Preface: Windows 10’s market share jumped from 68.86% in January 2023 to 73.31% in February 2023. Windows 11’s market share increased as well, but only by 1.01% to 19.13% in February 2023, said ghacks[.]net.
Remark: Windows 10 continues to be supported by Microsoft until October 2025.
Background: Some said, Intel microprocessors use direct I/O. Yes, Direct IO is talking about Data Direct I/O Technology. With Intel DDIO, Intel Ethernet Server Adapters and controllers talk directly to the processor cache without a detour via system memory. Intel DDIO makes the processor cache the primary destination and source of I/O data rather than the main memory. Traditionally, inbound PCIe transactions target the main memory, and data movement from the I/O device to the consuming core requires multiple DRAM accesses. For I/O-intensive use cases, such as software data planes, this scheme becomes inapplicable. But the design weakness is not another matter than above.
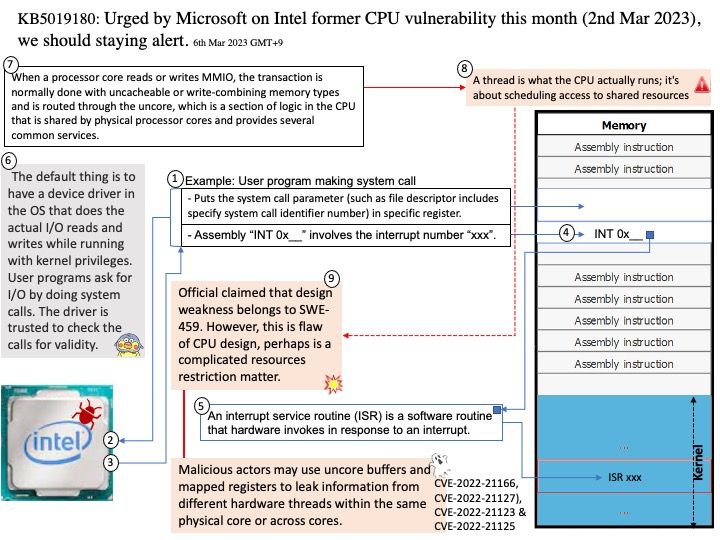
Below vulnerability is focusing to the following concept. The default thing is to have a device driver in the OS that does the actual I/O reads and writes while running with kernel privileges. User programs ask for I/O by doing system calls. The driver is trusted to check the calls for validity.
The Memory Mapped design objective. It stores program instructions and data that are used repeatedly in the operation of programs or information that the CPU is likely to need next. The computer processor can access this information more quickly from the cache than from the main memory.
Vulnerability details: Processor MMIO Stale Data Vulnerabilities are a class of memory-mapped I/O (MMIO) vulnerabilities that can expose data. When a processor core reads or writes MMIO, the transaction is normally done with uncacheable or write-combining memory types and is routed through the uncore, which is a section of logic in the CPU that is shared by physical processor cores and provides several common services. Malicious actors may use uncore buffers and mapped registers to leak information from different hardware threads within the same physical core or across cores.
Related vulnerabilities: CVE-2022-21166, CVE-2022-21127), CVE-2022-21123 & CVE-2022-21125
Official announcement: KB5019180: Security vulnerabilities exist in Memory Mapped I/O for some Intel processors for Windows 10. The related official article and advisory can be found in follow link – https://support.microsoft.com/en-us/topic/kb5019180-security-vulnerabilities-exist-in-memory-mapped-i-o-for-some-intel-processors-for-windows-10-version-20h2-21h2-and-22h2-march-2-2023-f8c174f1-ce5c-469f-9eac-21f8af66b8ea