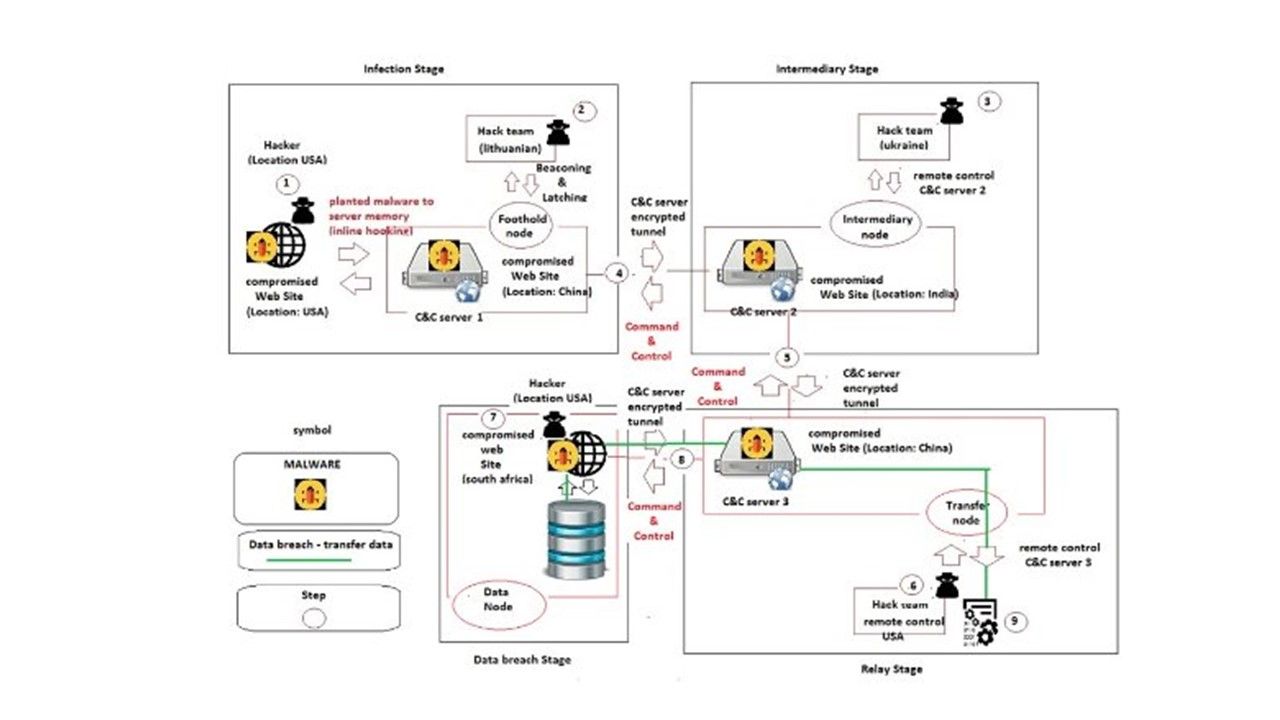
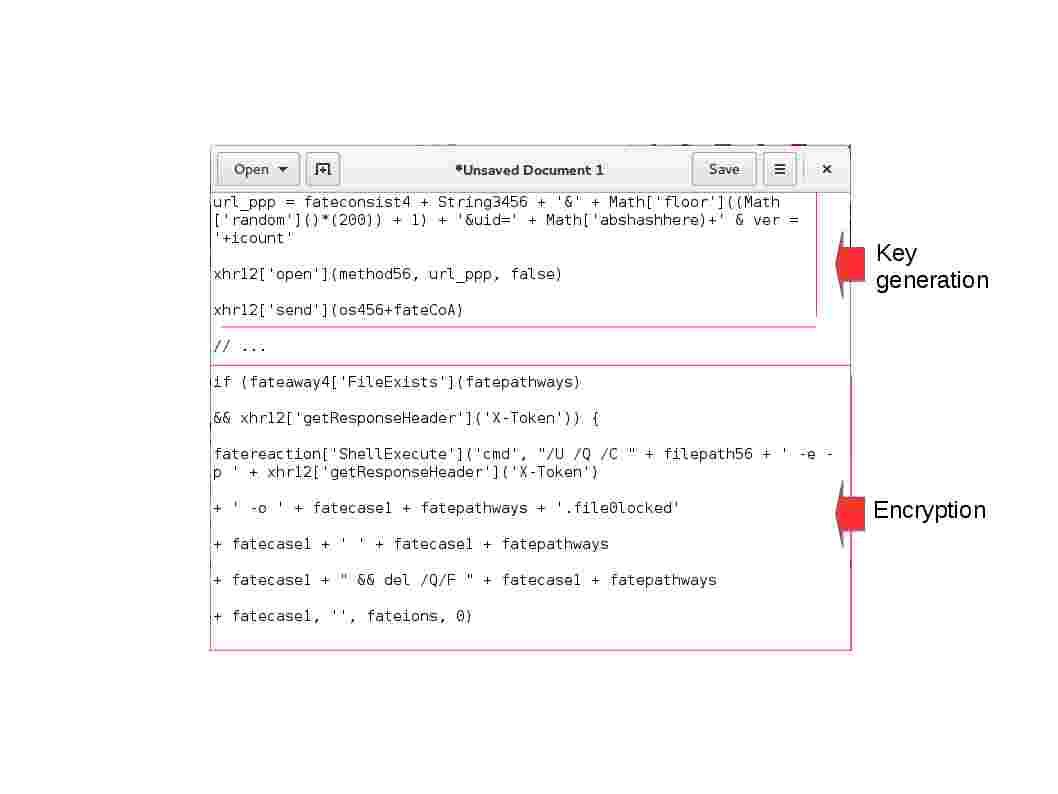
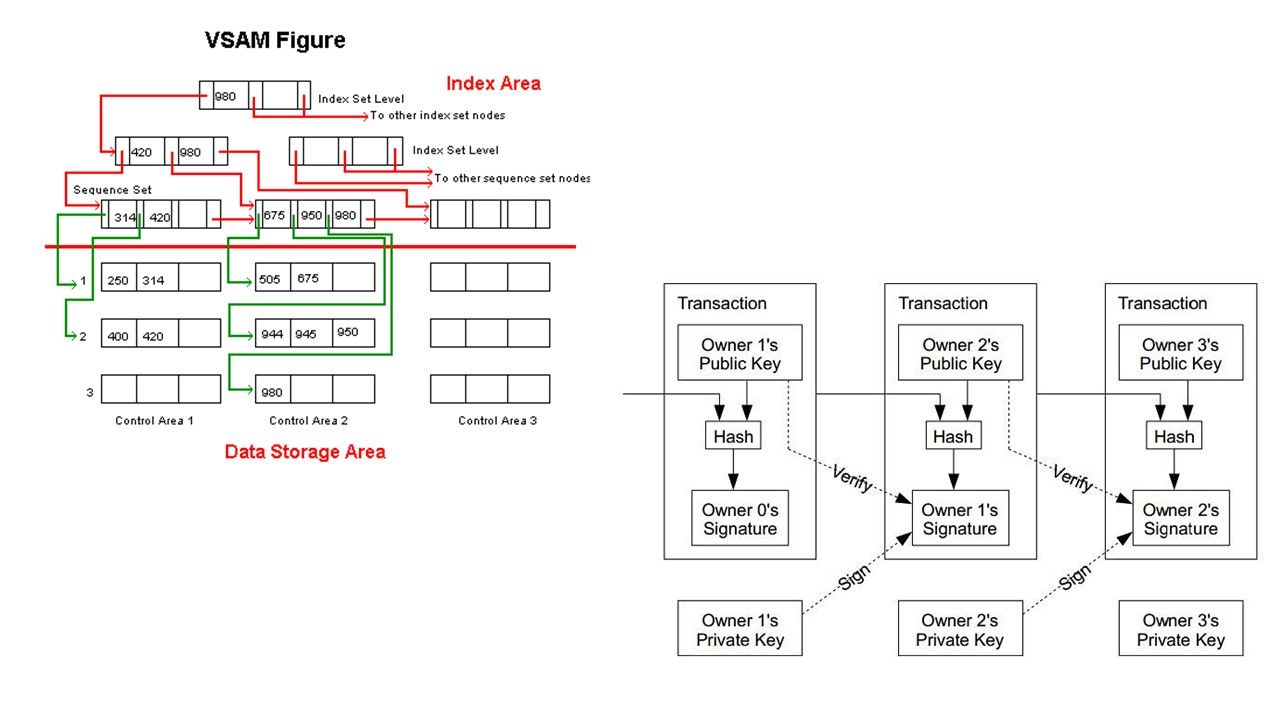
Electronic payment one of the major term of in our daily life. It is hard to imagine that what’s the result once without credit card payment, online payment transfer and mobile payment in the world! The cyber attack hits financial institution more frequently and rapidly especially malware. In this discussion, we are going to investigate modern technology on electronic business bring the impact on financial institution in the long run. The mainframe computer bring a secure environment to IT world since it operate on a proprietary operation system (z-OS), well defined system architecture (trusted kernel OS). You never heard that a zero-day vulnerability encounters on MainFrame OS or application weekly. As times goes by, the over demanding business activities in the world transfer the motivation equivalent push a secure technology concepts to the cliff side.
Can we say Java technology is the instigator?
The MainFrame system designer did not have hiccups of their system design since the isolation level of memory and operating system coding not as easy as jailbreak a iPhone iOS or windows OS system. However a security weakness of the system feature might bring an unforeseen tragedy to their environment.
Java for OS/390 creates java bytecodes which are not directly executable OS/390 instructions.
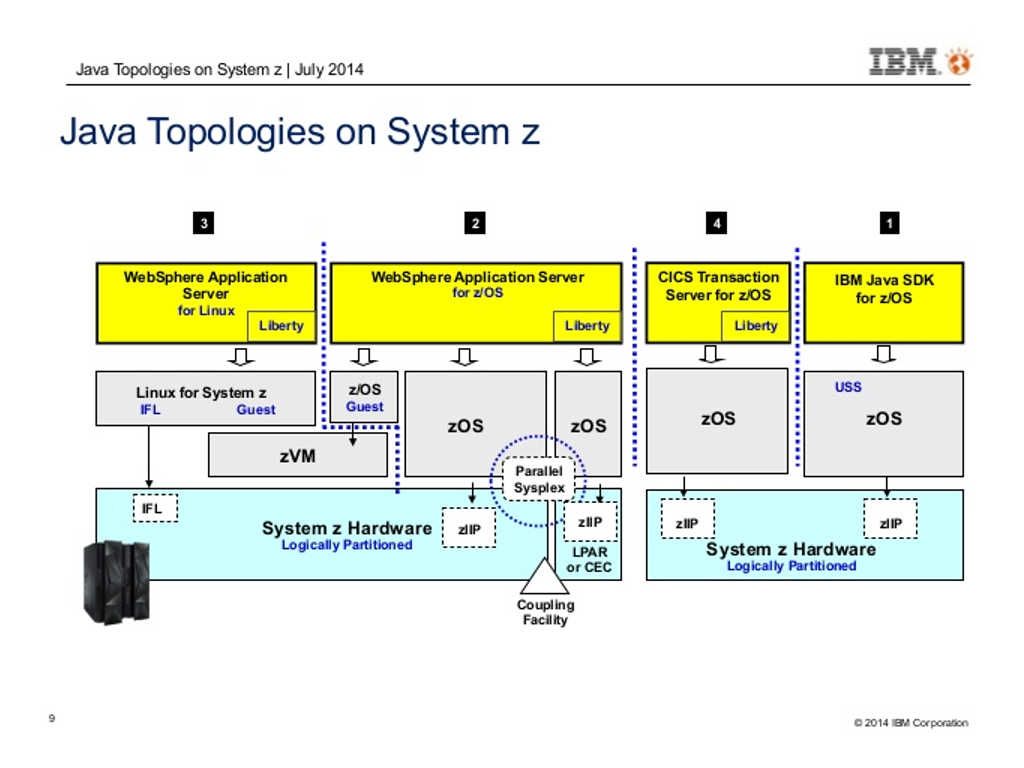
However a indirect way may possible lets Logical partitions (LPARs) become vulnerable.
Why?
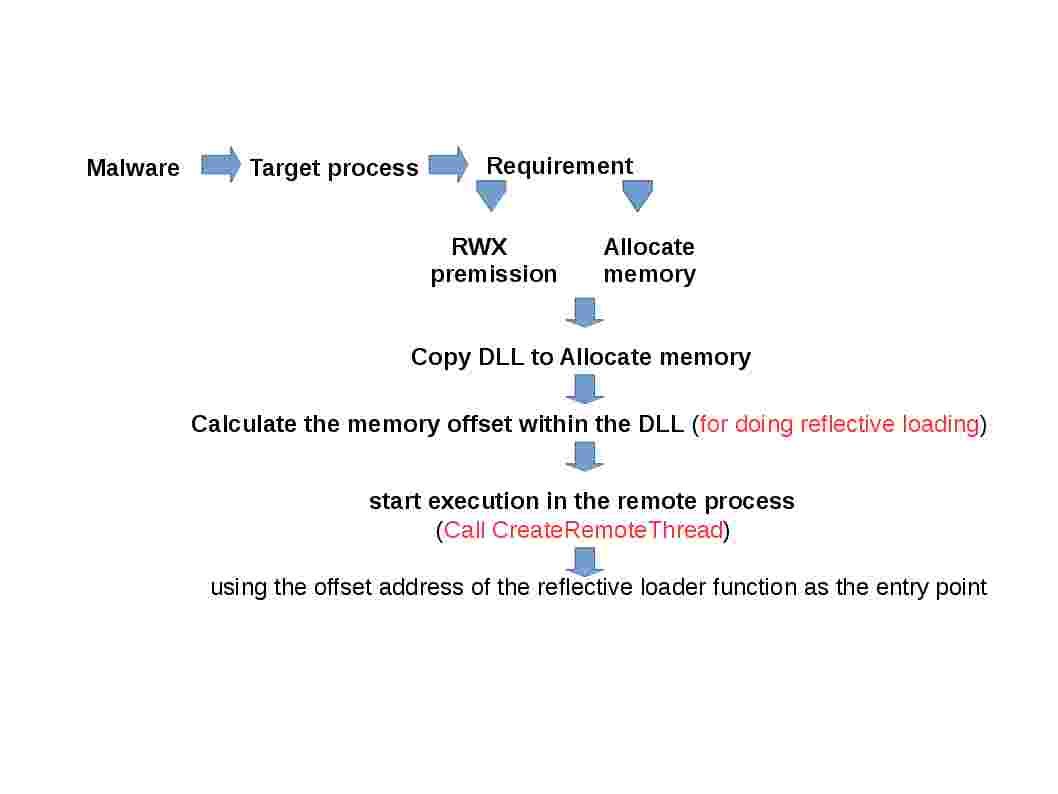
The combination of buffer overflow and heap spraying is the most common exploitation of pdf malware. How mainframe generate pdf format of file driven by cobol programming language. FPDF is a PHP class which allows to generate PDF files with pure PHP, that is to say without using the PDFlib library. But what is the inherit potential vulnerability of Java. The Java API for JSON Processing provides portable APIs to parse, generate and transform.The COBOL application populates the CRD and passes it to the generation subroutine (RCJSNGEN) with the CRD source in a CALL statement. RCJSNGEN then converts the COBOL data to JSON objects and returns the top level JSON object to the application. Even though cobol program module not vulnerable. But 2 items of high risk application run on top of mainframe Logical partitions (LPARs).
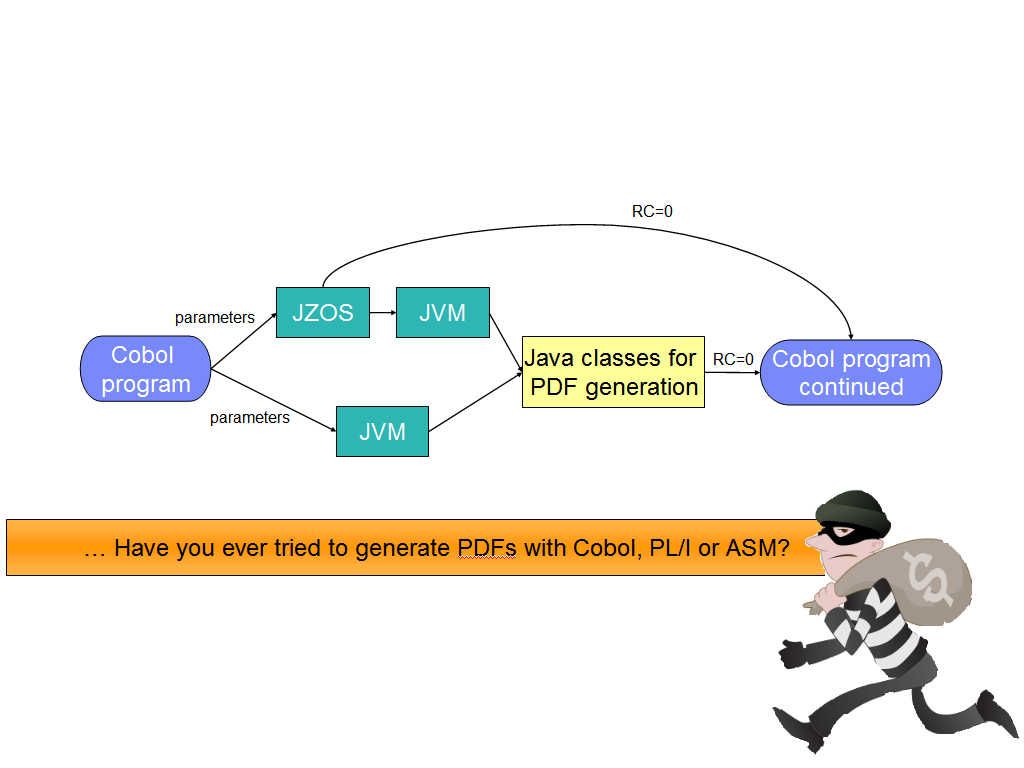
But reminds reader that Java for OS/390 creates java bytecodes which are not directly executable OS/390 instructions. Can we say OS/390 can avoid ring zero attack absolutely?
Ok, let take a closer look of Z-OS system architecture.
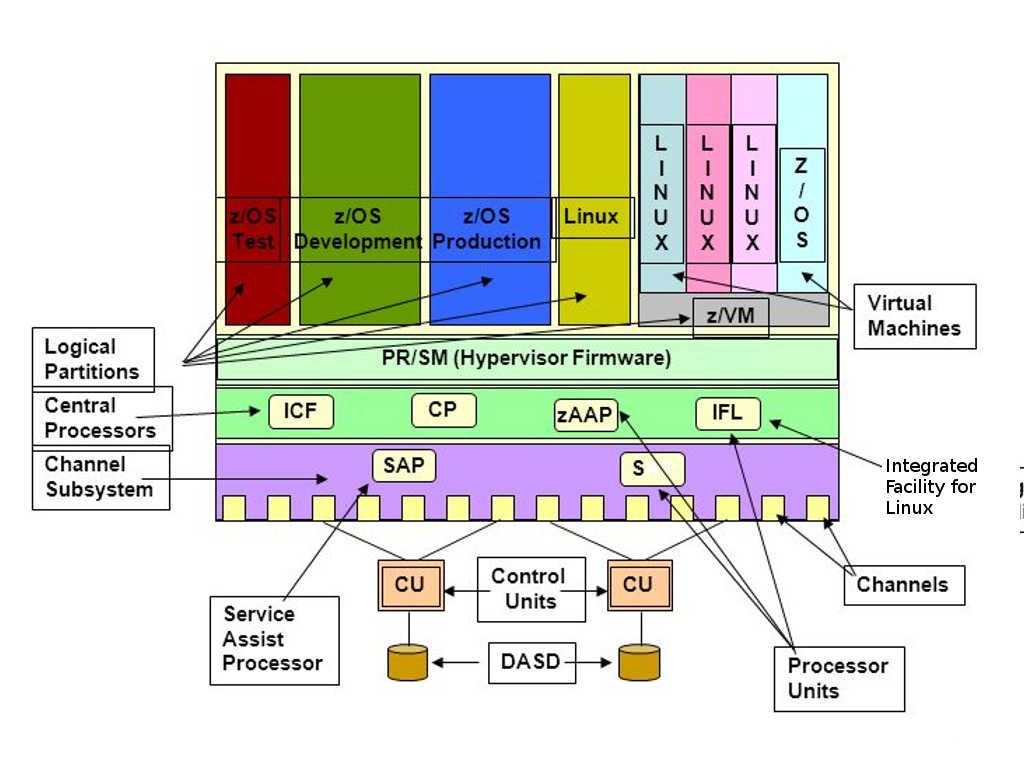
- User address spaces are unique and run single applications
- Multiple units of work can be active within the address space (parallel execution)
- User address spaces do not communicate with each other
- If one address space fails the other user address spaces continuous to run
2. System address spaces
- Execute system components (elements) – DB2, CICS, SMF, DFMS. These components are call subsystems.
- System components communicate with each other
3. Cloned or Duplicate address spaces running as a subsystem communicate with each other
- Multiple address spaces of a subsystem and as a component act as one
- If one address space fails, the components communicate with each other
Refer above 3 items, 3 types of memory address looks no direct communication with core OS since they are defined as a subsystem. But what is actual status of hardware DMA memory address resources sharing. For example, FICON to access local storage, network adapter (Ethernet and SDLC). And therefore it is hard to say that modernized mainframe environment as secure as classic mainframe system.
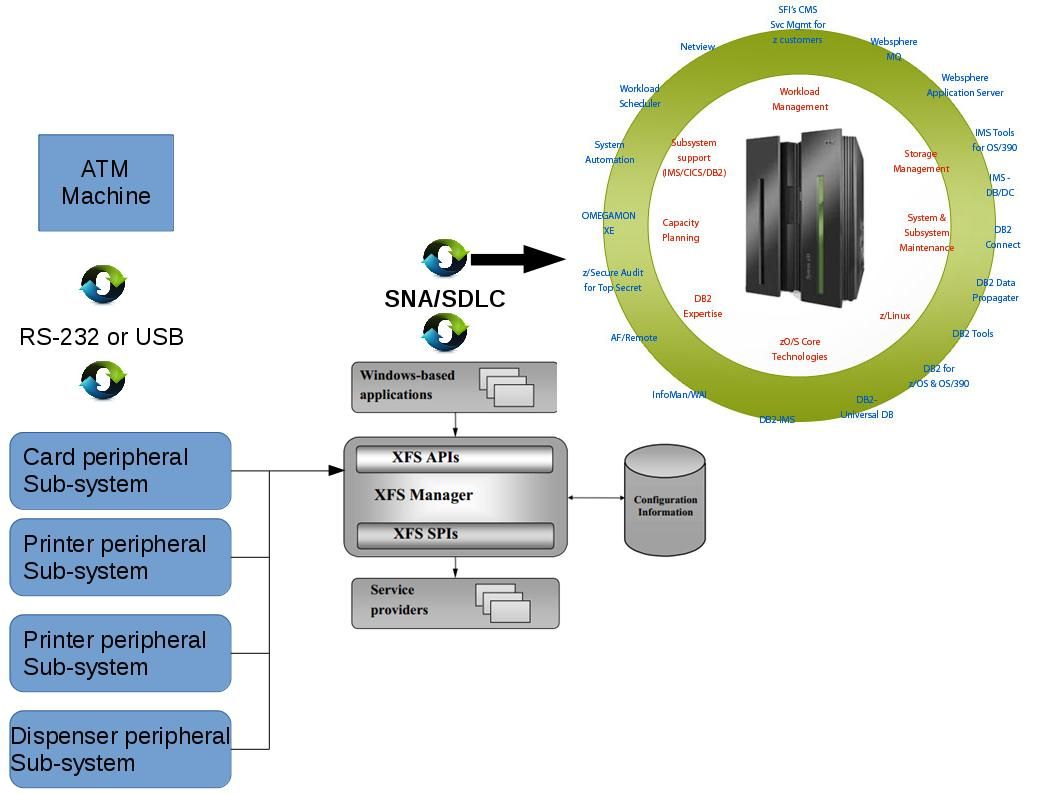
Electronic types of Bank Robbery
The Extensions for Financial Services (XFS) system accidentally driven of finance lost in banking industry. The XFS function is responsible for mapping the API (WFS…) functions to SPI (WFP…) functions, and calling the appropriate vendor-specific service providers. As a matter of fact, the Extensions for Financial Services (XFS) system causes financial lost looks serious than traditional bank robbery case. For instance ATM malware incident or 2016 Bangladesh Bank heist. The total of amount of financial lost are huge. From humanity point of view, feeling of optimism since such financial lost incidents did not injure human life. However it is more difficult to fight with technology crime compare with traditional crime.
Reference:
The Phantom of the payment (SWIFT) – A new system flaw found by Microsoft this week. Is there any relationship?
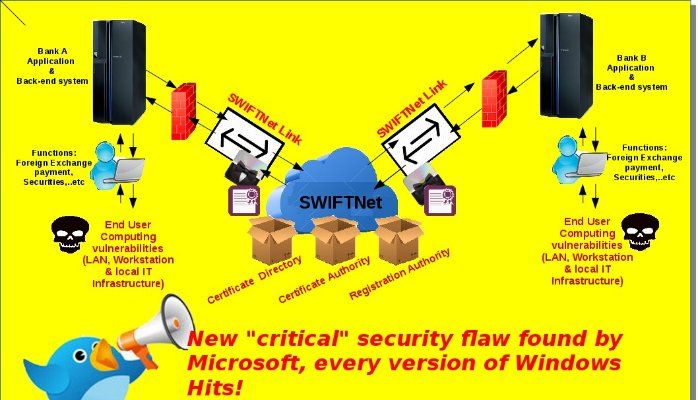
The APAC countries audience might voted “The Phantom of the Opera” is the famous opera, right? I familiar with the song, The Phantom of the Opera is there. Inside my mind. …..Yes, regarding to the subject matter, I digress.The payment flaw incidents happened this year looks didn’t have appropriate resolution to resolve. “To share attack intelligence … SWIFT first needs more hacked banks to come clean.” Brussels-based SWIFT announced the launch of the new team on July 11 as part of a customer security program unveiled by CEO in May. The program was a reaction to persistent security criticism leveled at SWIFT in the wake of the $81 million heist from Bangladesh Bank earlier this year. Read a lot of technical articles and analytic reports receive the understanding of the security weakness of the core system. I am not going to mention too much in this area because you can easily found the related informations on internet. But the payment flaw security incident especially incident happened in Bangladesh bank. As a matter of fact, it bring to our attention that the weakness of end user computing and IT infrastructure let this nightmare occurred. Why do we recall this system flaw again? New issued by Microsoft yesterday, a vulnerability occurs on windows OS system. Yes, we don’t surprise on zero-day weekly. However this vulnerability bring to my attention once again! How importance of end user computing was?
Microsoft found the following:
An attacker could exploit the flaw by conducting a man-in-the-middle attack on a system or print server and injecting malicious code. That’s possible because the print spooler service doesn’t properly validate print drivers when installing a printer.
The conclusion told that rootkit or malware can relies on this way jump inside windows OS system in silent mode because the print spooler service doesn’t properly validate print drivers! It sounds horrible, right?
My personal opinion is that end user computing is the major factor in nowadays IT world regardless of which types of system. I did penetration test on SWIFTNET in 2010 and couldn’t found any critical flaw on SWIFTNET. At that time mistake to believe that modern defence mechanism can fight with insider threats. Seems the stories happened can tell.
In the meantime, I strongly believed that the weakness of system (SWIFT) not the major factor causes serious cyber security incident and fraudulent payments. The initial instigator is the end user computing. Let’s keep our eye open and see whether it is true or not.
Reference articles refer below URLs:
Swift Hack Probe Expands to Up to a Dozen Banks Beyond Bangladesh
SWIFT CEO warns: Expect more hacking attacks
Every version of Windows hit by “critical” security flaw
http://www.zdnet.com/article/every-version-of-windows-hit-by-critical-security-flaw/
ATM thieves are all in jail. Can you tell me that bank ATM environments are safe now?