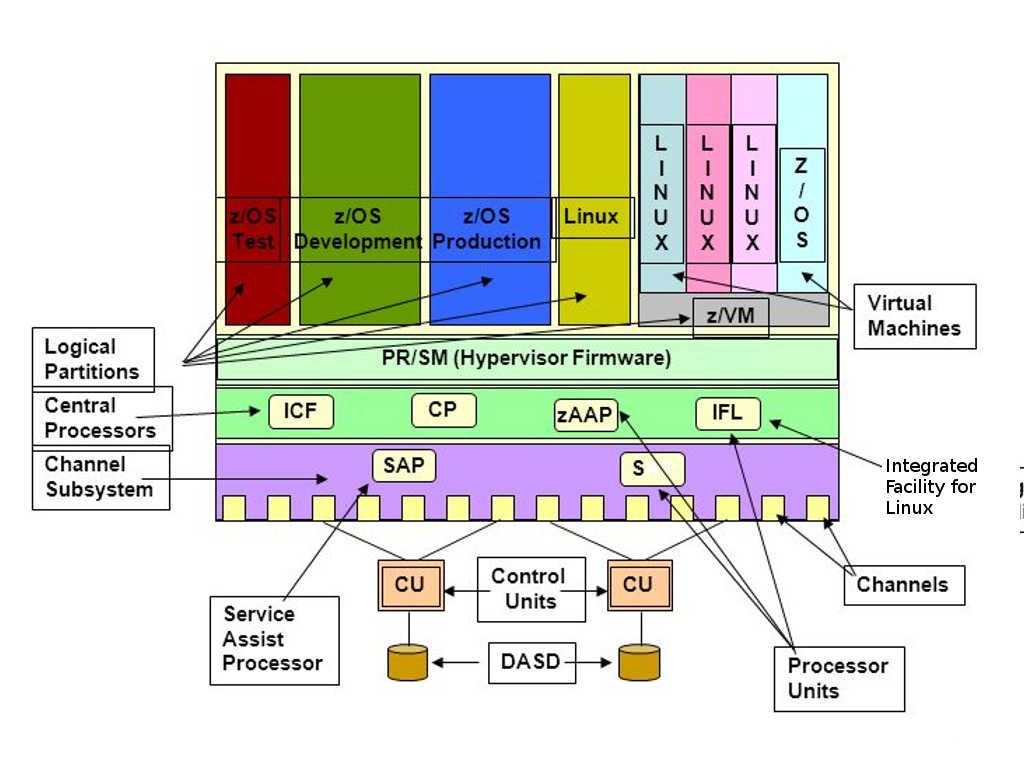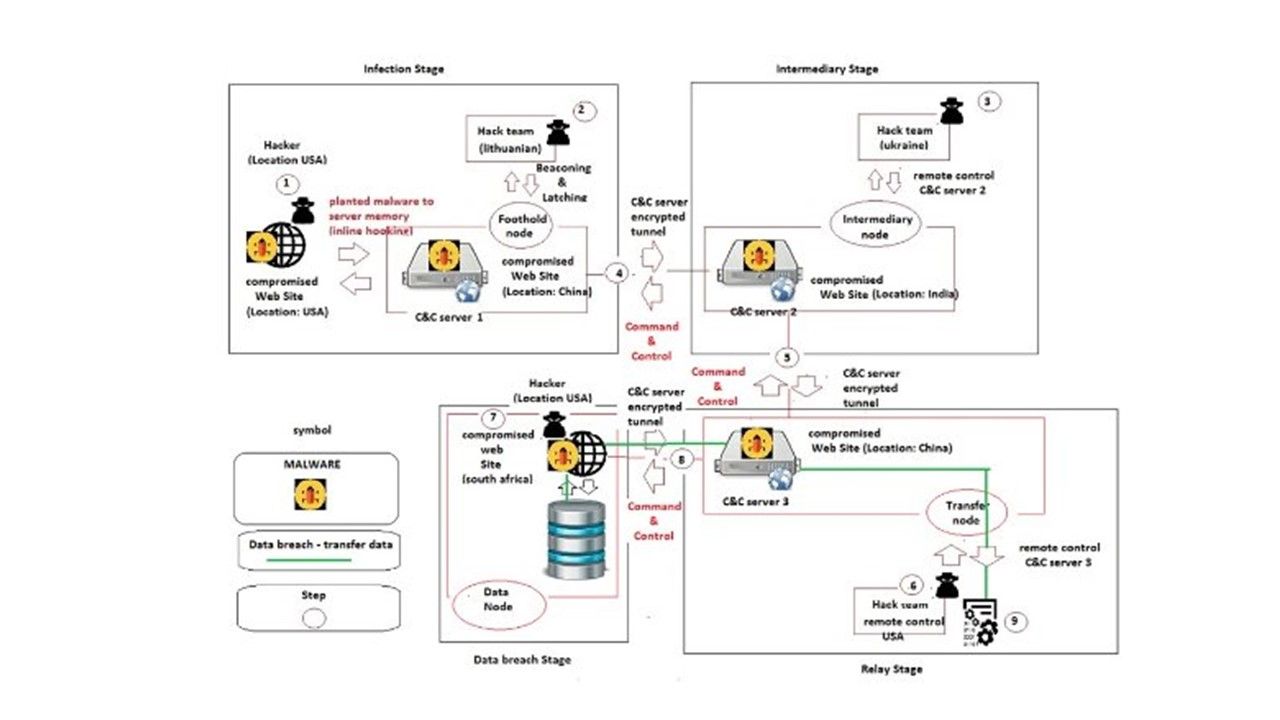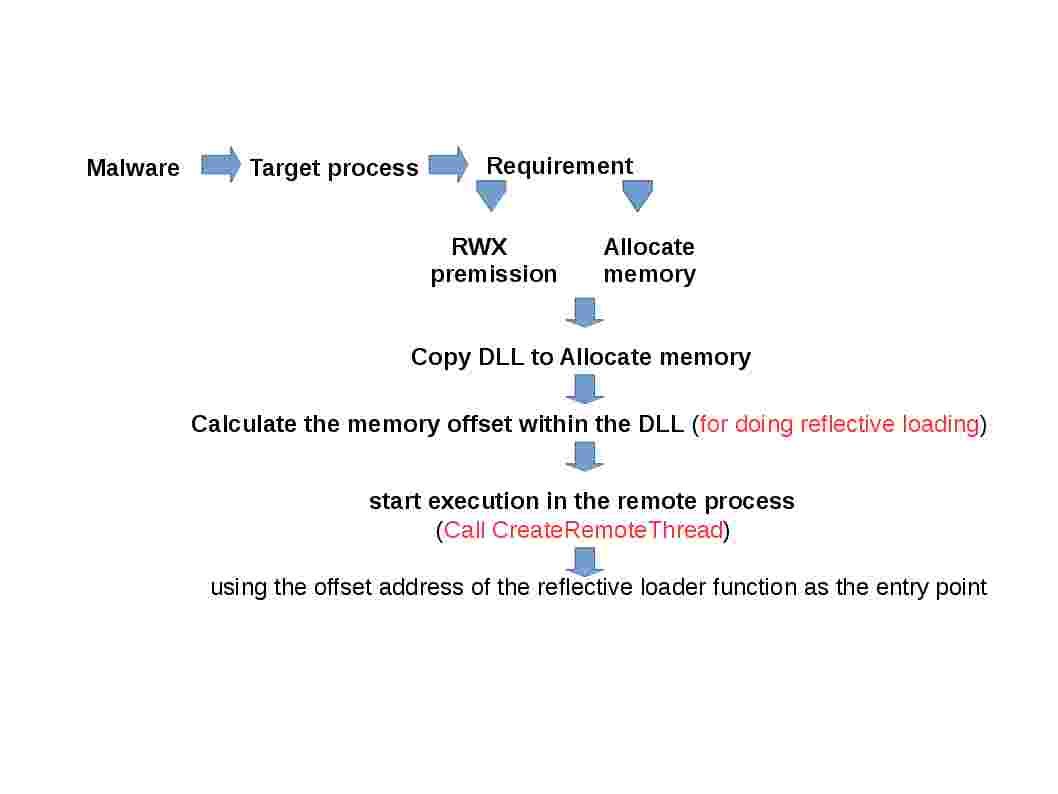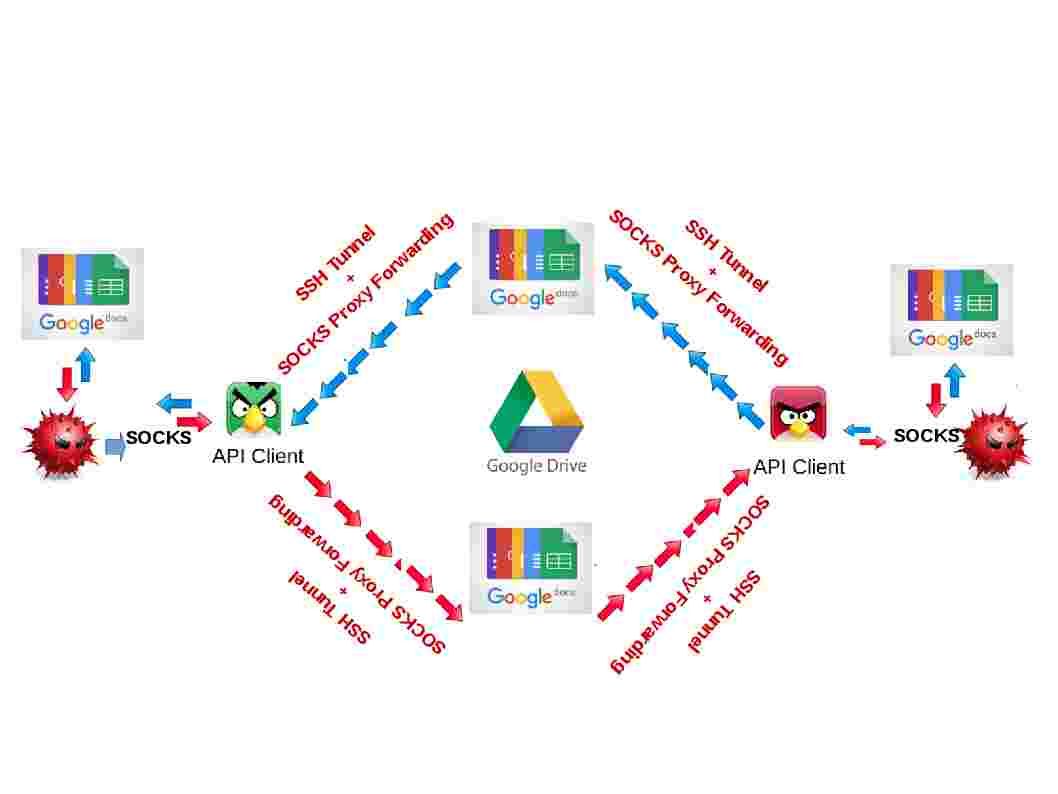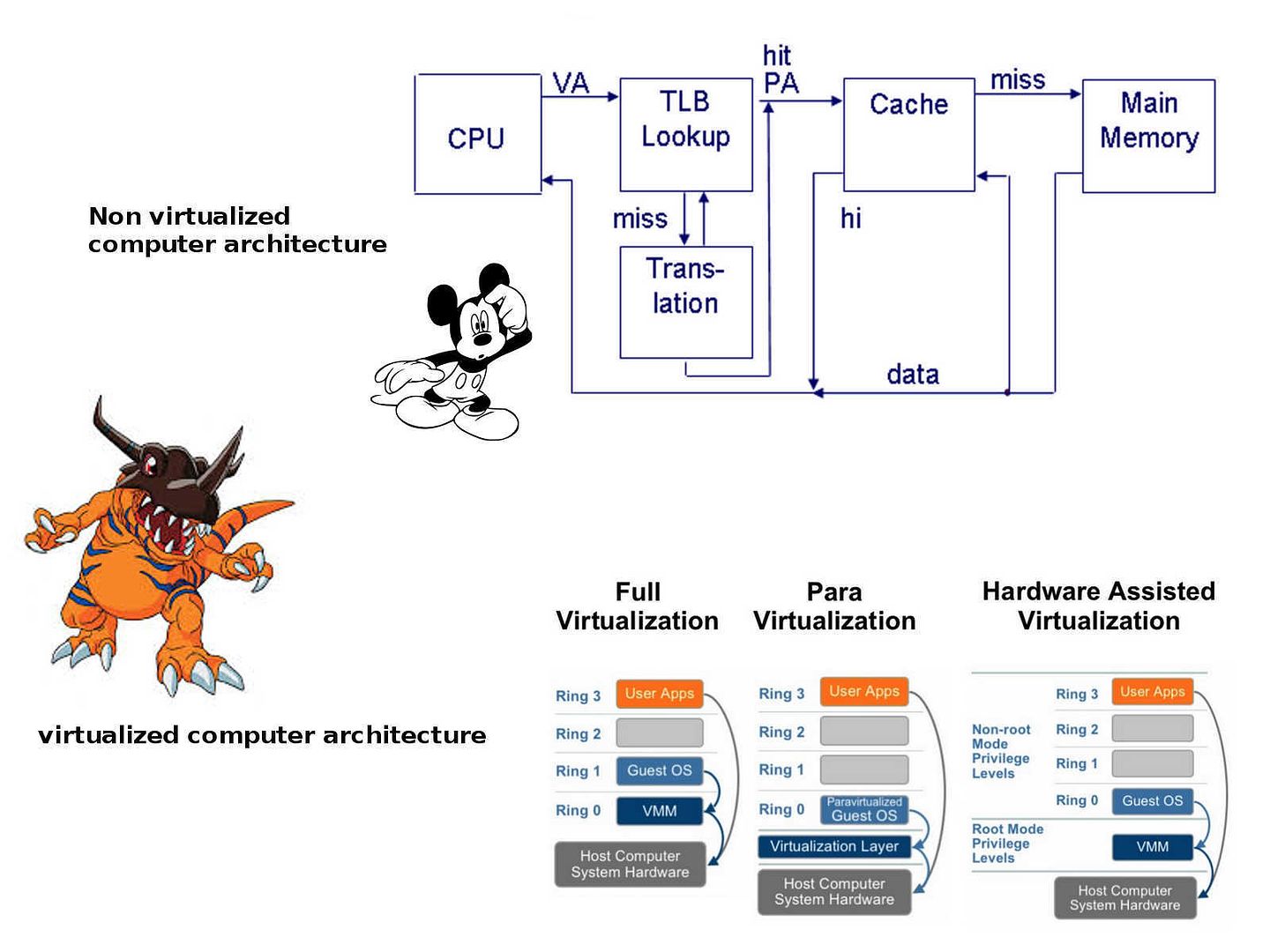
The trend in IT world running into virtual world nowadays. Even though your mobile phone operation system is run on top of virtual machine. The memory resources utilization from tradition static to dynamic since virtual machine architecture founded. Security experts worries about infiltration of malware on virtual machine. A mitigation step introduce on VMware since 2014. The system designer conducted a technology alleged address space layout randomization. As a result it avoid malware implant to kernel since no living place for the malware alive (see below – a statement on technical article point out that how ASLR bring in the value)
The VMware ESXi kernel uses an address space layout randomization (ASLR) methodology to provide random and unpredictable addresses for user-mode applications, drivers, libraries and other executable components. This is a significant security benefit because of the way ASLR thwarts malware looking to take advantage of memory-based exploits. The malware would not have a known address to use as a vector for the exploit because of the randomization.
As times goes by, ASLR not even is the assistance of virtual machine designer. On the other hand, he will become a killer to kill his master. But this fact is not a news today. Regarding to the technology expertise experimental studies, it is possible to execute a attack on kernel side through malicious Java application. The method is a kind of side-channel attack (side-channel attacks) and based on the definition of indirect addresses to which had previously been handling when traversing page tables memory processor unit MMU (Memory Management Unit) in the translation of virtual memory addresses to physical memory addresses. Since cache CPU general and it is recognized as an active application or activity the MMU, then by evaluating differences in data access time before and after resetting the cache (the attack variety “EVICT + TIME”) can with high probability to choose the address and able to detect the locations since it is under the operation of memory management unit.
By breaking ASLR, an attacker will know where code executes, and prepare an attack that targets the same area of the memory, stealing sensitive information stored in the computer’s memory.
The vulnerability channel found on web browser announced by Professor of Computer Science at Cornell Tech on Jan 2016.
When attacking browsers, may be able to insert arbitrary objects into the victim’s heap. Let’s focus on web browser design fundamental.
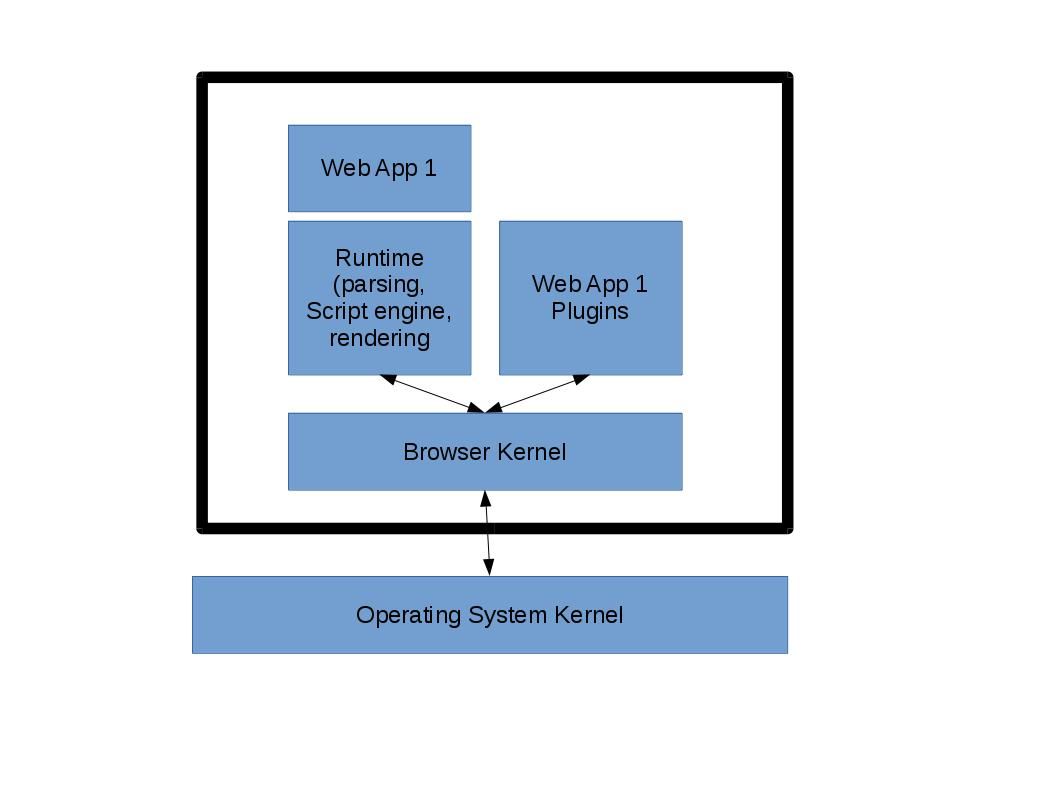
Web applications communicate with each other through system calls to the browser kernel. As we know, web applications exist in separate processes owned by the browser kernel, they are prohibited from communicating with each other, except through the browser kernel.
However Plugins are less reliable than browsers.
However Plugins are less reliable than browsers
As a matter of fact, Java script is the helper of ASLR vulnerability. Sounds like java-script is an accomplice. The murderer is plug in application.
But in which situation virtual machine will be compromise of this vulnerability?
From technical point of view hacker engage a cyber attack targets workplace on memory area we understood that it is a malware form style attack. As we know, AMD architecture define a feature named SVM instruction set. AMD virtualization technology, codenamed “Pacifica,” introduces several new instructions and modifies several existing instructions to facilitate the implementation of VMM systems.
The SVM instruction set includes instructions to:
Start execution of a guest (VMRUN)
Save and restore subsets of processor state (VMSAVE,VMLOAD)
Allow guests to explicitly communicate with the VMM (VMMCALL)
Set and clear the global interrupt flag (STGI, CLGI)
Invalidate TLB entries in a specified ASID (INVLPGA)
Read and write CR8 in all processor modes
Secure init and control transfer with attestation (SKINIT)
Remark: Fundamentally, VMMs (Hypervisor) work by intercepting and emulating in a safe manner sensitive operations in the guest (such as changing the page tables, which could give a guest access to memory it is not allowed to access).

As such, you are more free to run on memory address space once AMD-V is enabled in the BIOS (or by the host OS).
Remark: (VERR_SVM_ENABLED)
Below confirmed CVEs looks headaches to virtual machine core designers (VMWARE, VBOX, Hyper-V), right?
- CVE-2017-5925 for Intel processors
- CVE-2017-5926 for AMD processors
- CVE-2017-5927 for ARM processors
- CVE-2017-5928 for a timing issue affecting multiple browsers
Since founded AnC attack (EVICT+TIME), it can detect which locations in the page table pages are accessed during a page table walk performed by the MMU. In the sense that it such a way broken the ASLR feature on virtual machine. The objective of ASLR mainly avoid malware infection on virtual machine. What scenario we can foreseen tomorrow!
Sample: Java code with execute arbitrary memory write
// prepare buffer with address we want to write to
ptrBuf = ""
// fill buffer: length = relative ptr address - buffer start + ptr offset
while (ptrBuf.length < (0x????? - 0x9????? + 0xC)){ptrBuf += "A"}
ptrBuf += addr
// overflow buffer and overwrite the pointer value after buffer
obj.SetText(ptrBuf,0,0)
// use overwritten pointer to conduct memory write of 4 bytes
obj.SetFontName("\xbe\xba\xfe\xca")
// WHAT TO WRITE
alert("Check after write:0x???????? + 0x?