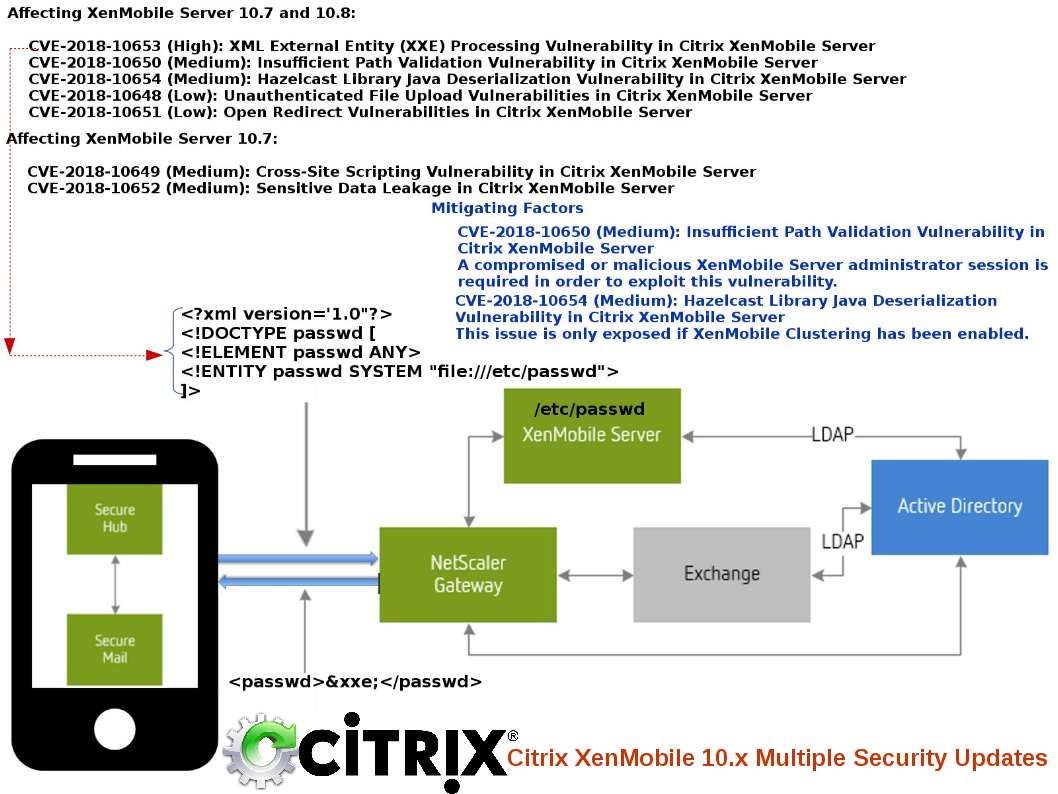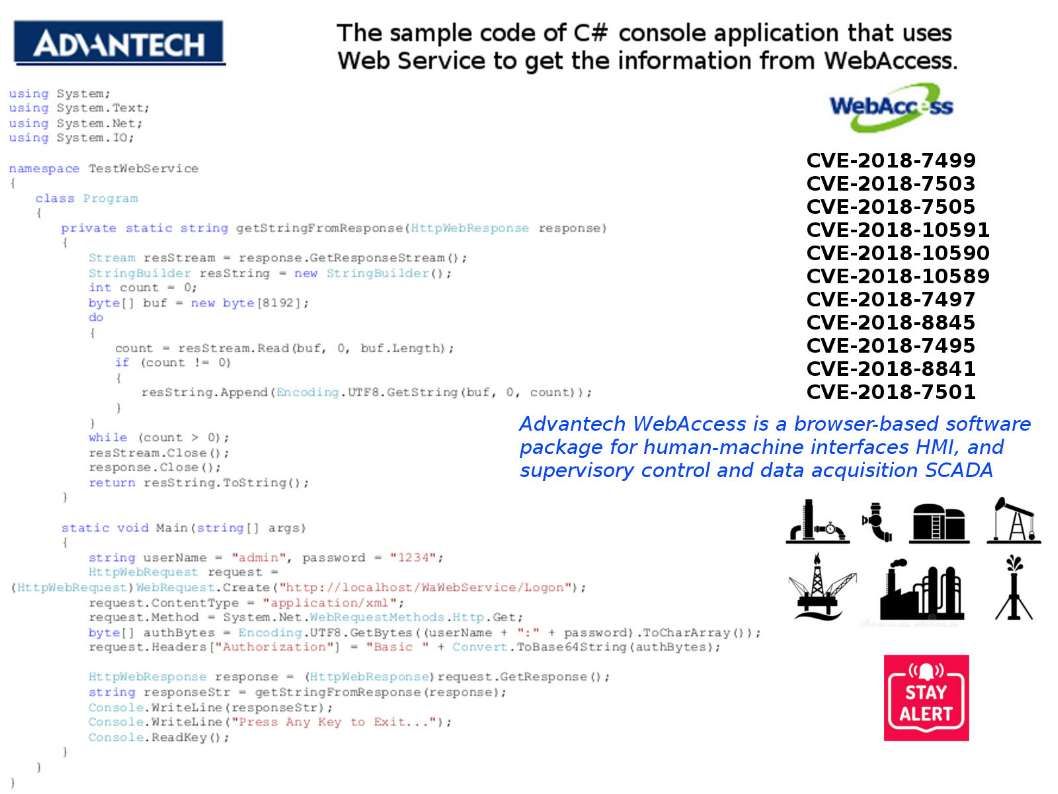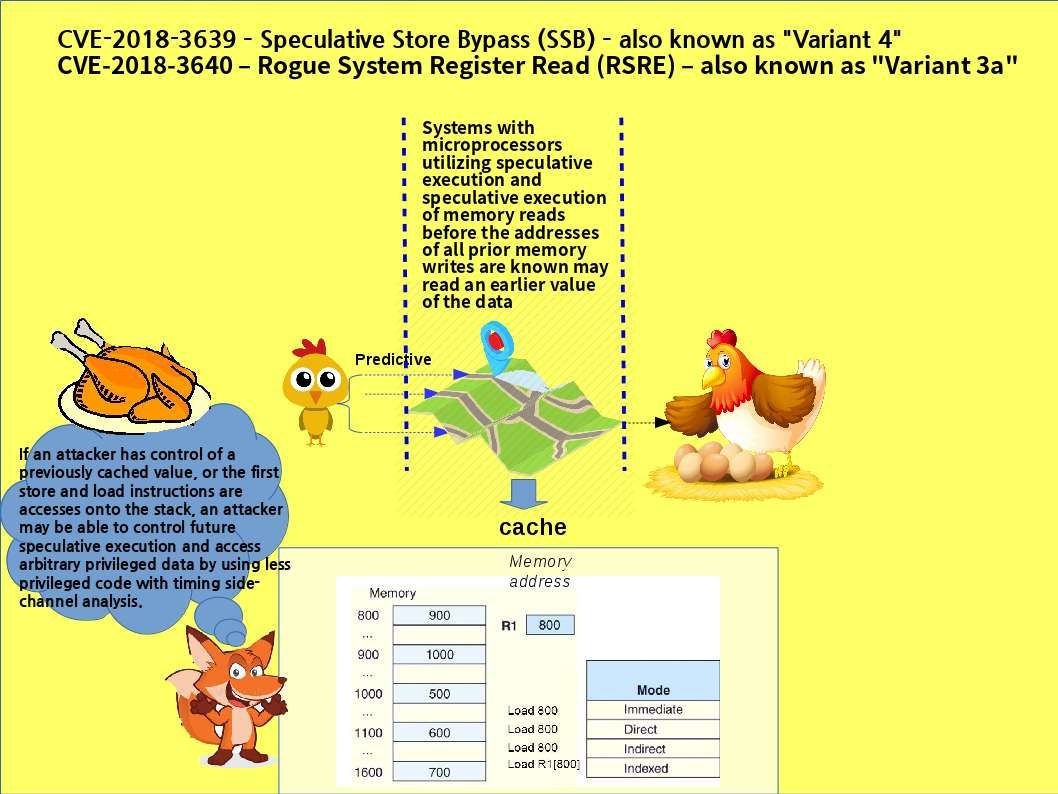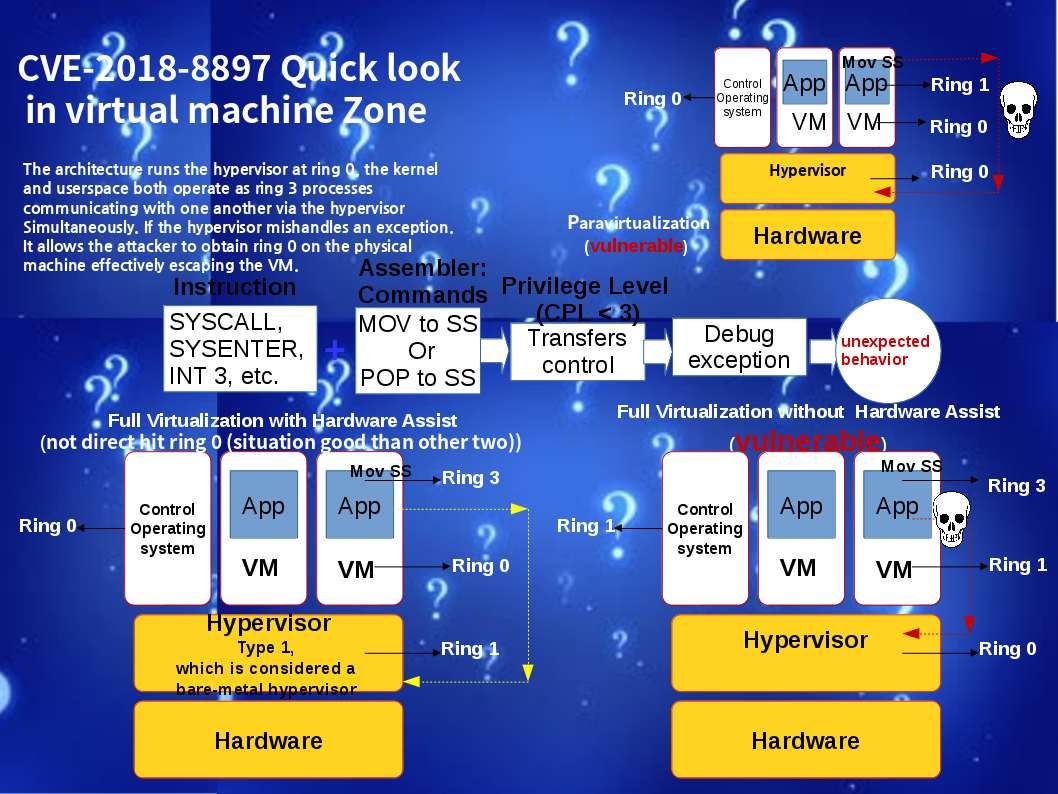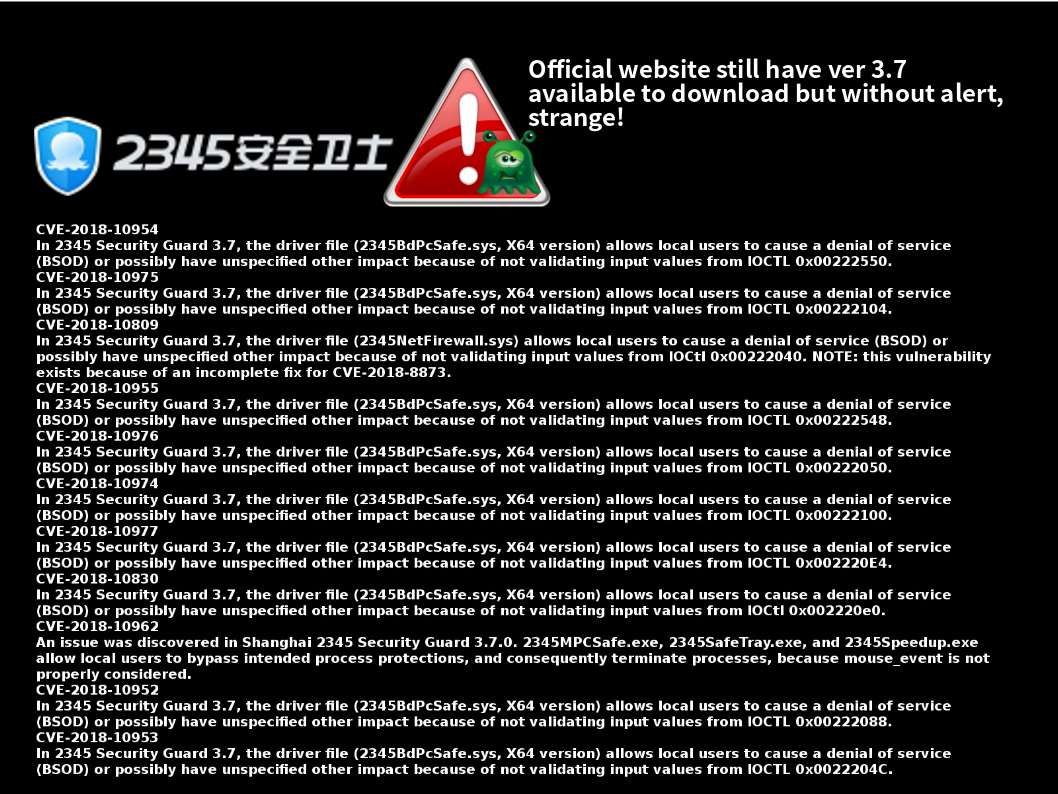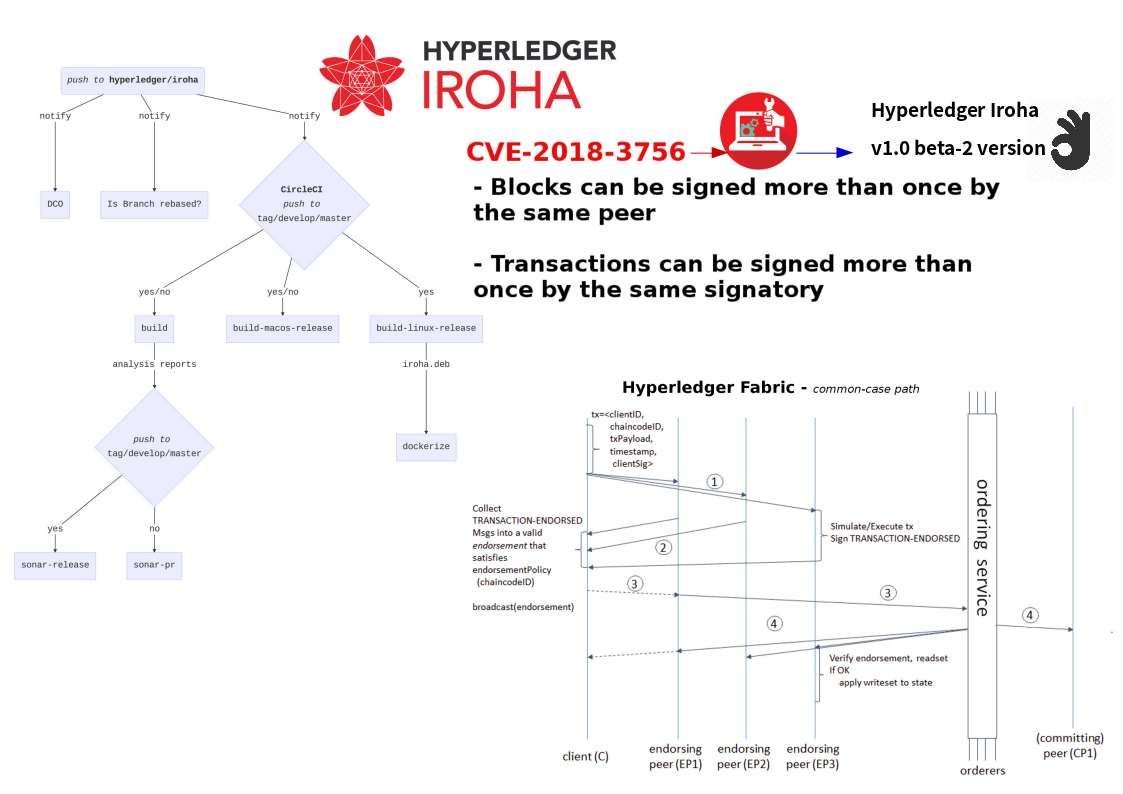
The earlier generation of blockchain technology empower encryption power let the world know his capability. As times goes by people found the design weakness of blockchain technology is the performance of synchoization of the peer nodes. Such design weakness cause double spending vulnerability. The next generation of technology so called HYPERLEDGER. It enhance the design weakness of blockchain. As a result cryptocurrency especially Ethereum relies on Hyperledger Fabric in demand. A blockchain project developed by several Japanese firms including by startup Soramitsu and IT giant Hitachu has been accepted into the Hyperledger blockchain initiative. A fix has been released by Hyperledger IROHA project two weeks ago. Hyperledger Iroha v1.0 beta-2 version is avaliable for download. The reason is that a critical vulnerabilities discovered during the security audit.
On 2017, Cambodia central bank taps Hyperledger Iroha for blockchain settlement. Perhaps they update to beta 2 already.
Should you have interest to know the detail, please refer below:
Cambodia central bank taps Hyperledger Iroha for blockchain settlement – https://www.cryptoninjas.net/2017/04/20/cambodia-central-bank-taps-hyperledger-iroha-blockchain-settlement/
Beta 2 (download): https://github.com/hyperledger/iroha/releases/tag/v1.0.0_beta-2