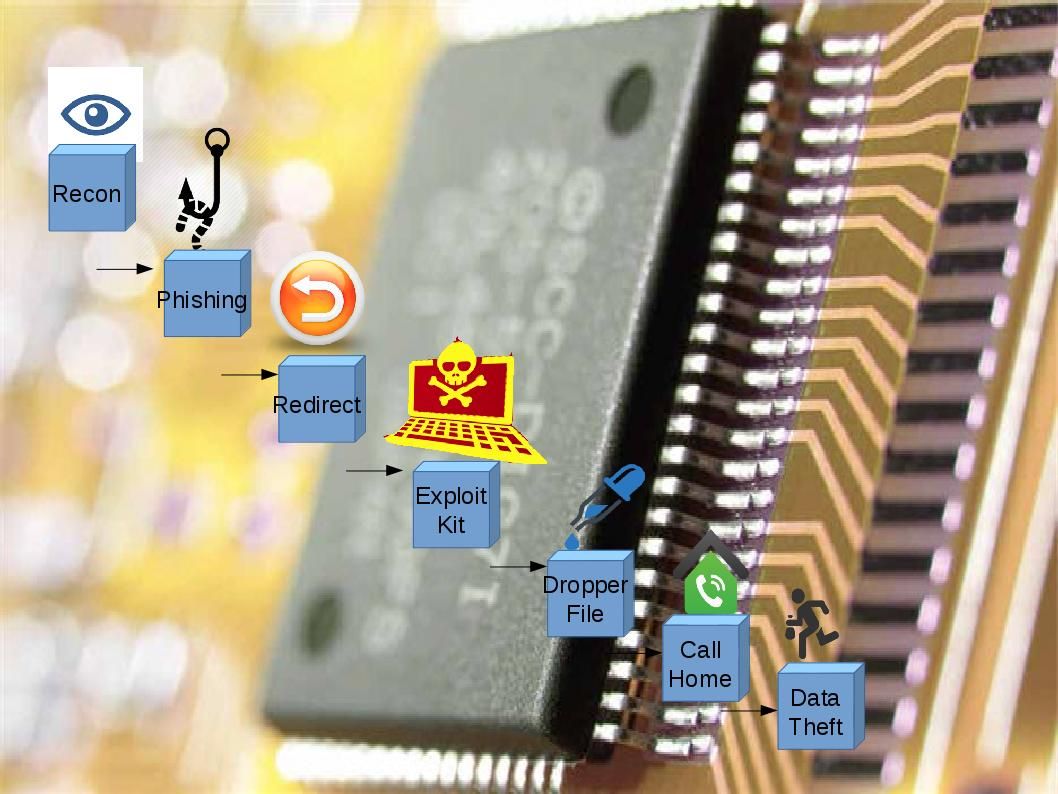
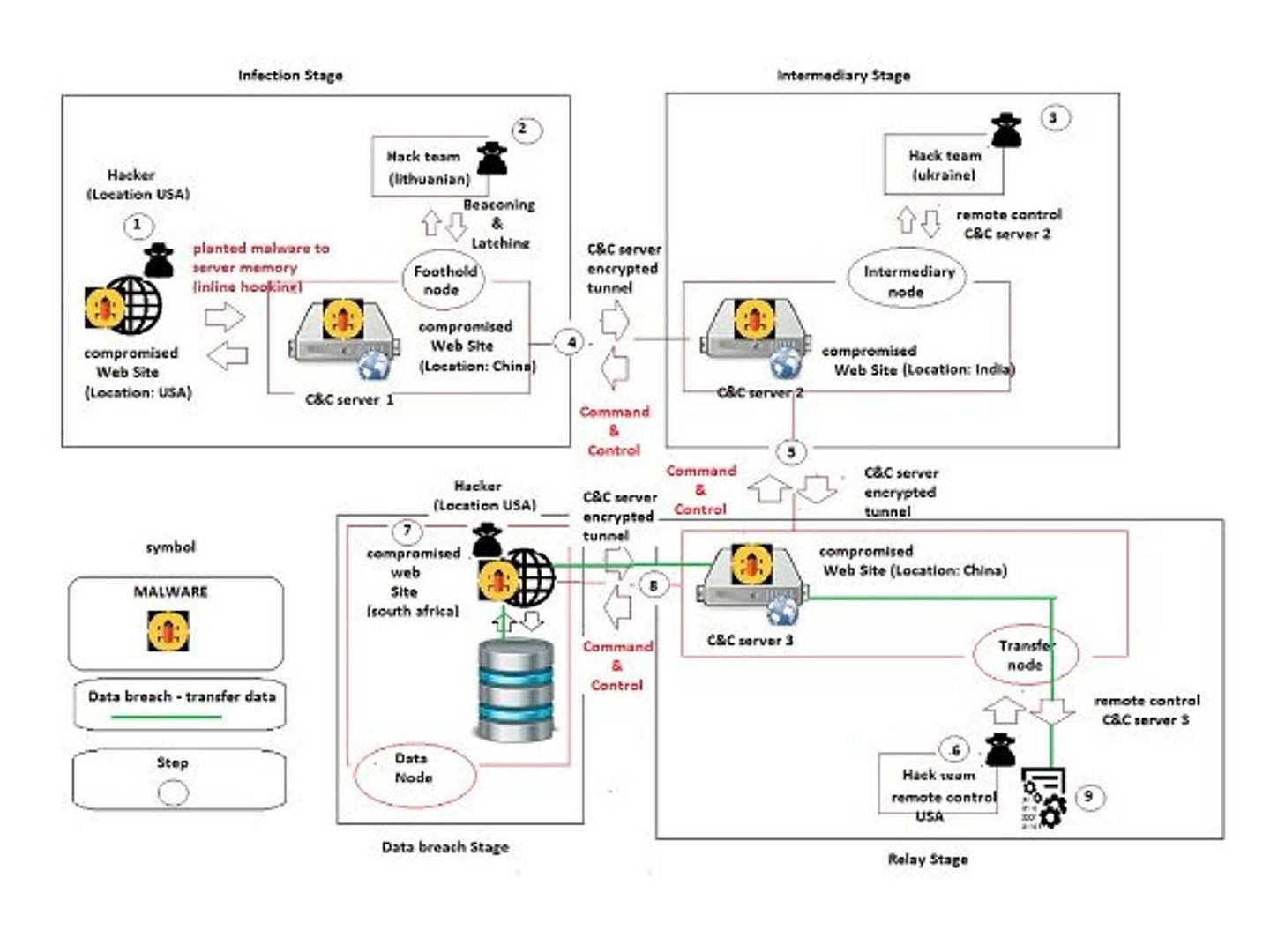
Preface:
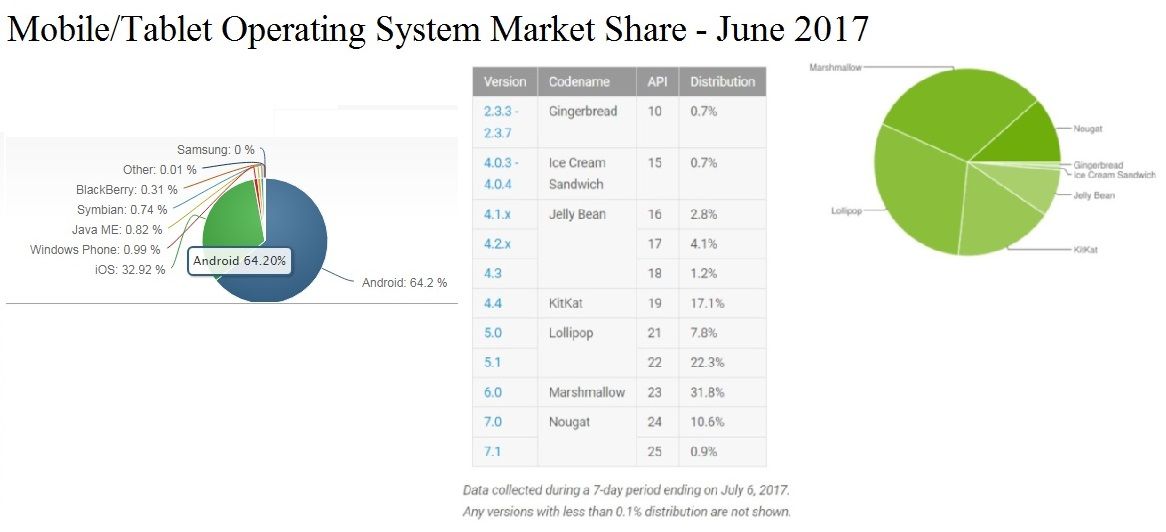
Google Pinyin,QQ,TouchPal,Sogou IME apps has high volume download volume in Google Play store. However user may also be vulnerable to component-hijacking attacks. Do you think whether there are more apps monitor your mobile phone silently!
Start discussion:
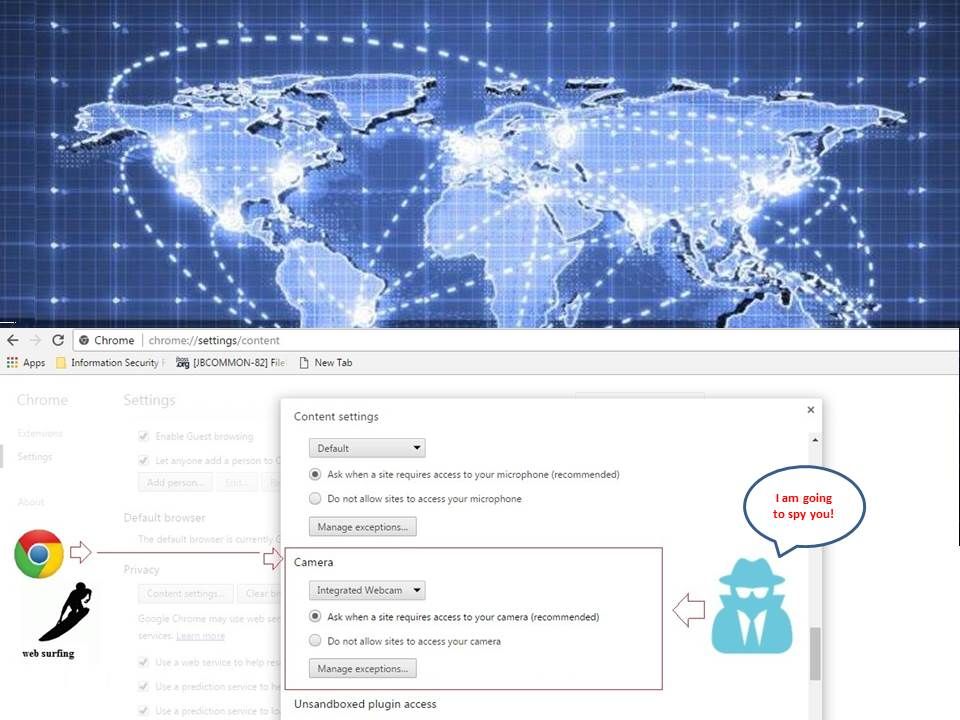
We heard technical terms so called predictive search and auto-correction. Google browser (Chrome) keyboard input feature apply similar technologies.
What is predictive search?
Google’s search feature uses a predictive search algorithm based on popular searches to predict a user’s search query. It requires interconnect with Google system.
What is auto-correction?
Auto correction is a feature in which an application predicts the rest of a word a user is typing. It requires interconnect with Google system.
Reality – existing situation in the market 2017
It looks that above criteria make sense, user are allow to disable this function. If mobile owner forgot to enforce the access permission setting. Seems their personal information will be forward to google during web site visiting. Their goal is going to do the web behavior analytic. As far as I know, the applications like google app, Google Zhuyin input, Google Pinyin input are maintain the following spy able permissions.
Google App – Reads Browser Bookmarks, Knows location by Cell-ID and WiFi, Knows location by GPS signal, Runs on device startup, Reads all SMS messages and records audio on voice calls
Google Zhuyin Input – Records Audio on Voice Calls, Runs on device startup
Google Pinyin Input – Records Audio on Voice Calls, Runs on device startup
MiTalk (China users) – knows location by GPS signal, Received all SMS messages, Records Audio on Voice calls, Knows location by Cell-ID and WiFi, Handles Outgoing calls and Runs on device startup
Attention – critical loophole
In 2015, a group of researcher in Chinese university of Hong Kong (Wenrui Diao, Xiangyu Liu, Zhe Zhou, Kehuan Zhang, Zhou Li) found a vulnerability on Pinyin input. A vulnerability so called cross-app KeyEvent injection (CAKI) attack will be encountered on Google Pinyin input method. The flaw is that it allow 3rd party to harvest entries from the personalized user dictionary of IME through an ostensibly innocuous app only asking for common permissions.
Android CAKI vulnerability
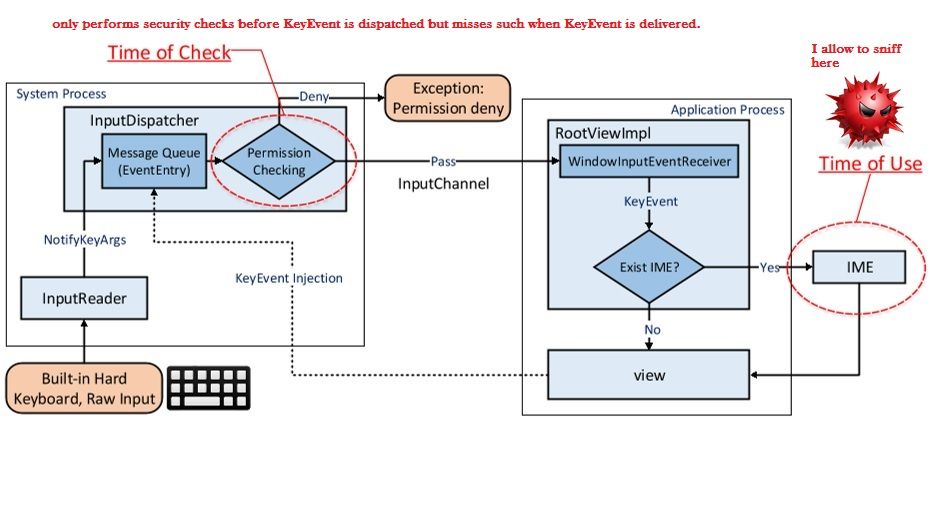
Speculation:
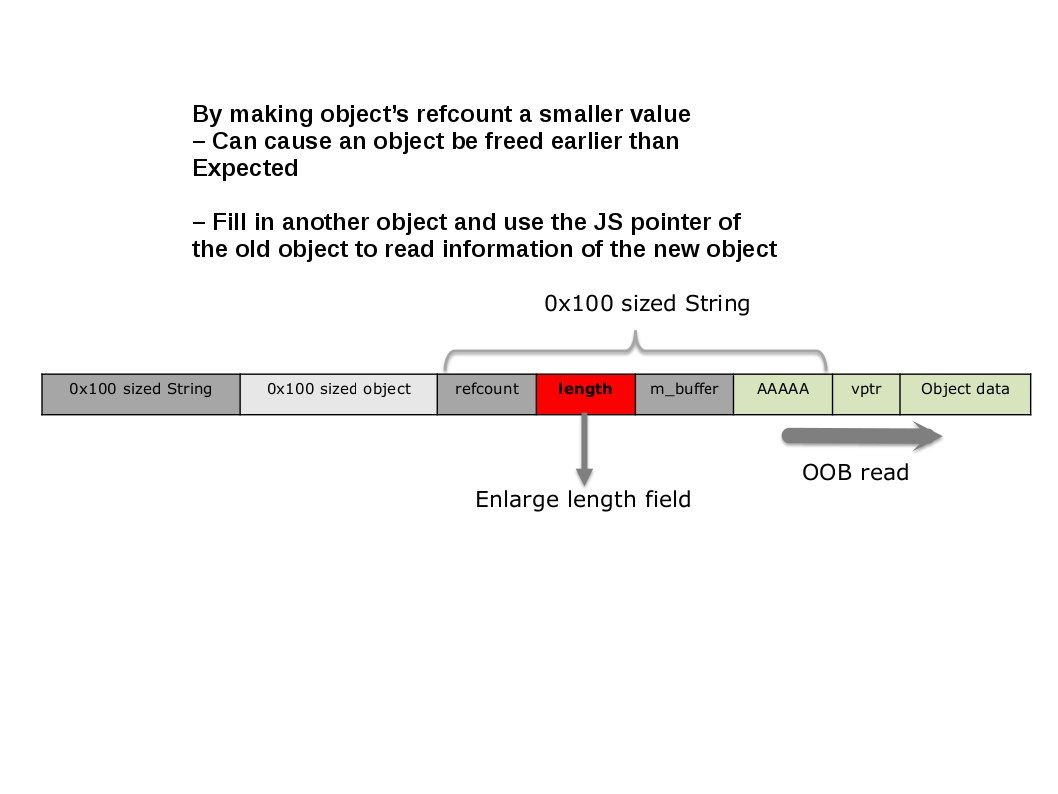
We keep track of android vulnerabilities so far. I note with concerns of CVE-2016-9651. This vulnerability is allow to collect the Invisible Private Property on your android phone. Details is shown as below:
Get all properties of an special object by d8 shell command
d8> var specialObject = new Error("test");
d8> var ownNames = Object.getOwnPropertyNames(specialObject);
d8> var ownSymbols = Object.getOwnPropertySymbols(specialObject);
d8> var ownKeys = ownNames.concat(ownSymbols)
d8> ownKeys
["stack", "message"] ---------> all public properties got by normal JavaScript
d8> %DebugPrint(specialObject)
DebugPrint: 0x3058e8cd: [JS_ERROR_TYPE]
- map = 0x53d0945d [FastProperties]
- prototype = 0x2560b9e1
- elements = 0x45384125 <FixedArray[0]> [FAST_HOLEY_SMI_ELEMENTS]
- properties = { ---------> all properties got by DebugPrint
#stack: 0x453d012d <AccessorInfo> (accessor constant)
#message: 0x453bb18d <String[4]: test> (data field at offset 0)
0x453859f1 <Symbol: stack_trace_symbol>: 0x3058e9c1 <JS Array[6]> (data field at offset 1) ---------> private property
}
If above flaw co-exists with this vulnerability. Sounds like a prefect surveillance backdoor allow 3rd to collect the information of your android phone. As a matter of fact, the surveillance program or cyber espionage keep track of our mobile activities daily. If such action is collected by your government for crime prevention purpose or big data foundation framework. From certain point of view, we have no doubt to say no. However, who can say how much is the value your personal privacy on your mobile phone?
Reference:
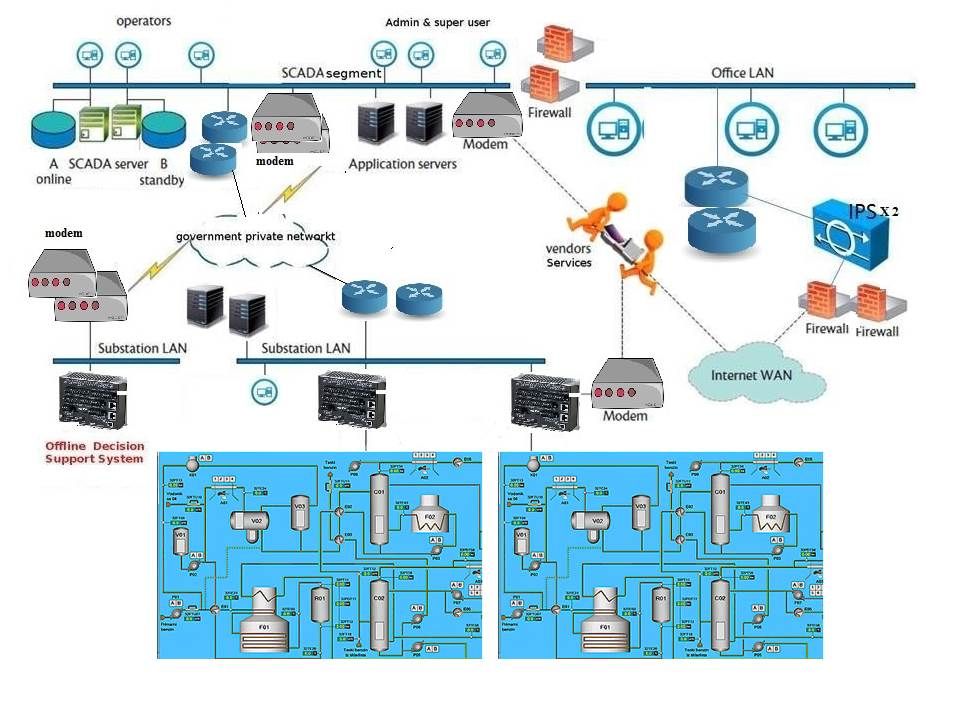
Mobile phone applications – access permission component
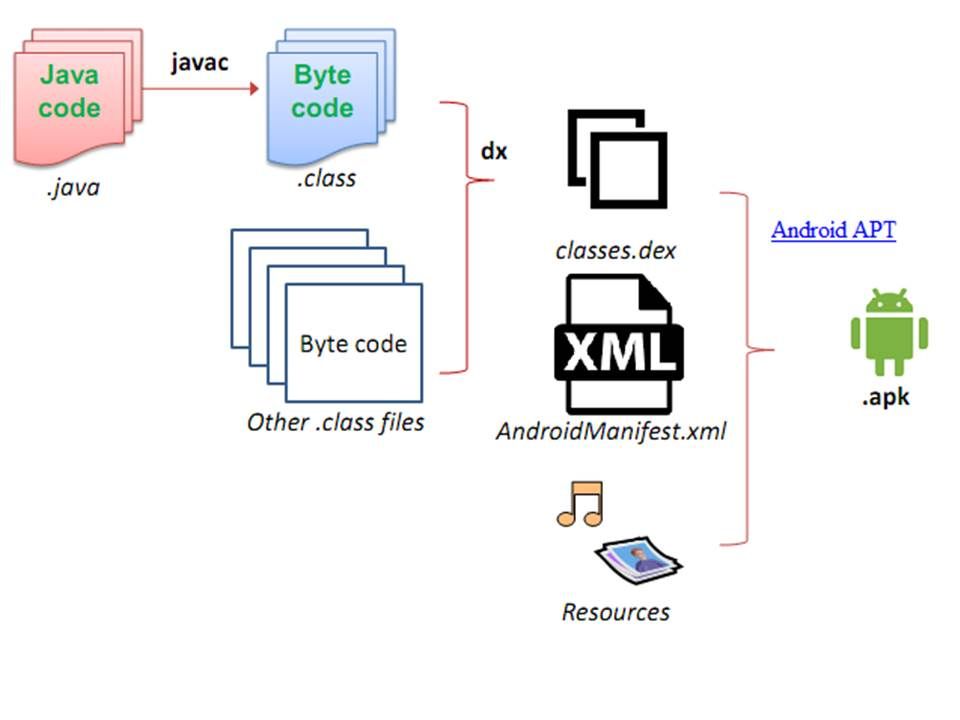
Application must have an AndroidManifest.xml file in its root directory. The manifest file provides essential information about your app to the Android system, which the system must have before it can run any of the app’s code. Manifest file capable declares the permissions (see below) that the application must have in order to access protected parts of the API and interact with other applications. It also declared the permissions that others are required to have in order to interact with the application components.
Sample – Manifest file capable declares the permissions
<?xml version="1.0" encoding="utf-8"?>
<manifest xmlns:android="http://schemas.android.com/apk/res/android"
package="com.photoeffect"
android:versionCode="1"
android:versionName="1.0" >
<uses-sdk
android:minSdkVersion="8"
android:targetSdkVersion="18" />
<uses-permission android:name="android.permission.INTERNET" />
<uses-permission android:name="android.permission.ACCESS_FINE_LOCATION" />
<uses-permission android:name="android.permission.ACCESS_LOCATION_EXTRA_COMMANDS" />
<uses-permission android:name="android.permission.ACCESS_COARSE_LOCATION" />
<uses-permission android:name="com.example.towntour.permission.MAPS_RECEIVE" />
<uses-permission android:name="android.permission.ACCESS_NETWORK_STATE" />
<uses-permission android:name="android.permission.CALL_PHONE" />
<uses-permission android:name="android.permission.READ_PHONE_STATE" />
<uses-permission android:name="com.google.android.providers.gsf.permission.READ_GSERVICES" />
Mobile apps like your wife or girlfriend. They are tracing you!