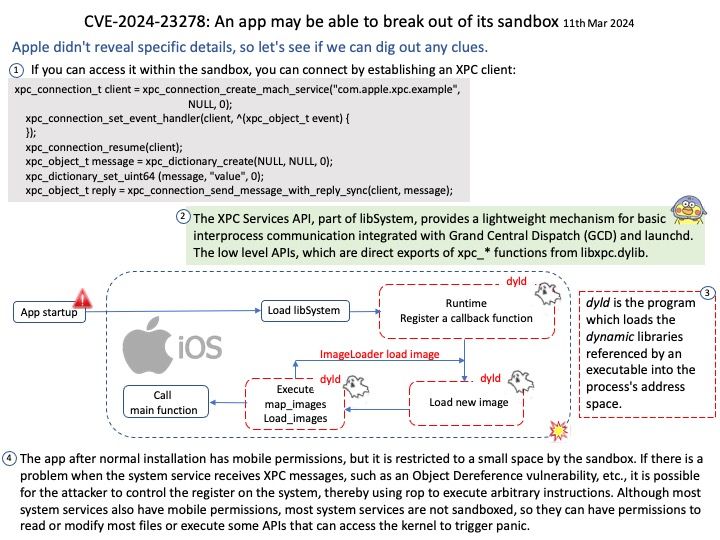
Vulnerability CVE-2024-23278 was released on March 7, 2024. Apple didn’t reveal specific details, so let’s see if we can dig out any clues.
Preface: XPC has a sizeable portion of undocumented functionality, including its implementation (for example, the main project libxpc is closed source). XPC provides a public API at two levels: low-level and Foundation wrappers.
Background: XPC is the enhanced IPC framework used in macOS/iOS. Since its introduction in version 10.7/5.0, its use has exploded. XPC has a fairly large undocumented portion of its functionality, which includes its implementation (the main project libxpc, for example, is closed source). XPC provides public APIs on two levels: the low level and the Foundation wrappers.
Vulnerability details: The issue was addressed with improved checks. This issue is fixed in macOS Ventura 13.6.5, macOS Sonoma 14.4, iOS 17.4 and iPadOS 17.4, watchOS 10.4, iOS 16.7.6 and iPadOS 16.7.6, tvOS 17.4. An app may be able to break out of its sandbox.
Official announcement: Please refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2024-23278