Preface: The open source Paho MQTT project for embedded C to connect and communicate with IoT Platform.
Background: MQTT is based on the client-server communication mode. MQTT server is called as MQTT Broker. Currently, there are many MQTT Brokers in the IIoT world. MQTT client libraries under different programming languages and platforms (see below):
Eclipse Paho C and Eclipse Paho Embedded C
Eclipse Paho Java Client
Eclipse Paho MQTT Go client
emqtt : Erlang mqtt client library provided by EMQ
MQTT.js Web & Node.js Platform MQTT Client
Eclipse Paho Python
The Paho MQTT project for embedded C includes three sub-projects:
– MQTTPacket: provides serialization and deserialization of MQTT data packets and some helper functions.
– MQTTClient: encapsulates the high-level C++ client program generated by MQTTPacket.
– MQTTClient-C: encapsulates the high-level C client program generated by MQTTPacket.
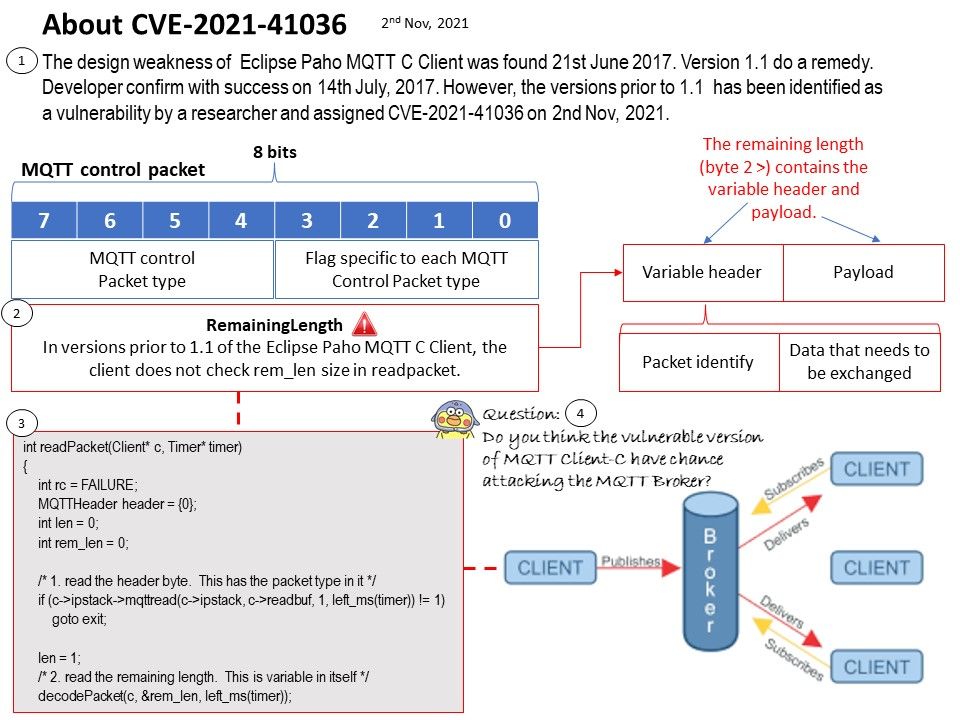
Vulnerability details: In versions prior to 1.1 of the Eclipse Paho MQTT C Client, the client does not check rem_len size in readpacket.
Ref: The design weakness of Eclipse Paho MQTT C Client was found 21st June 2017. Version 1.1 do a remedy. Developer confirm with success on 14th July, 2017. However, the versions prior to 1.1 has been identified as a vulnerability by a researcher and assigned CVE-2021-41036 on 2nd Nov, 2021.
Question: Do you think the vulnerable version of MQTT Client-C have chance attacking the MQTT Broker?
Official announcement: https://github.com/eclipse/paho.mqtt.embedded-c/issues/96