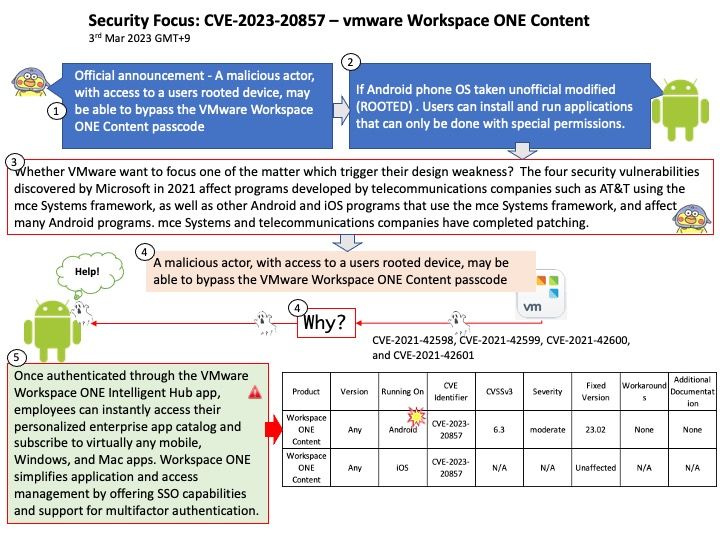
Preface: As a computer end user. When there is a vulnerability, the only way is to patch it according to the official announcement.
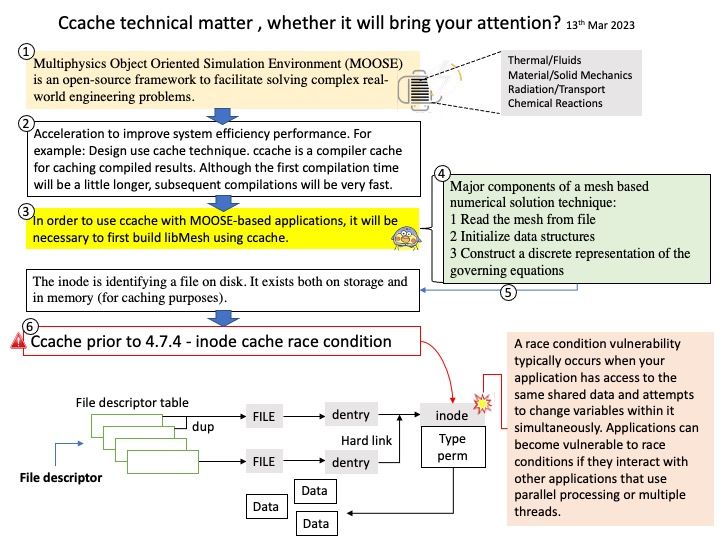
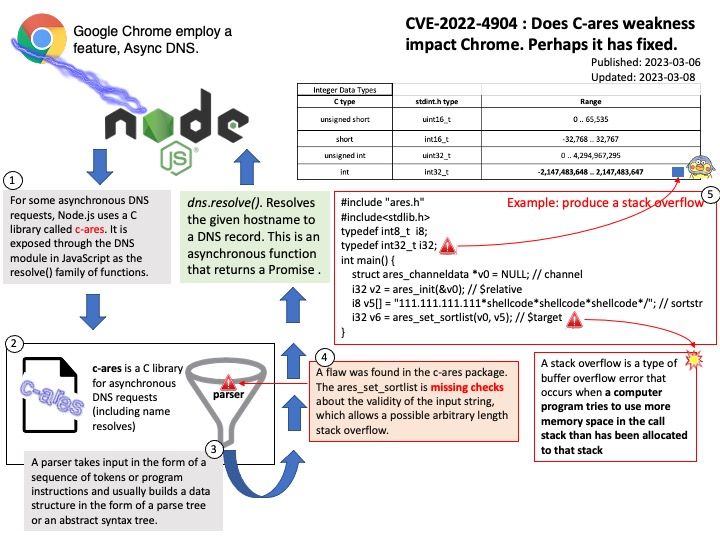
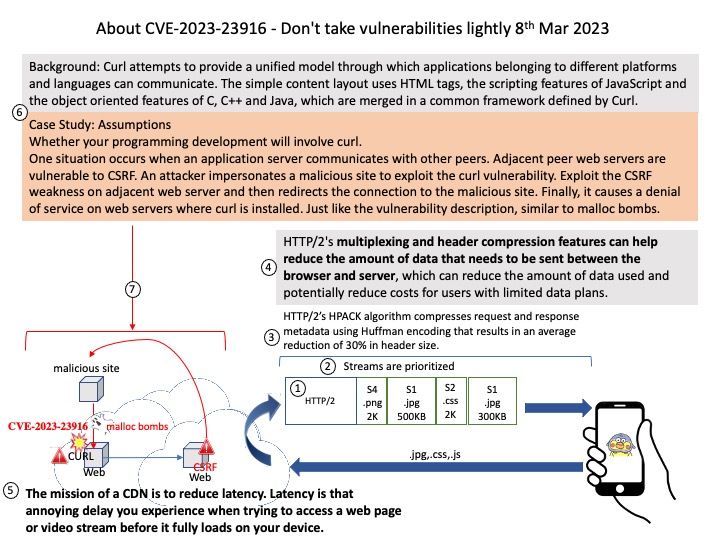
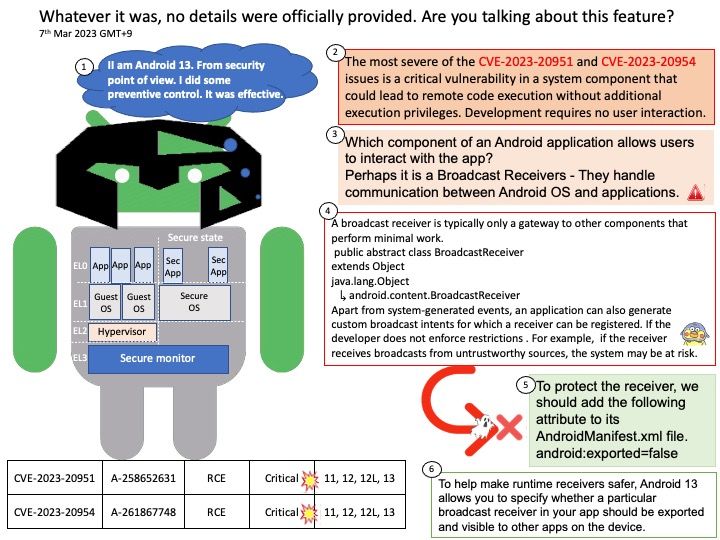
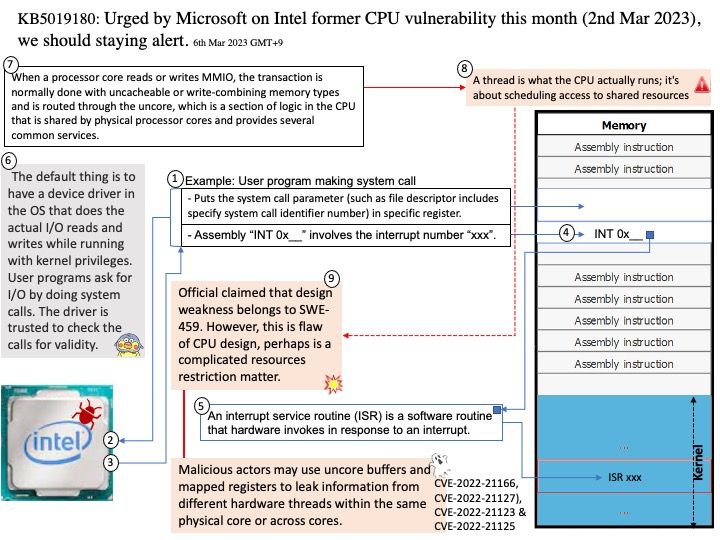
GnuTLS is a secure communications library implementing the SSL, TLS and DTLS protocols and technologies around them. It provides a simple C language API to access the secure communications protocols.
Remark: If OpenSSL is selected over GnuTLS, neither libnettle nor libgcrypt will be used.
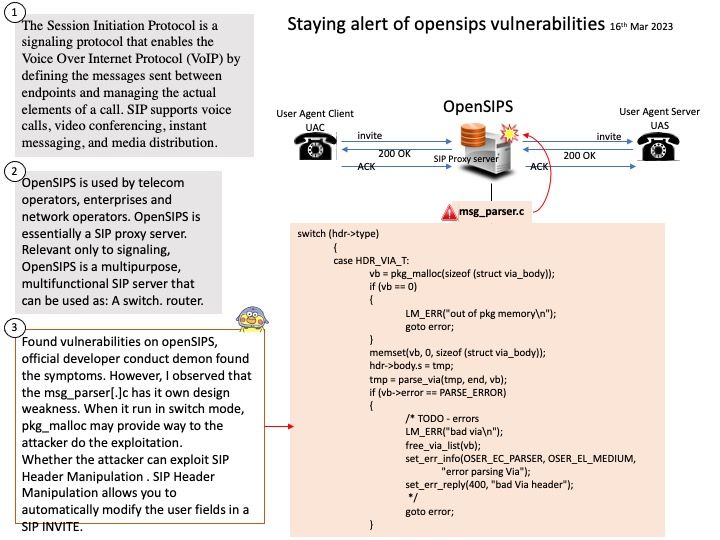
Background: GnuTLS is a free software implementation of the TLS, SSL and DTLS protocols. It offers an application programming interface for applications to enable secure communication over the network transport layer, as well as interfaces to access X.509, PKCS #12, OpenPGP and other structures.
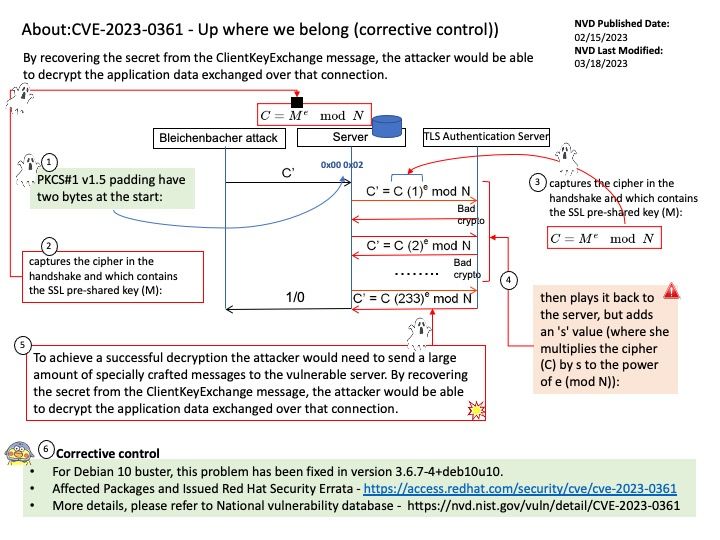
Vulnerability details: A timing side-channel in the handling of RSA ClientKeyExchange messages was discovered in GnuTLS. This side-channel can be sufficient to recover the key encrypted in the RSA ciphertext across a network in a Bleichenbacher style attack. To achieve a successful decryption the attacker would need to send a large amount of specially crafted messages to the vulnerable server. By recovering the secret from the ClientKeyExchange message, the attacker would be able to decrypt the application data exchanged over that connection.
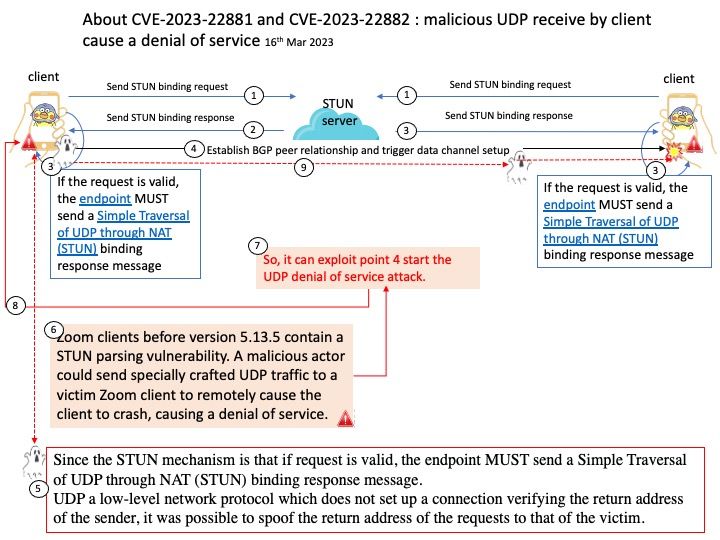
SUSE – Recommended update for gnutls: This update for gnutls fixes the following issues:
FIPS: Establish PBKDF2 additional requirements [bsc #1209001]
- Set the minimum output key length to 112 bits (FIPS 140-3 IG D.N)
- Set the minimum salt length to 128 bits (SP 800-132 sec. 5.1)
- Set the minimum iterations count to 1000 (SP 800-132 sec 5.2)
- Set the minimum passlen of 20 characters (SP SP800-132 sec 5)
- Add regression tests for the new PBKDF2 requirements.
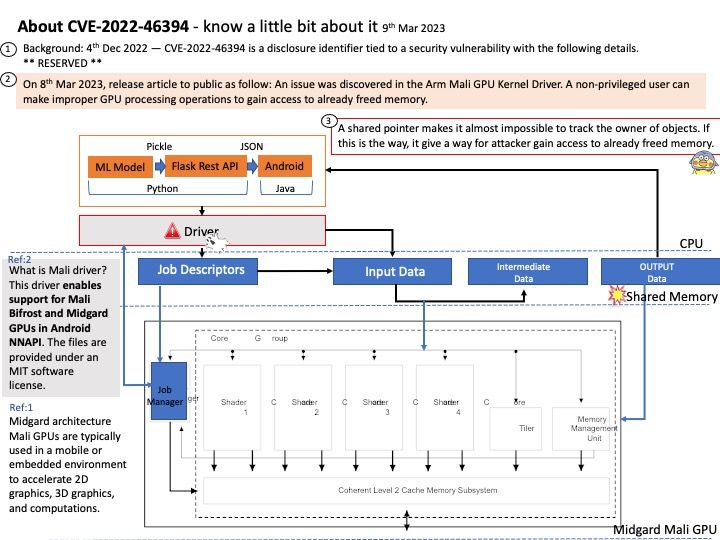
Official announcement: please refer to National vulnerability database – https://nvd.nist.gov/vuln/detail/CVE-2023-0361