AMD made this announcement on March 12, 2024.
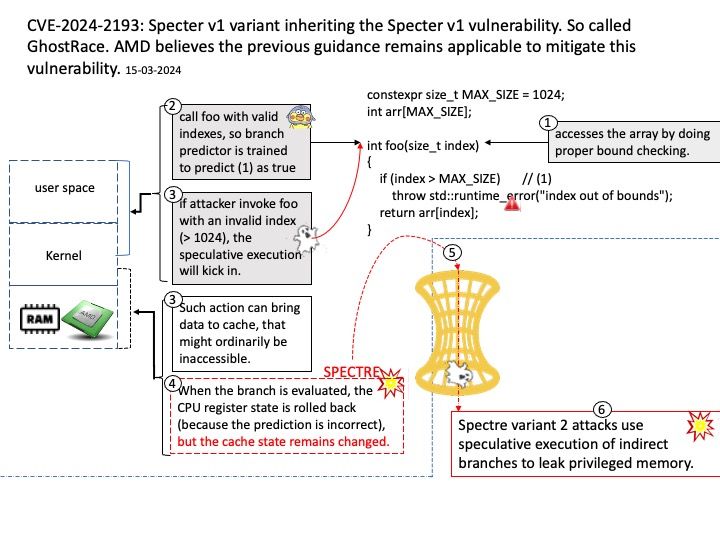
Preface: Spectre variant 1 attacks take advantage of speculative execution of conditional branches, while Spectre variant 2 attacks use speculative execution of indirect branches to leak privileged memory.
Background: Speculative execution improves speed by operating on multiple instructions at once—possibly in a different order than when they entered the CPU. Speculative execution includes instruction or data pre-fetch, branch prediction, or any operation performed speculatively based on the prediction of program/system behavior.
Vulnerability details: A Speculative Race Condition (SRC) vulnerability that impacts modern CPU architectures supporting speculative execution has been discovered. CPU hardware utilizing speculative execution that are vulnerable to Spectre v1 are likely affected. An unauthenticated attacker can exploit this vulnerability to disclose arbitrary data from the CPU using race conditions to access the speculative executable code paths. Security researchers have labeled this variant of the Spectre v1 vulnerability “GhostRace”, for ease of communication.
Official announcement: Please refer to the following link for details –
CPU hardware utilizing speculative execution may be vulnerable to speculative race conditions – https://www.kb.cert.org/vuls/id/488902
AMD official article – https://www.amd.com/en/resources/product-security/bulletin/amd-sb-7016.html