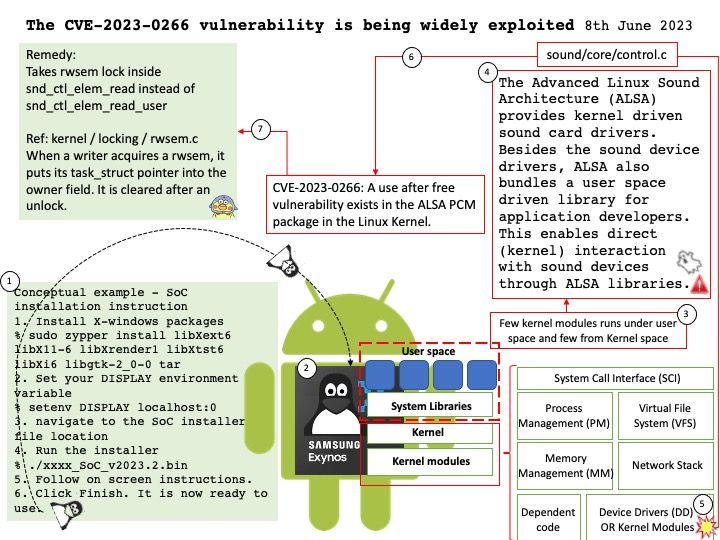
Preface: The Advanced Linux Sound Architecture (ALSA) provides kernel driven sound card drivers.
Besides the sound device drivers, ALSA also bundles a user space driven library for application developers. This enables direct (kernel) interaction with sound devices through ALSA libraries.
Background: Exynos, formerly Hummingbird, is a series of ARM-based system-on-chips developed by Samsung Electronics’ System LSI division and manufactured by Samsung Foundry.
Conceptual example – SoC installation instruction
- Install X-windows packages
% sudo zypper install libXext6 libX11-6 libXrender1 libXtst6 libXi6 libgtk-2_0-0 tar - Set your DISPLAY environment variable
% setenv DISPLAY localhost:0 - navigate to the SoC installer file location
- Run the installer
% [.]/xxxx_SoC_v2023[.]2[.]bin - Follow on screen instructions.
- Click Finish. It is now ready to use.
Vulnerability details: A use after free vulnerability exists in the ALSA PCM package in the Linux Kernel. SNDRV_CTL_IOCTL_ELEM_{READ|WRITE}32 is missing locks that can be used in a use-after-free that can result in a priviledge escalation to gain ring0 access from the system user.
Solution: Samsung Mobile is releasing a maintenance release for major flagship models as part of monthly Security Maintenance Release (SMR) process. This SMR package includes patches from Google and Samsung.
For details, please refer to link – https://security.samsungmobile.com/securityUpdate.smsb
Official announcement: For details, please refer to the following links
https://nvd.nist.gov/vuln/detail/CVE-2023-0266
https://www.hkcert.org/tc/security-bulletin/samsung-products-multiple-vulnerabilities_20230607