Preface:
HTTP/1.1 – The current resource must finish downloading before making another request; each has a delay of one round-trip-time (RTT).
HTTP/2 solves the HOL Blocking problem with multiplexing that uses streams which can be prioritized.
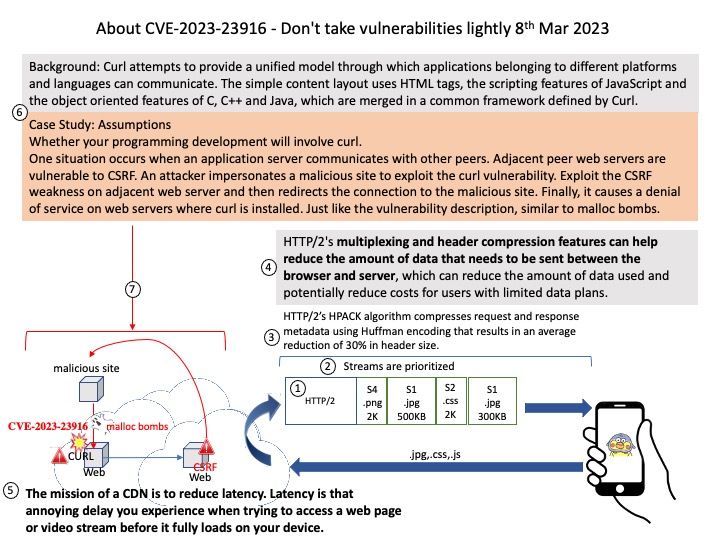
Background: Curl attempts to provide a unified model through which applications belonging to different platforms and languages can communicate. The simple content layout uses HTML tags, the scripting features of JavaScript and the object oriented features of C, C++ and Java, which are merged in a common framework defined by Curl.
Case Study: Assumptions
Whether your programming development will involve curl.
One situation occurs when an application server communicates with other peers. Adjacent peer web servers are vulnerable to CSRF. An attacker impersonates a malicious site to exploit the curl vulnerability. Exploit the CSRF weakness on adjacent web server and then redirects the connection to the malicious site. Finally, it causes a denial of service on web servers where curl is installed. Just like the vulnerability description, similar to malloc bombs.
Vulnerability details: An allocation of resources without limits or throttling vulnerability exists in curl <v7.88.0 based on the “chained” HTTP compression algorithms, meaning that a server response can be compressed multiple times and potentially with different algorithms. The number of acceptable “links” in this “decompression chain” was capped, but the cap was implemented on a per-header basis allowing a malicious server to insert a virtually unlimited number of compression steps simply by using many headers. The use of such a decompression chain could result in a “malloc bomb”, making curl end up spending enormous amounts of allocated heap memory, or trying to and returning out of memory errors.
Official announcement: Please refer to the url for details – https://nvd.nist.gov/vuln/detail/CVE-2023-23916