Preface: c-ares is a C language implementation of asynchronous request DNS. When using c-ares, you usually only need to reference the ares.h header file, and the related header files of the library are included.
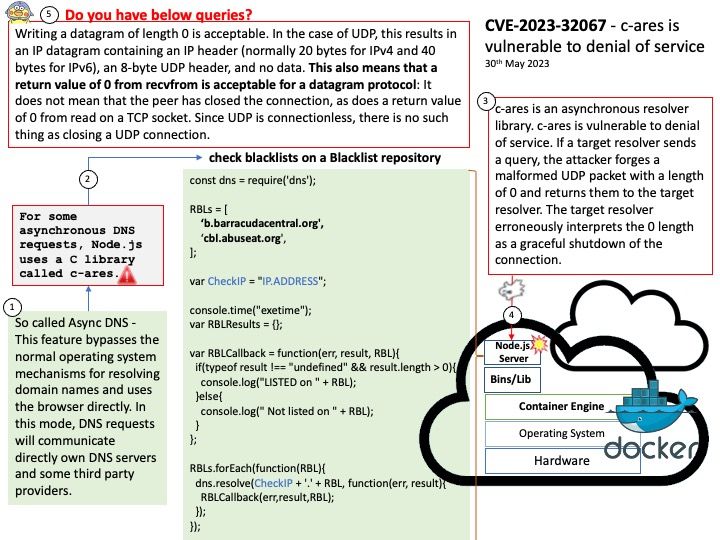
Background: For some asynchronous DNS requests, Node[.]js uses a C library called c-ares.
So called Async DNS – This feature bypasses the normal operating system mechanisms for resolving domain names and uses the browser directly. In this mode, DNS requests will communicate directly own DNS servers and some third party providers.
Vulnerability details: c-ares is an asynchronous resolver library. c-ares is vulnerable to denial of service. If a target resolver sends a query, the attacker forges a malformed UDP packet with a length of 0 and returns them to the target resolver. The target resolver erroneously interprets the 0 length as a graceful shutdown of the connection. This issue has been patched in version 1.19.1.
According to the technical aspect of UDP packet with a length of 0 matter. Do you have below queries?
Writing a datagram of length 0 is acceptable. In the case of UDP, this results in an IP datagram containing an IP header (normally 20 bytes for IPv4 and 40 bytes for IPv6), an 8-byte UDP header, and no data. This also means that a return value of 0 from recvfrom is acceptable for a datagram protocol: It does not mean that the peer has closed the connection, as does a return value of 0 from read on a TCP socket. Since UDP is connectionless, there is no such thing as closing a UDP connection.
Official announcement: For details, please refer to the link – https://nvd.nist.gov/vuln/detail/CVE-2023-32067