Preface: We known that so called vulnerability may be found few months or year ago. But zero-day vulnerability have different. A zero-day is a computer-software vulnerability previously unknown to those who should be interested in its mitigation, like the vendor of the target software. Because of it urgency, it need to announce or release the fix shortly.
Background: What does Site Recovery do?
Site Recovery contributes to your business continuity and disaster recovery (BCDR) strategy, by orchestrating and automating replication of Azure VMs between regions, on-premises virtual machines and physical servers to Azure, and on-premises machines to a secondary datacenter.
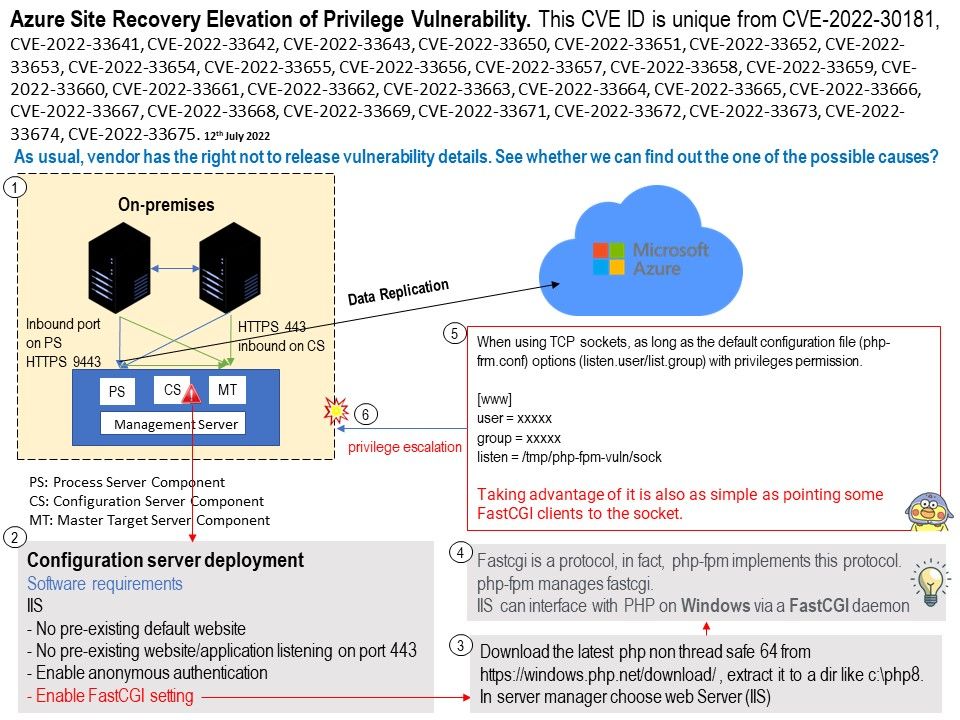
Vulnerability details: Azure Site Recovery Elevation of Privilege Vulnerability. This CVE ID is unique from CVE-2022-30181, CVE-2022-33641, CVE-2022-33642, CVE-2022-33643, CVE-2022-33650, CVE-2022-33651, CVE-2022-33652, CVE-2022-33653, CVE-2022-33654, CVE-2022-33655, CVE-2022-33656, CVE-2022-33657, CVE-2022-33658, CVE-2022-33659, CVE-2022-33660, CVE-2022-33661, CVE-2022-33662, CVE-2022-33663, CVE-2022-33664, CVE-2022-33665, CVE-2022-33666, CVE-2022-33667, CVE-2022-33668, CVE-2022-33669, CVE-2022-33671, CVE-2022-33672, CVE-2022-33673, CVE-2022-33674, CVE-2022-33675.
As usual, vendor has the right not to release vulnerability details. See whether we can find out the one of the possible causes?
For disaster recovery of VMware VMs to Azure, system administrator should deploy the configuration server as a VMware VM. Based on my speculation of existing design flaws. So just focus on suspicious components.
Software requirements: IIS (Web server)
- No pre-existing default website
- No pre-existing website/application listening on port 443
- Enable anonymous authentication
- Enable FastCGI setting
When using TCP sockets, as long as the default configuration file (php-frm.conf) options (listen.user/list.group) with privileges permission.
Local attacker is possible to exploit this vulnerability. It is as simple as pointing some FastCGI clients to the socket. Then it will execute priviliges escalation. Please refer to attached diagram for reference.
Azure Site Recovery Elevation of Privilege Vulnerability. For official announcement, please refer to the link – https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2022-33677
Remedy: What can I do to protect myself from this vulnerability? You can follow the steps here to update to version 9.49.