Preface: Server-side request forgery (SSRF) is a web security vulnerability that allows an attacker to induce the server-side application to make requests to an unintended location. Additionally, SSRF attacks against other backend systems are also an evasion path. Sometimes an SSRF risk rating is medium risk, so it goes unnoticed (contempt).
Background: vCenter Server manages VMware vSphere environments, giving IT administrators simple and automated control over the virtual environment to deliver infrastructure with confidence. VMware vSphere Web Client plug-in is the program that extends the user interface for VMware vSphere Web Client to a browser. The VMware vSphere Web Client allows an administrator to connect to a vCenter Server system and manage a vSphere environment.
Vulnerability details: The vCenter Server contains a server-side request forgery (SSRF) vulnerability. VMware has evaluated the severity of this issue to be in the Moderate severity range with a maximum CVSSv3 base score of 5.3.
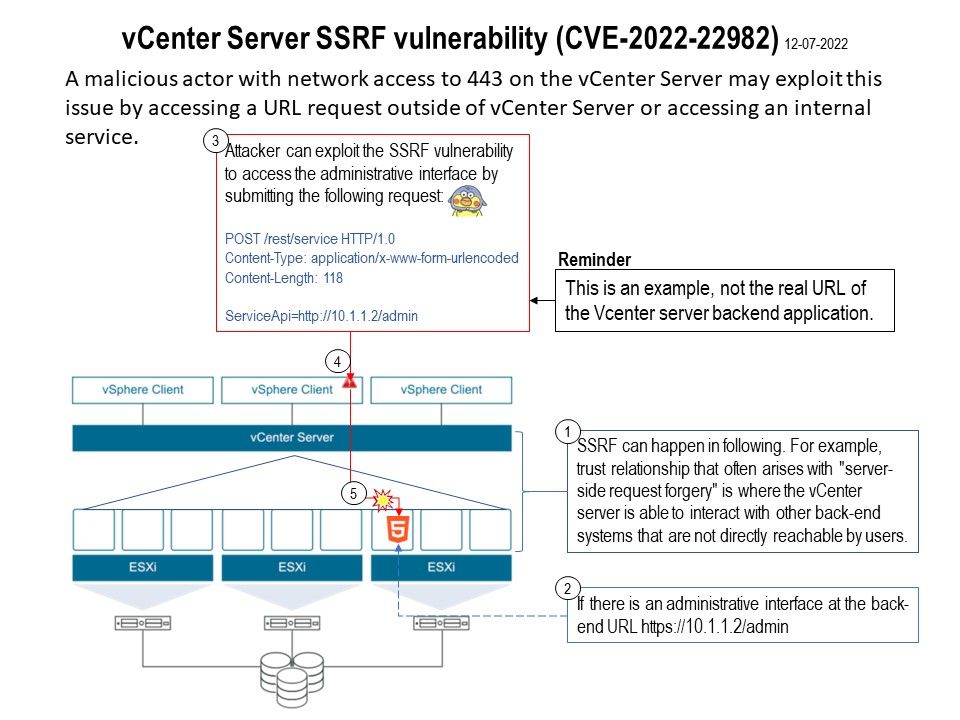
Impact: A malicious actor with network access to 443 on the vCenter Server may exploit this issue by accessing a URL request outside of vCenter Server or accessing an internal service. For more details, please refer to attached diagram.
Solutions: Before installation of the software, please visit the vendor web-site for more details – https://www.vmware.com/security/advisories/VMSA-2022-0018.html