteThread and LoadLibrary to map it to the remote program.
- Copy your code directly to the remote program without using a DLL (using WriteProcessMemory)
So, how can you protect yourself against malicious code? Staying alert!