Preface: In this rushed, demanding digital world, people don’t think about what the back-end platform or its design is. Therefore, vulnerability management actually relies on vendors and software developers.
Background: Ruby on Rails is forming a niche as it is used by millions of websites, which includes well-known companies like Github, Shopify, Airbnb, Fiverr and more.
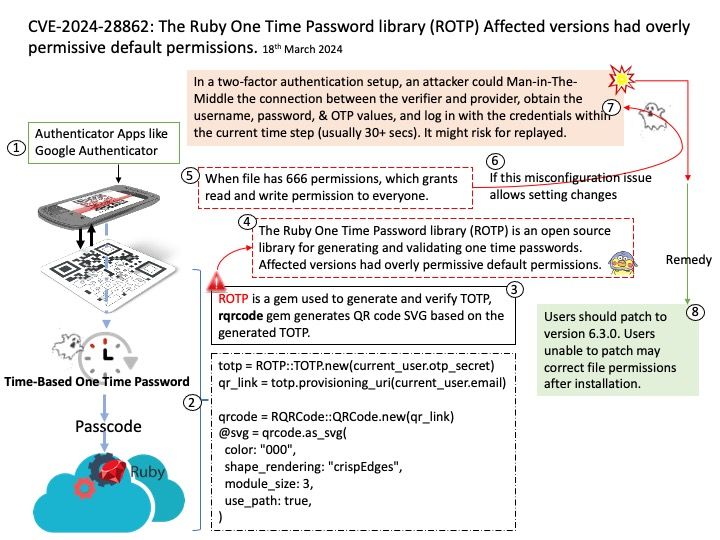
ROTP is a gem used to generate and verify TOTP (Time-Based One Time Password), rqrcode gem generates QR code SVG based on the generated TOTP.
Vulnerability details: The Ruby One Time Password library (ROTP) is an open source library for generating and validating one time passwords. Affected versions had overly permissive default permissions (CWE-276 – Incorrect Default Permissions).
When file has 666 permissions, which grants read and write permission to everyone. This CVE hits this matter.
Workaround: Users should patch to version 6.3.0. Users unable to patch may correct file permissions after installation.
Official announcement: Please refer to the link below for details –https://nvd.nist.gov/vuln/detail/CVE-2024-28862