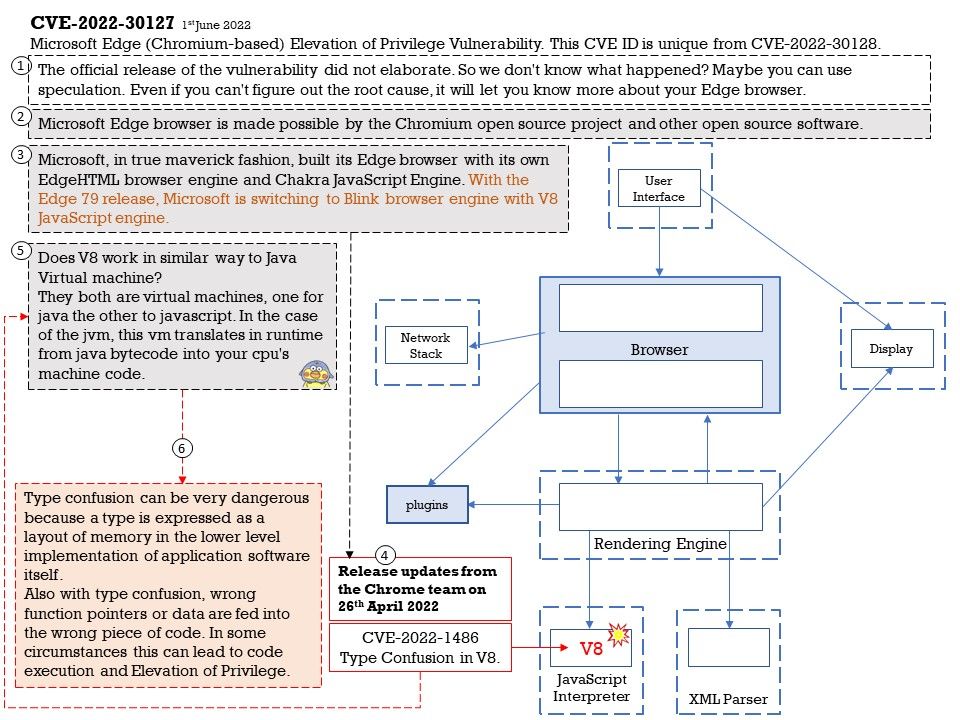
Preface: The official release of the vulnerability did not elaborate. So we don’t know what happened? Maybe you can use speculation. Even if you can’t figure out the root cause, it will let you know more about your Edge browser.
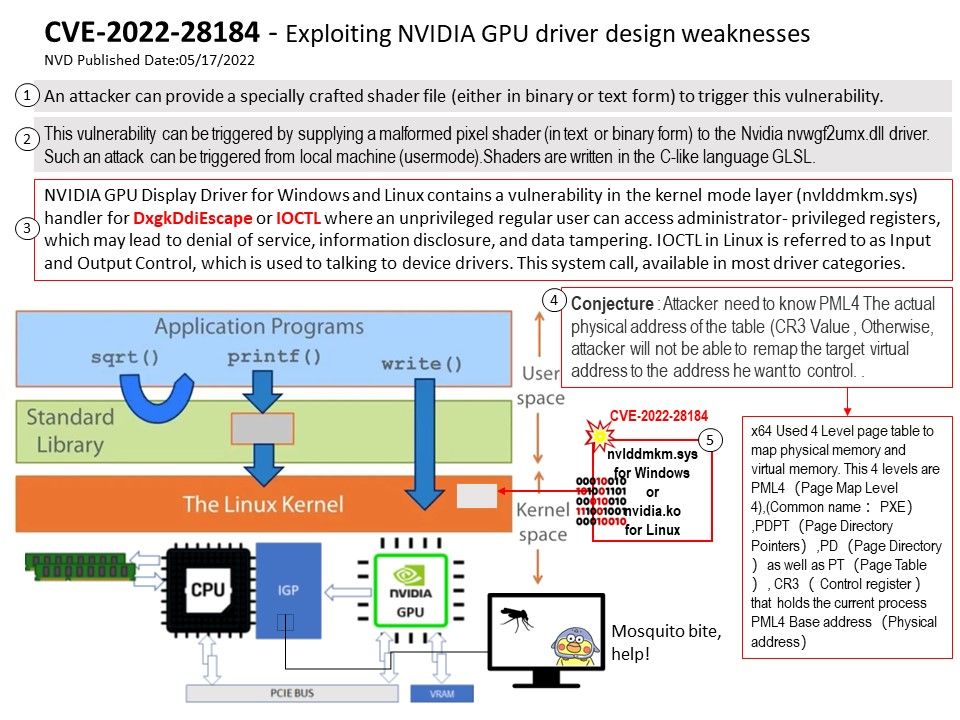
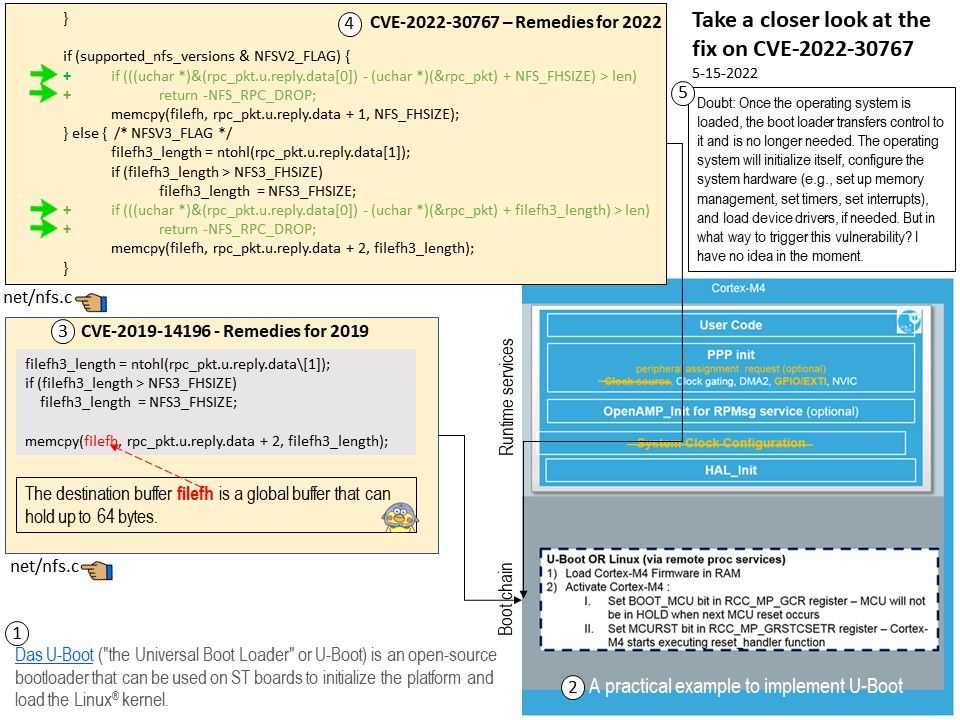
Background: The new Microsoft Edge is based on Chromium and was released on January 15, 2020. It is compatible with all supported versions of Windows, and macOS.
The chrome engine is used for Microsoft edge chromium. The features of Microsoft edge chromium are not stable as they keep on changing. The Microsoft edge chromium offers many types of user interfaces. From customer point of view, Microsoft Edge is still developing till now.
Microsoft, in true maverick fashion, built its Edge browser with its own EdgeHTML browser engine and Chakra JavaScript Engine. With the Edge 79 release, Microsoft is switching to Blink browser engine with V8 JavaScript engine.
According to Stable Channel Update for Desktop issued on Tuesday, April 26, 2022. A Type Confusion vulnerability found on V8 Javascript Engine.
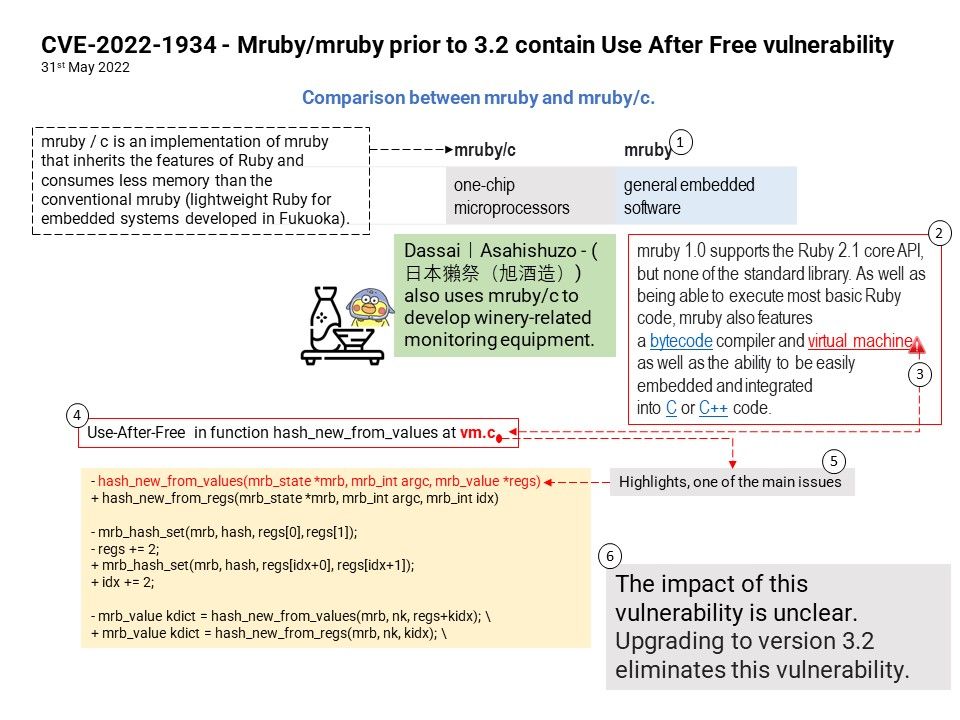
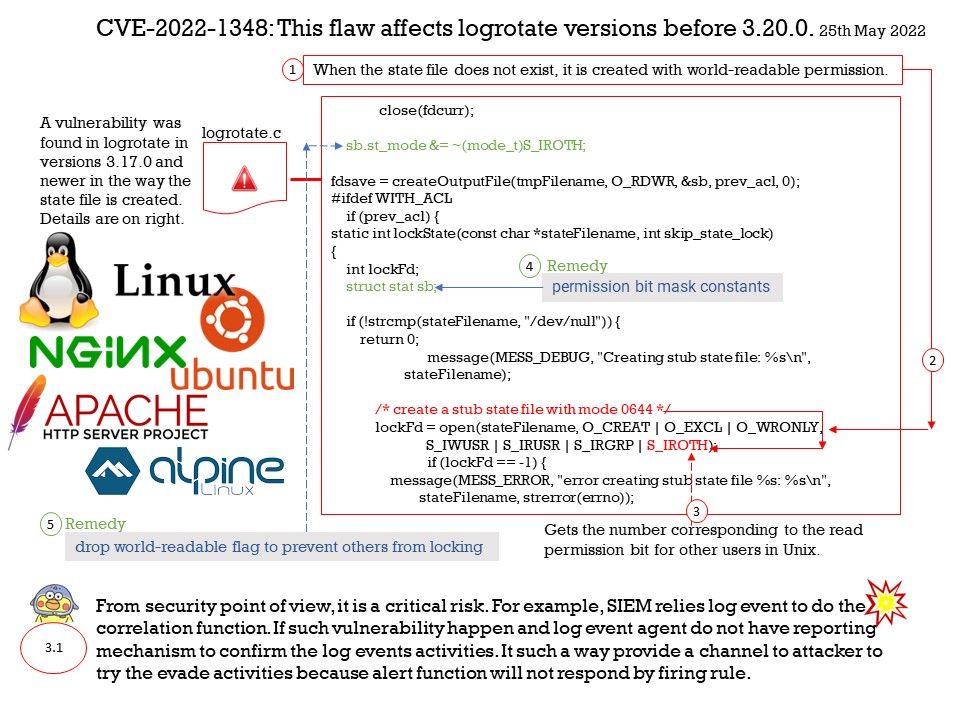
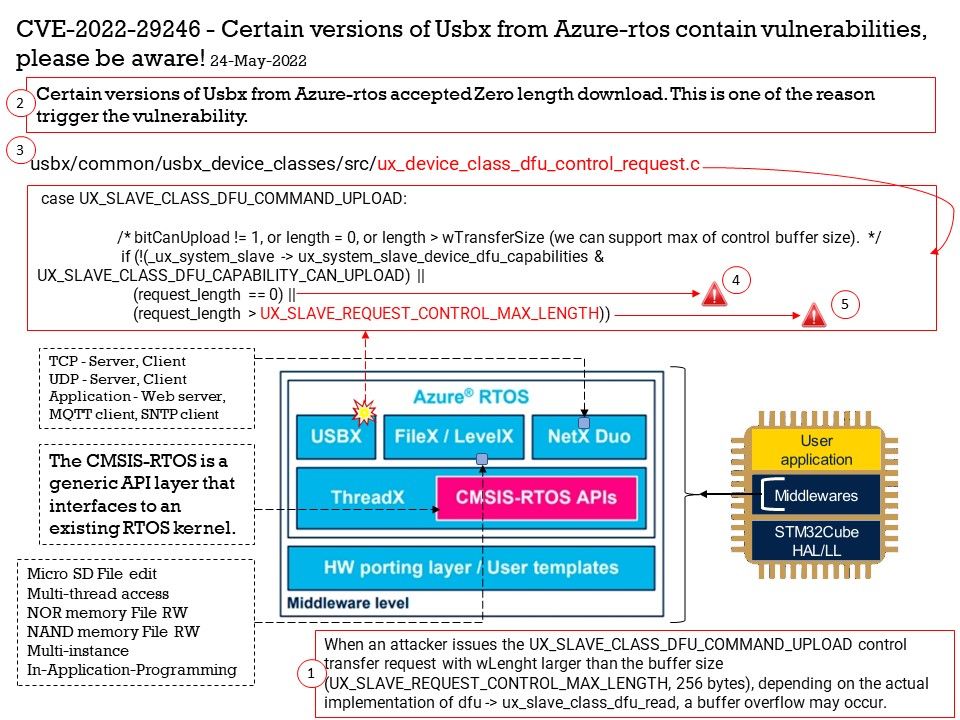
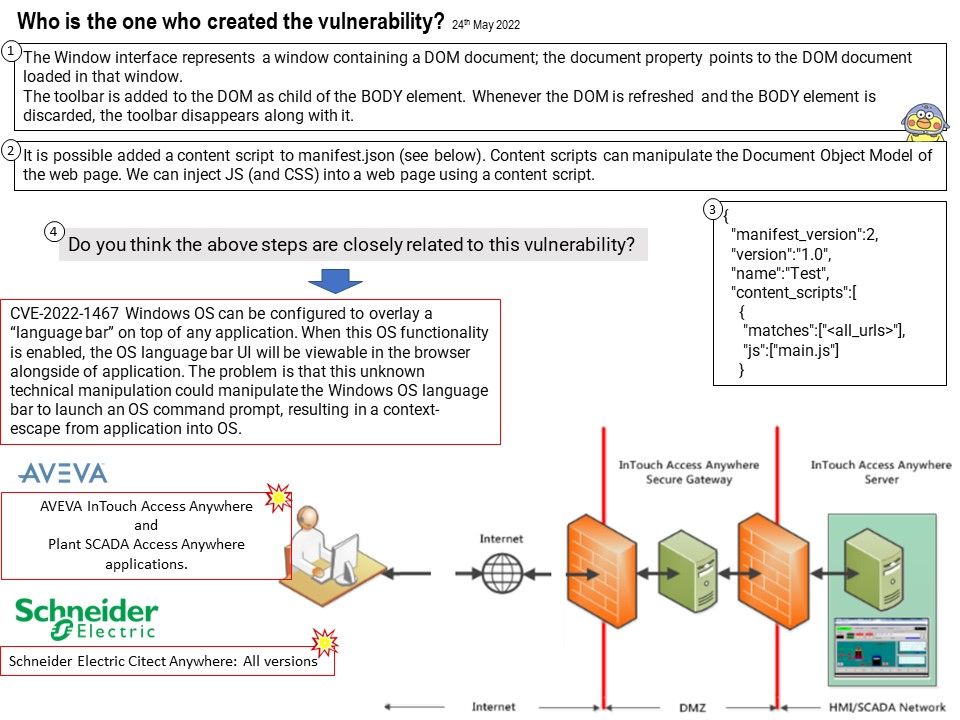
Vulnerability details: Microsoft Edge (Chromium-based) Elevation of Privilege Vulnerability. This CVE ID is unique from CVE-2022-30128.
Based on the attached diagram and the above details, I speculate that CVE-2022-30127 is related to a javascript Engine design flaw. The technical problem that occurs will be a type confusion vulnerability.
Type confusion can be very dangerous because a type is expressed as a layout of memory in the lower level implementation of application software itself. Also with type confusion, wrong function pointers or data are fed into the wrong piece of code. In some circumstances this can lead to code execution and Elevation of Privilege.
Official announcement: https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2022-30127
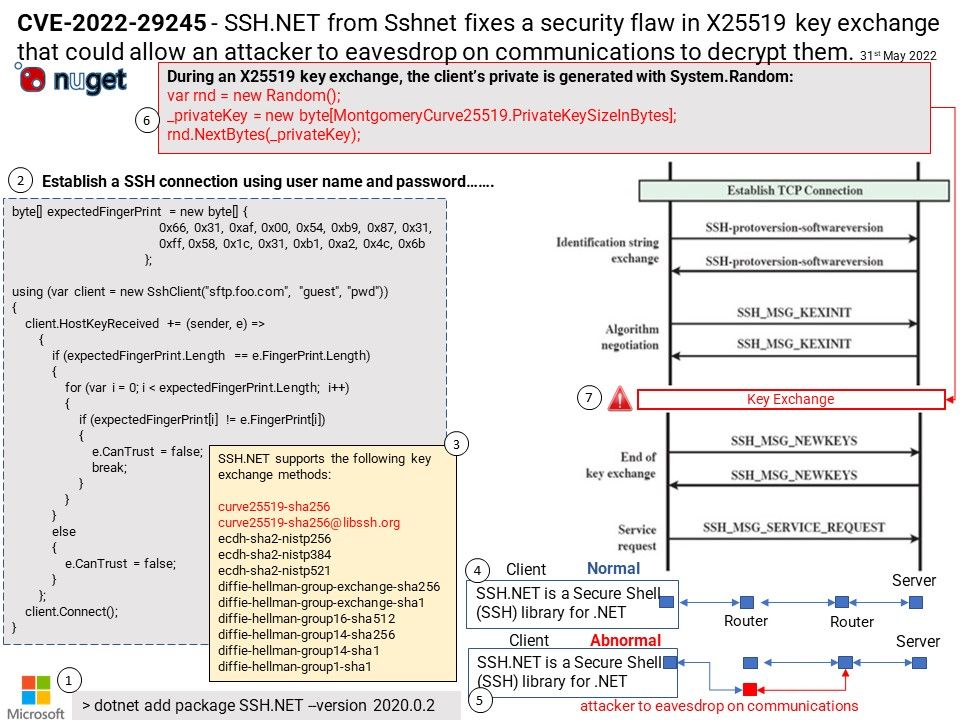
.jpg)
.jpg)