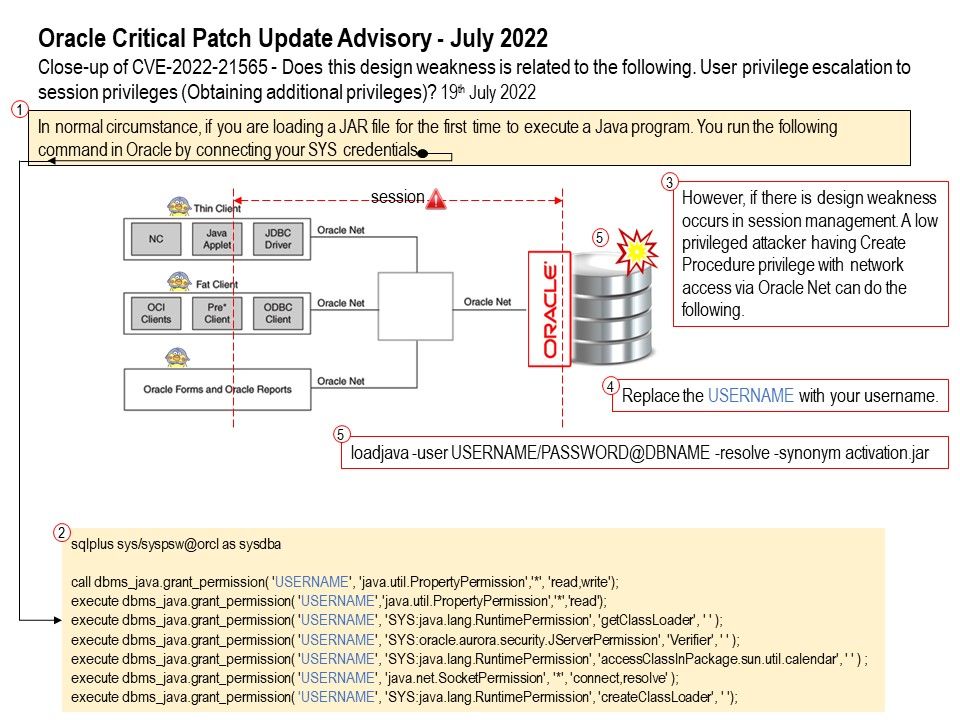
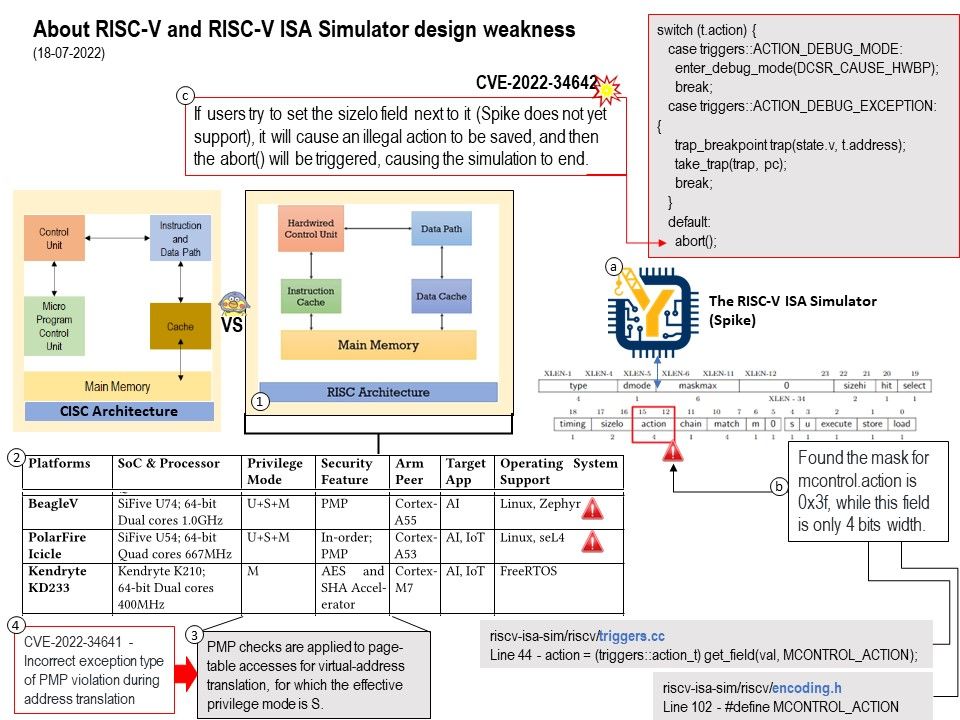
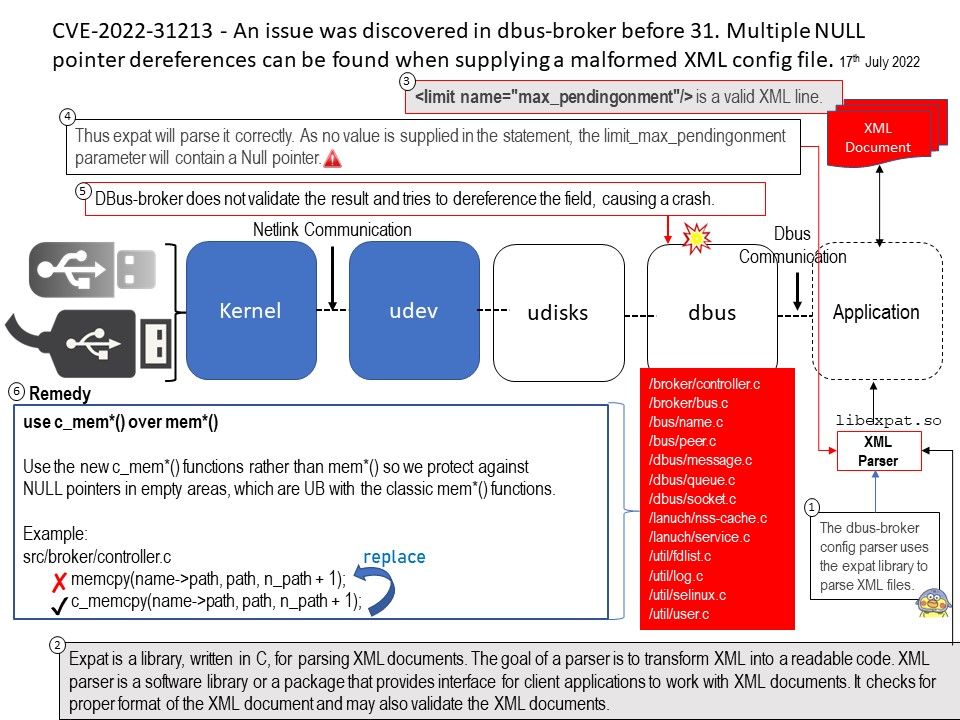
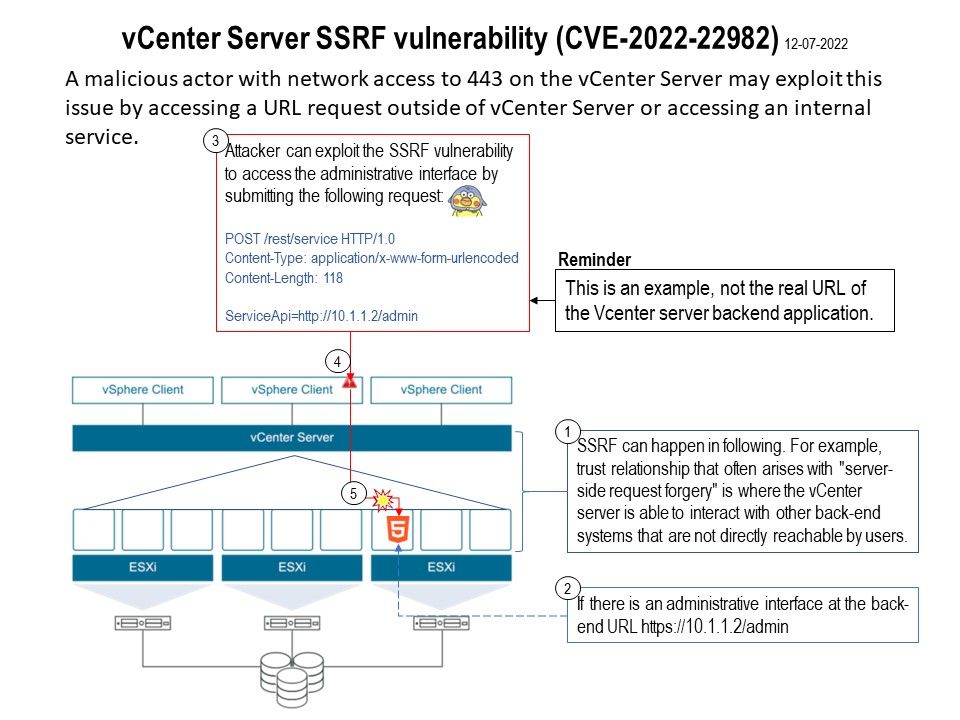
Preface: According to technical report (OT:ICEFALL) by cyber security service provider (Forescout). They observe that an APT toolkit targeting several OT devices, such as OPC UA servers and PLCs from Omron and Schneider Electric. According to ICS-CERT advisories on 28th June, 2022. The article had written down the RISK EVALUATION. Successful exploitation of these vulnerabilities could cause a denial-of-service condition and allow remote code execution.Please refer to the link for details.
Background: The Omron FINS Ethernet Driver provides a reliable way to connect Omron FINS Ethernet controller to client applications; including HMI, SCADA, Historian, MES, ERP, and countless custom applications.
Remark: A PLC is a hardware-based device, SCADA is a system that works in conjunction with the PLC. Furthermore, HMI is also a system that works in conjunction with a PLC.
Omron PLCs usually have three different modes; Program Monitor and Run.
- Program Mode: In PROGRAM mode the CPU unit is stopped so your logic will not be executed. User programming can be created or modified, memory can be cleared, and programs can be checked. Depending on the PLC type there may be other options as well.
- Monitor Mode: In MONITOR mode the CPU unit is running, so your logic will be executed. I/O is processed in the same way as in RUN mode. The operating status of the CPU unit can be monitored, bits can be forced and/or set or reset. The set values and present values of timers and counters can be modified. The present values of word data can be modified. This mode is used for system adjustments.
- Run Mode: RUN mode is used for normal system operation. The operating status of the CPU unit can be monitored, but bits cannot be forced and/or set or reset. Present and set values cannot be modified using programming devices.
Let’s put our CP1H controller into monitor mode. Ctrl + 3, Monitor Icon or PLC | Operating Mode | Monitor from the main menu.
Vulnerability details (see below):
- CVE-2022-31204 – Omron CS series, CJ series, and CP series PLCs through 2022-05-18 use cleartext passwords.
- CVE-2022-31207 – The Omron SYSMAC Cx product family PLCs (CS series, CJ series, and CP series) through 2022-05-18 lack cryptographic authentication.
- CVE-2022-31206 – The Omron SYSMAC Nx product family PLCs (NJ series, NY series, NX series, and PMAC series) through 2022-005-18 lack cryptographic authentication.
- CVE-2022-31205 – In Omron CS series, CJ series, and CP series PLCs through 2022-05-18, the password for access to the Web UI is stored in memory area D1449…D1452 and can be read out using the Omron FINS protocol without any further authentication.
Remark: Omron Cx series Authentication bypass & plaintext credentials – CVE-2022-31204, CVE-2022-31205
Reference A: Public report, known as “OT:ICEFALL” that details vulnerabilities found in multiple operational technology (OT) vendors. Please follow this link to download the report – https://www.forescout.com/resources/ot-icefall-report/
Reference B: ICS-CERT advisories on 28th June, 2022. Please follow this link to download the report – https://www.cisa.gov/uscert/ics/advisories/icsa-22-179-02
.jpg)
.jpg)