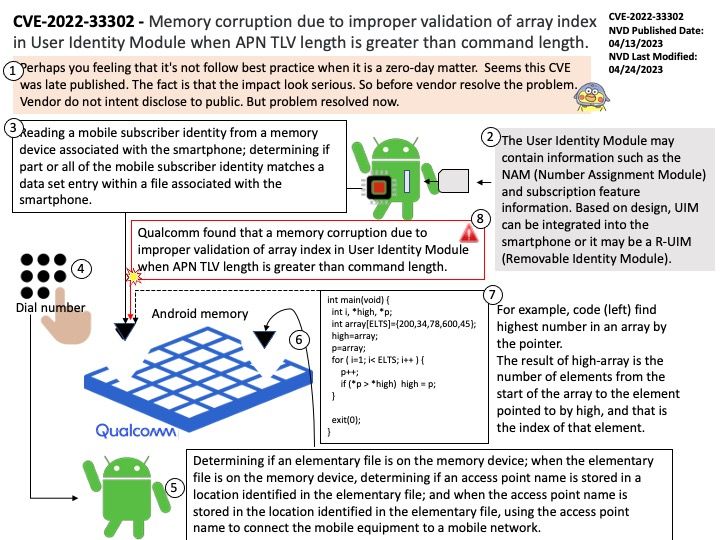
Preface: Perhaps you feeling that it’s not follow best practice when it is a zero-day matter. Seems this CVE was late published. The fact is that the impact look serious. So before vendor resolve the problem. Vendor do not intent disclose to public. But problem resolved now.
Background: The User Identity Module may contain information such as the NAM (Number Assignment Module) and subscription feature information. Based on design, UIM can be integrated into the smartphone or it may be a R-UIM (Removable Identity Module).
Refer to vendor design mechanism, Reading a mobile subscriber identity from a memory device associated with the smartphone; determining if part or all of the mobile subscriber identity matches a data set entry within a file associated with the smartphone.
For example, a program assists find highest number in an array by the pointer. As a result, the result of high-array is the number of elements from the start of the array to the element pointed to by high, and that is the index of that element.
Ref: What is a Function Pointer? Function Pointers are pointers, i.e. variables, which point to an address of a function. The running programs get a certain space in the main memory. Both, the executable compiled program code and the used variables, are put inside this memory.
Vulnerability details: Qualcomm found that a memory corruption due to improper validation of array index in User Identity Module when APN TLV length is greater than command length.
Official details: Please refer to link – https://nvd.nist.gov/vuln/detail/CVE-2022-33302