Preface: Are you afraid of someone suddenly controlling your car?
Background: AutoPi is a small device that plugs into the OBD-II port of your car.
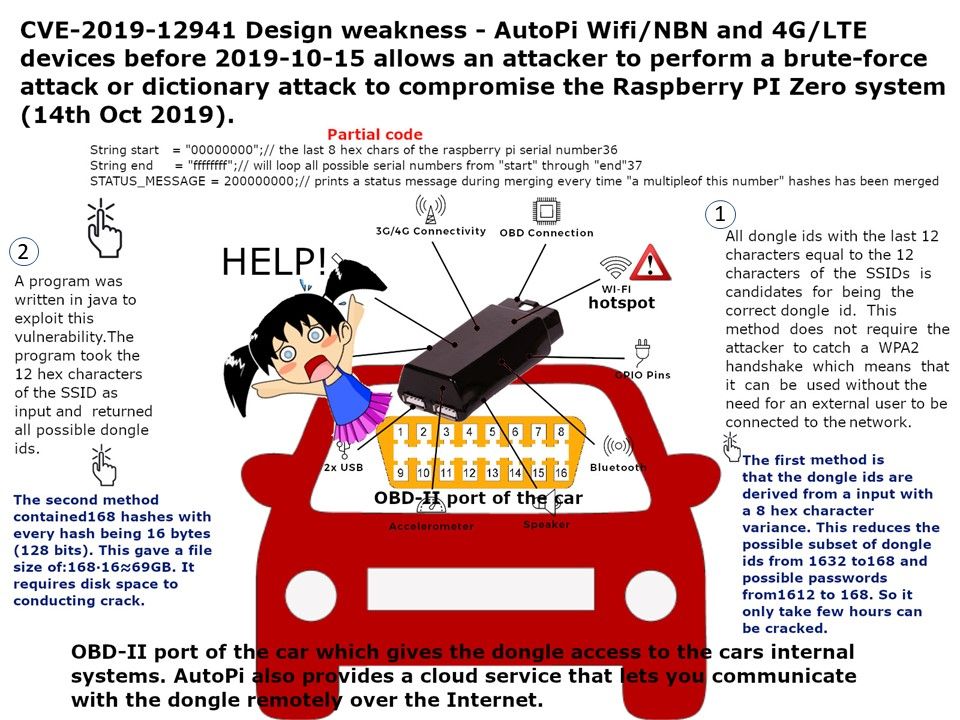
What is OBD-II port? OBD-II port of the car which gives the dongle access to the cars internal systems. AutoPi also provides a cloud service that lets you communicate with the dongle remotely over the Internet.
Vulnerability details: When user connected to the WiFi, it is also possible to SSH into the device. Both the web portal terminal and the SSH terminal grants root access, meaning that full access of the devices is given when connected through WiFi.
Since the wifi password mechanism design weakness. Attacker can use following method to receive the WPA2 authentication password. The default WiFi password and WiFi SSID are derived from the same hash function output (input is only 8 characters), which allows an attacker to deduce the WiFi password from the WiFi SSID. So it only take few hours can be cracked. For more details, please refer to attached infographic for reference.
Should you have interested, please download the technical white paper to review. https://www.kth.se/polopoly_fs/1.931922.1571071632!/Burdzovic_Matsson_dongle_v2.pdf