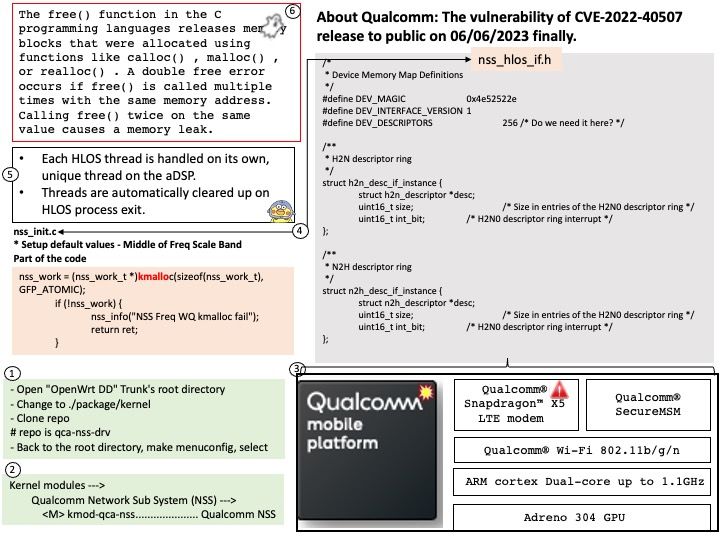
Preface: Double free errors occur when free() is called more than once with the same memory address as an argument. Calling free() twice on the same value can lead to memory leak. When a program calls free() twice with the same argument, the program’s memory management data structures become corrupted and could allow a malicious user to write values in arbitrary memory spaces.
Background: SnapDragon has different processors runn on top of SOC (see below):
Krait CPU — General purpose processor that usually runs android applications.
Adreno GPU — This is largely used for graphics processing like rendering.
Hexagon DSP — Hexagon specially designed for multi-media acceleration, this helps CPU to offload the task to DSP and save energy and thereby offering optimum performance.
Vulnerability details: Memory corruption due to double free in Core while mapping HLOS address to the list.
The vulnerability release to public on 06/06/2023. The announcement can be read at qualcomm.com – https://www.qualcomm.com/company/product-security/bulletins/june-2023-bulletin
This vulnerability has been identified as CVE-2022-40507 since 09/12/2022. The vendor did not release technical details.
How to observe memory allocation in Linux kernel?
Generate the skeleton for the task named 1-mem and browse the contents of the mem[.]c file. Observe the use of kmalloc() call for memory allocation.
- Compile the source code and load the mem[.]ko module using insmod.
- View the kernel messages using the dmesg command.
- Unload the kernel module using the rmmod mem command.