Preface: In technical aspect, a Socket[.]IO server can sustain 10,000 concurrent connections. Therefore you can build a chat experience and using Socket[.]IO as your realtime communication solution. But if you want chat users to receive push notifications when they’re not actively using the app, Socket[.]IO can’t help, as it relies on a persistent socket connection.
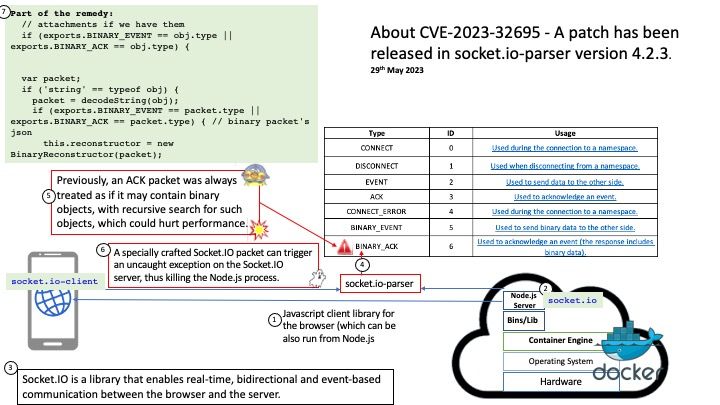
Background: Socket[.]IO is a library that enables real-time, bidirectional and event-based communication between the browser and the server.
A socket[.]io encoder and decoder written in JavaScript complying with version 4 of socket[.]io-protocol. Used by socket[.]io and socket[.]io-client.
In addition, a socket[.]io-parser has included. A socket.io encoder and decoder written in JavaScript complying with socket[.]io-protocol. Used by socket[.]io and socket[.]io-client.
Ref:socket-io[.] client is the code for the client-side implementation of socket[.]io[.] That code may be used either by a browser client or by a server process that is initiating a socket[.]io connection to some other server (thus playing the client-side role in a socket[.]io connection).
Vulnerability details: socket[.]io parser is a socket.io encoder and decoder written in JavaScript complying with version 5 of socket[.]io-protocol.
Potential impact: A specially crafted Socket[.]IO packet can trigger an uncaught exception on the Socket[.]IO server, thus killing the Node[.]js process.
Solution: A patch has been released in version 4.2.3.
Official announcement: For details, please refer to the link – https://nvd.nist.gov/vuln/detail/CVE-2023-32695