Preface: Looking back, a vulnerability was discovered in NVIDIA GPU Display Driver on 2016. A flaw exists in the kernel mode layer (nvlddmkm.sys) handler for DxgDdiEscape IDs 0x600000E, 0x600000F, and 0x6000010 due to improper validation of user-supplied input that is used as an index to an internal array. A local attacker can exploit this to corrupt memory, resulting in a denial of service condition or an escalation of privileges.
Background: NVIDIA GPU Display Driver support 2 different operation systems. So called the kernel mode layer (nvlddmkm.sys for Windows or nvidia.ko for Linux).
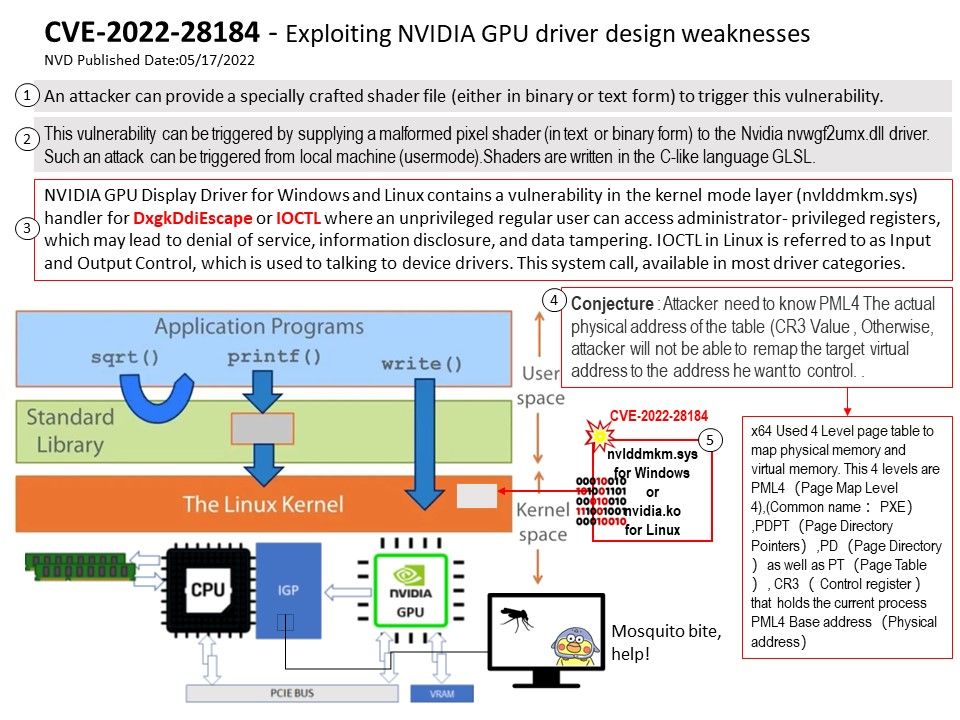
Vulnerability details: NVIDIA GPU Display Driver for Windows and Linux contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape or IOCTL where an unprivileged regular user can access administrator- privileged registers, which may lead to denial of service, information disclosure, and data tampering. IOCTL in Linux is referred to as Input and Output Control, which is used to talking to device drivers. This system call, available in most driver categories.
Conjecture : Attacker need to know PML4 The actual physical address of the table (CR3 Value) , Otherwise, attacker will not be able to remap the target virtual address to the address he want to control.
There are other ideas.Use Paging table Primitives to destroy bitmaps , And use it GDI Primitive language to restore our relevant mmPfnDatabase entry .
Ref: x64 Used 4 Level page table to map physical memory and virtual memory. This 4 levels are PML4(Page Map Level 4),(Common name :PXE),PDPT(Page Directory Pointers),PD(Page Directory)as well as PT(Page Table), CR3( Control register )that holds the current process PML4 Base address(Physical address).
CR3 enables the processor to translate linear addresses into physical addresses by locating the page directory and page tables for the current task.
Vendor announcement: Security Bulletin: NVIDIA GPU Display Driver – May 2022 – https://nvidia.custhelp.com/app/answers/detail/a_id/5353