Preface: The Out-of-Band vulnerabilities, also known as OOB, are a series of alternative ways that an attacker uses to exploit a vulnerability that can’t be detected by a traditional request-response interaction.
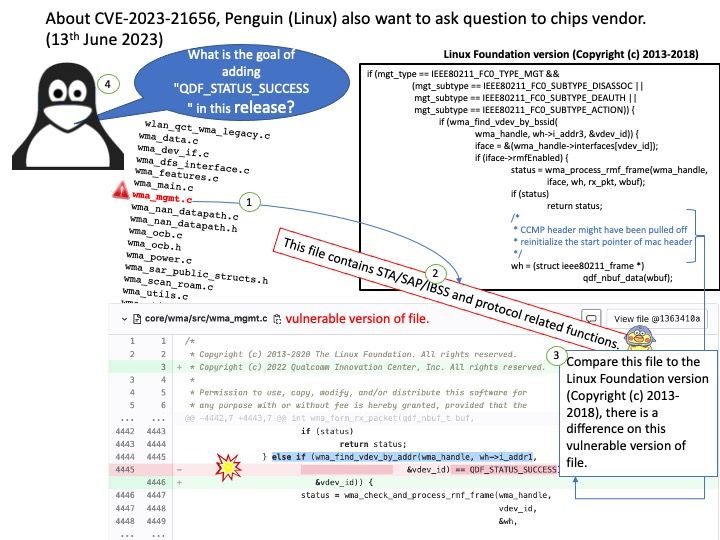
Background: Qualcomm Technologies offers industry leading platforms for wireless networks and products that cover the gamut of device needs. The file (wma_mgmt[.]c) contains STA/SAP/IBSS and protocol related functions.
Ref:
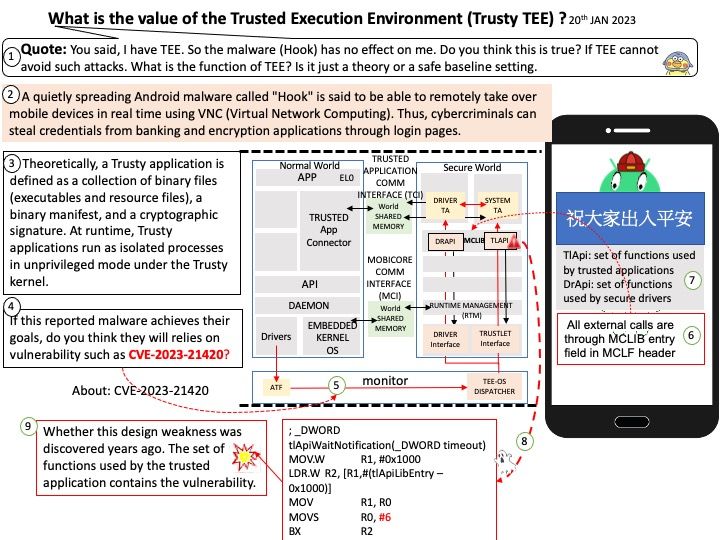
The Independent Basic Service Set (IBSS) is a simple and flexible wireless network configuration designed for situations where there is no centralized access point or other infrastructure in place. It operates by forming an ad hoc, self-contained network with station-to-station traffic flowing directly between devices. This makes IBSS networks effortless to set up and ideal for small groups of users who need a temporary, wireless means of communication without having to rely on any external hardware.
Vulnerability details: CVE-2023-21656 Memory corruption in WLAN HOST while receiving an WMI event from firmware.
Official Announcement: Please see the link for details – https://docs.qualcomm.com/product/publicresources/securitybulletin/june-2023-bulletin.html