Preface: Make sure to use the STUN message format specified in standard, to perform the MESSAGE-INTEGRITY computation. This protocol uses Simple Traversal of UDP through NAT (STUN) binding request and response messages for connectivity checks between the two endpoints.
Background: Most attackers utilize UDP to launch amplification attacks since reflection of traffic with spoofed IP source address is possible due to the lack of proper handshake. While UDP makes it easy to launch reflected amplification attacks.
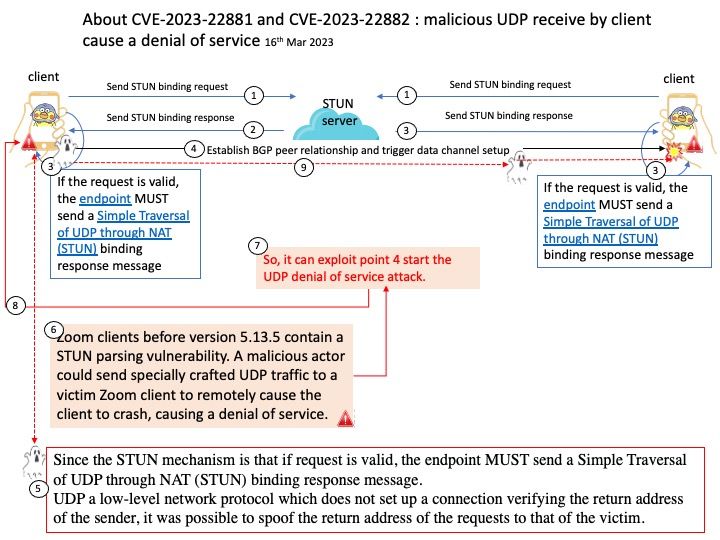
Since the STUN mechanism is that if request is valid, the endpoint MUST send a Simple Traversal of UDP through NAT (STUN) binding response message.
UDP a low-level network protocol which does not set up a connection verifying the return address of the sender, it was possible to spoof the return address of the requests to that of the victim.
Vulnerability details: Zoom clients before version 5.13.5 contain a STUN parsing vulnerability. A malicious actor could send specially crafted UDP traffic to a victim Zoom client to remotely cause the client to crash, causing a denial of service.
Official details: Please refer to the URL link – https://explore.zoom.us/en/trust/security/security-bulletin/