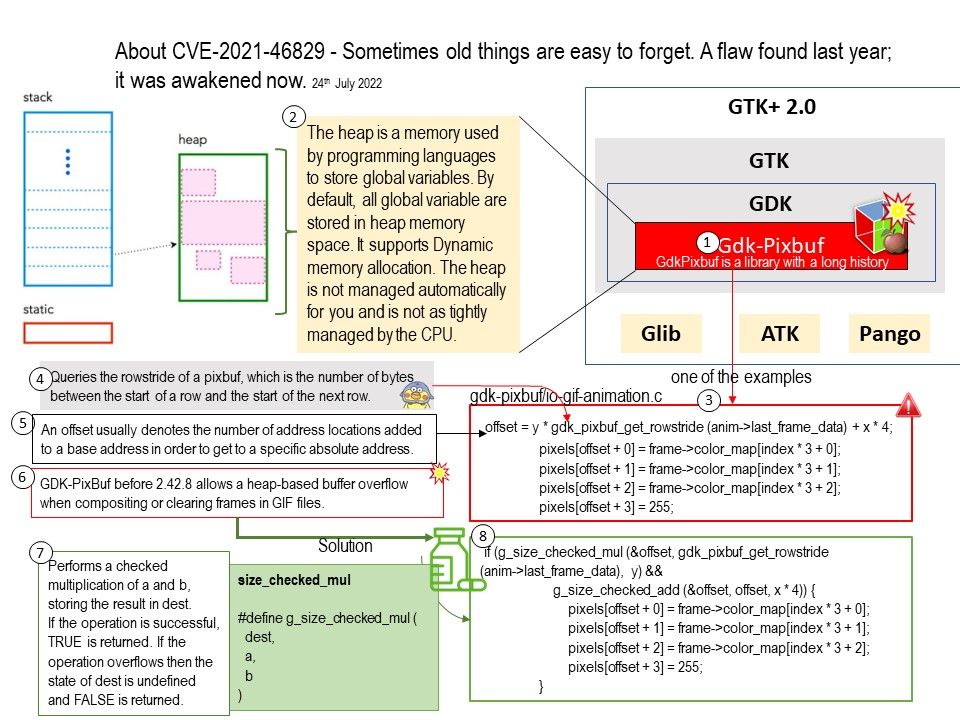
Preface: GdkPixbuf is a library with a long history, and it has been incrementally modified over years, so it may retain some older coding practices alongside newer ones.
Background: GdkPixbuf is a library that loads image data in various formats and stores it as linear buffers in memory. The buffers can then be scaled, composited,modified, saved, or rendered.GdkPixbuf can load image data encoded in different formats, such as: PNG, JPEG, TIFF, TGA and GIF.
The GdkPixbuf class provides methods for saving image data in a number of file formats. The formatted data can be written to a file or to a memory buffer. GdkPixbuf can also call a user-defined callback on the data, which allows to e.g. write the image to a socket or store it in a database.
Vulnerability details: GNOME GdkPixbuf (aka GDK-PixBuf) before 2.42.8 allows a heap-based buffer overflow when compositing or clearing frames in GIF files, as demonstrated by io-gif-animation[.]c composite_frame. This overflow is controllable and could be abused for code execution, especially on 32-bit systems.
This design weakness found in last year. Since no CVE was registered, it probably is not being considered as a problem for downstream users of the package. Till July 2022, the latest Debian stable package is affected by this vulnerability. Using a GNOME file system browser and browsing to that folder will cause a crash, as will opening it up in a GNOME image viewer and even attempting to load it in Chromium .
The bug is in composite_frame() in io-gif-animation[.]c. The problem appears to be in the calculation of the offset variable (see below):
- because it is a signed int, it can overwrite when it’s over INT32_MAX.
- even if it was as an unsigned int, given the calculations, it becomes quite easy to reach very large values.
Solution: Upgrade to gdk-pixbuf 2[.]42[.]8