Preface: Google Chrome employ a feature, Async DNS. The objective is avoid traditional way using public DNS function. When google (Chrome) running, all the resolving domain name activities will be point to google DNS server.In Security point of view, it is good. At least it reduced unknown trap intend to hunting victim. It benefits to chrome reduce attack by threata actors detect the vulnerabilities. This is true, statistic shown that cyber attack require compromised or black list domain server.
It can be enabled or disabled (see below):
Open “chrome://flags/#enable-async-dns” Change option to “Disabled” Click “Relaunch Now” at the bottom of the page. After relaunch open “chrome://net-internals/#dns”
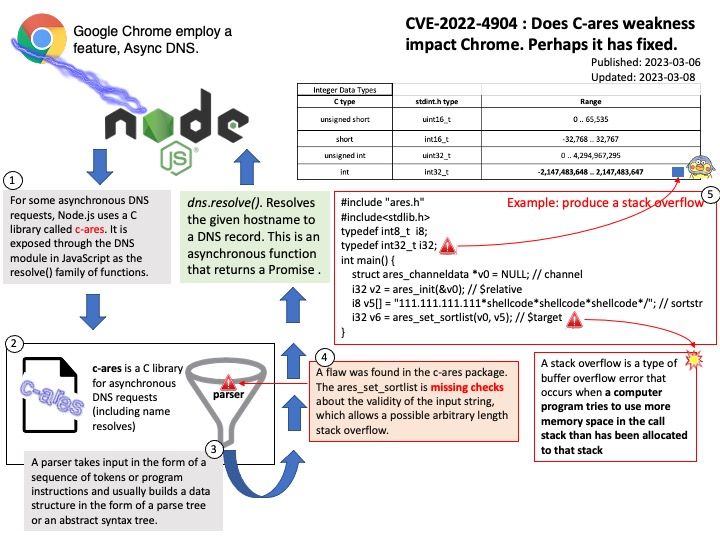
Background:For some asynchronous DNS requests, Node.js uses a C library called c-ares. It is exposed through the DNS module in JavaScript as the resolve() family of functions. The lookup() function, which is what the rest of core uses, makes use of threaded getaddrinfo(3) calls in libuv.
c-ares is a C library for asynchronous DNS requests (including name resolves)
Vulnerability details: A flaw was found in the c-ares package. The ares_set_sortlist is missing checks about the validity of the input string, which allows a possible arbitrary length stack overflow. This issue may cause a denial of service or a limited impact on confidentiality and integrity.
Official details: Please refer to the url for details – https://www.tenable.com/cve/CVE-2022-4904
Additional: It is a stack overflow, however the risk level (whether it is severity), it depends on the design structure of product when it use. Therefore it is better to follow the recommendation by the product which involves this vulnerability.