Preface: Modern SoCs typically employ heterogeneous remote processor devices in asymmetric multiprocessing (AMP) configurations, which may be running different instances of operating system, whether it’s Linux or any other flavor of real-time OS.
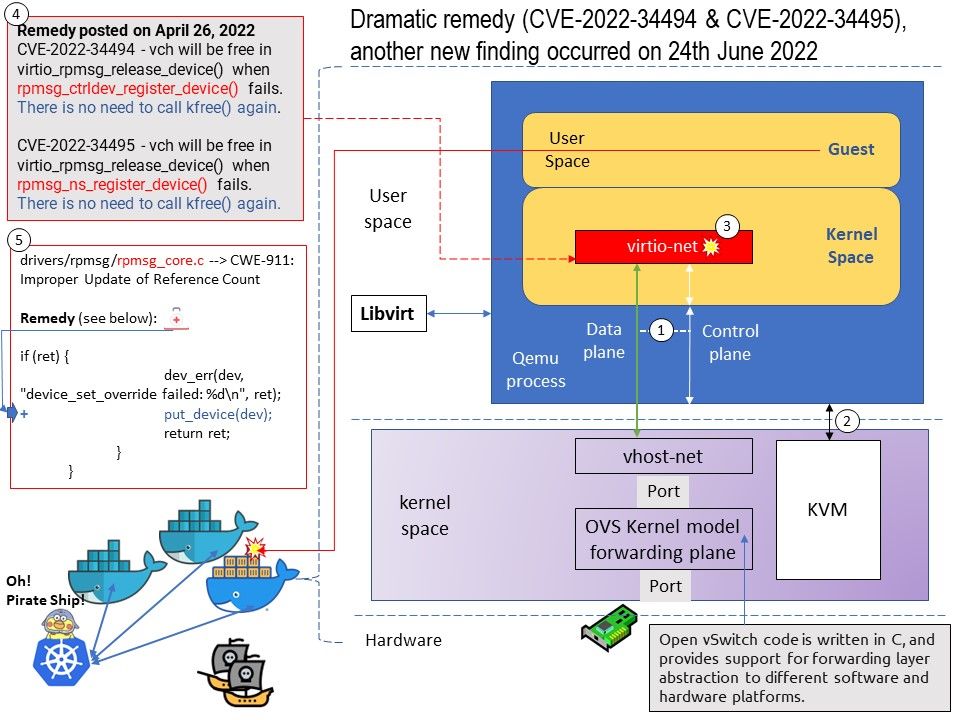
The Linux* Kernel vhost-net module was developed as an offload mechanism for virtio-net. The vhost-net module enables KVM (QEMU) to offload the servicing of virtio-net devices to the vhost-net kernel module, reducing the context switching and packet copies in the virtual dataplane.
Background: Rpmsg is a virtio-based messaging bus that allows kernel drivers to communicate with remote processors available on the system. In turn, drivers could then expose appropriate user space interfaces, if needed.
Every rpmsg device is a communication channel with a remote processor (thus rpmsg devices are called channels). Channels are identified by a textual name and have a local (“source”) rpmsg address, and remote (“destination”) rpmsg address.
When a driver starts listening on a channel, its rx callback is bound with a unique rpmsg local address (a 32-bit integer). This way when inbound messages arrive, the rpmsg core dispatches them to the appropriate driver according to their destination address (this is done by invoking the driver’s rx handler with the payload of the inbound message).
About double free: Double free errors occur when free() is called more than once with the same memory address as an argument. Calling free() twice on the same value can lead to memory leak.
Vulnerability details: The following vulnerabilities have remediation released on April 26, 2022.
CVE-2022-34494 – rpmsg_virtio_add_ctrl_dev in drivers/rpmsg/virtio_rpmsg_bus.c in the Linux kernel before 5.18.4 has a double free.
vch will be free in virtio_rpmsg_release_device() when rpmsg_ctrldev_register_device() fails. There is no need to call kfree() again.
CVE-2022-34495 – rpmsg_probe in drivers/rpmsg/virtio_rpmsg_bus.c in the Linux kernel before 5.18.4 has a double free.
vch will be free in virtio_rpmsg_release_device() when
rpmsg_ns_register_device() fails. There is no need to call kfree() again.
Summary: Fix this by changing error path from free_vch to free_ctrldev.It is recommended to upgrading to version 5.18.4 eliminates this vulnerability.
Observation: I say this vulnerability is dramatic. See the new findings from June 24, 2022 below. My feeling is that the design weaknesses fixed in April 2022 are not done yet. Maybe in a hurry.
Vulnerability details: rpmsg_register_device_override need to call put_device to free vch when driver_set_override fails. Fix possible refcount leak in rpmsg_register_device_override()
Remedy: Fix this by adding a put_device() to the error path.
Status: Not sure whether this fix will be included in 5.18.4 or require to update to latest version.

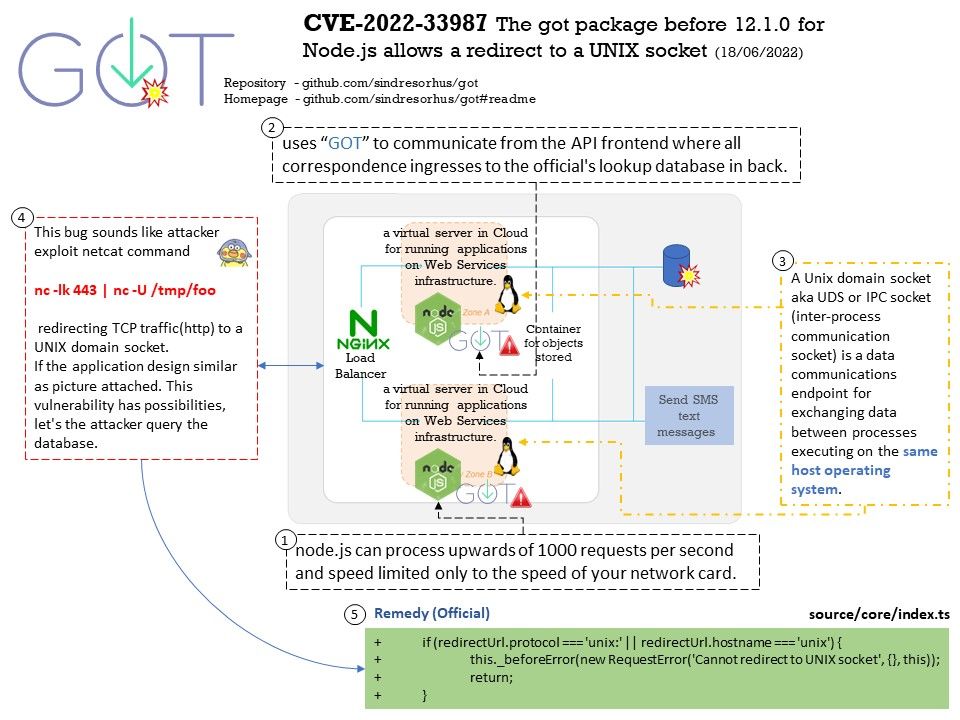
.jpg)
.jpg)