Preface: As time goes by, online training course is the mainstream to offload traditional onsite training course. The Learning Management System (LMS) is a software application designed to deliver, track, report on and manage trainings and learner activity. Some popular LMS used by educational institutions include Moodle, Blackboard Learn and Schoology.
Accroding to security reason, LMS will running in a separate web hosting area. However, if it contains (stored XSS and blind SSRF) vulnerabilities. Even though it is not running in the student office, it is potentially risky allowing cybercriminals to steal their sensitive information. Therefore, it may affect their enterprise systems.
Background: SCORM (Sharable Content Object Reference Model) can be described as a collection of standards and specifications that allow for the description and packaging of an e-learning course. SCORM 1.2 is the most widely distributed version of the SCORM specification. The SCORM 1.2 definition has two main parts SCORM Content Aggregation Model (CAM) and SCORM RunTime Environment (RTE).
SCORM packages are typically zip files. Within the zip file you will find all the content needed at delivery time by the SCORM package and a manifest file, named imsmanifest.xml. The manifest file describes the SCORM package so that the SCORM player understands how to run the SCORM package.
SCORM 1.2 is supported by Moodle 1.9.3 (or higher) and Moodle 1.8.7 (or higher). It is very simple to add a SCORM package to Moodle. The SCORM package is simply added to a course as a course activity.
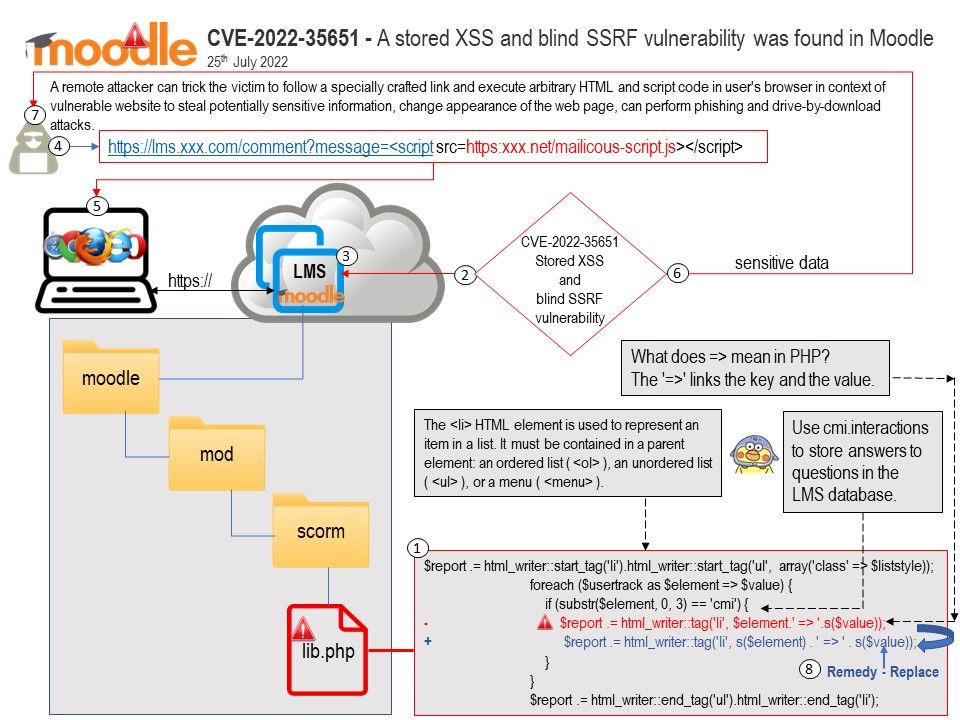
Vulnerability details: A stored XSS and blind SSRF vulnerability was found in Moodle, occurs due to insufficient sanitization of user-supplied data in the SCORM track details. A remote attacker can trick the victim to follow a specially crafted link and execute arbitrary HTML and script code in user’s browser in context of vulnerable website to steal potentially sensitive information, change appearance of the web page, can perform phishing and drive-by-download attacks.
Below details are the existing vulnerabilities found by vendor.
CVE-2022-35653 – A reflected XSS issue was identified in the LTI module of Moodle
CVE-2022-35652 – An open redirect issue was found in Moodle due to improper sanitization of user-supplied data in mobile auto-login feature.
CVE-2022-35651 – A stored XSS and blind SSRF vulnerability was found in Moodle, occurs due to insufficient sanitization of user-supplied data in the SCORM track details.
CVE-2022-35650 – The vulnerability was found in Moodle, occurs due to input validation error when importing lesson questions.
CVE-2022-35649 – Due to improper input validation when parsing PostScript code. An omitted execution parameter results in a remote code execution risk for sites running GhostScript versions older than 9.50.
Solution: For Solutions to fix the above vulnerabilities. See the official announcement in the link – https://moodle.org/security/