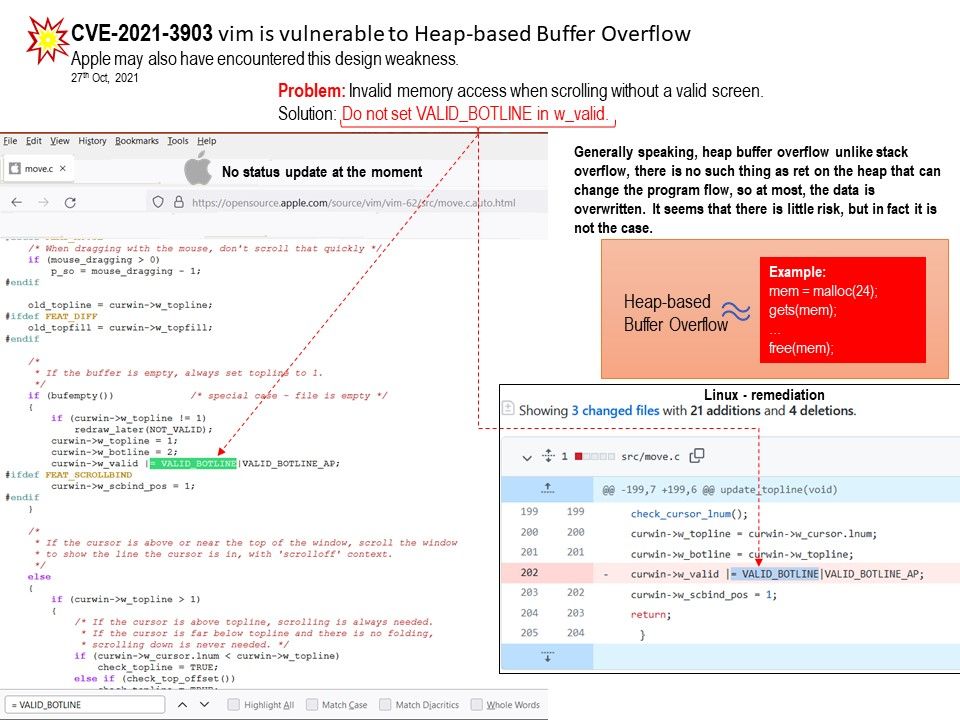
Preface: Generally speaking, heap buffer overflow unlike stack overflow, there is no such thing as ret on the heap that can change the program flow, so at most, the data is overwritten. It seems that there is little risk, but in fact it is not the case.
Background: Vim comes standard with most modern Linux distributions, but some of the minimal installation doesn’t include vim editor default. Vim is a vi-like editor but is more advanced and powerful than the original Vi.
Vulnerability details: Certain versions of vim is vulnerable to Heap-based Buffer Overflow. Found design weakness in raw file (move.c) programming syntax. Invalid memory access when scrolling without a valid screen.
A heap overflow condition is a buffer overflow, where the buffer that can be overwritten is allocated in the heap portion of memory, generally meaning that the buffer was allocated using a routine such as malloc(). Buffer overflows generally lead to crashes.
Remedy: Do not set VALID_BOTLINE in w_valid.
Affected Vendor/Software: vim/vim version < 8.2.3564
Reference: In C++, new/delete should be preferred over malloc()/free() where possible. (In C, new/delete is not available, so the choice would be obvious there.)
The main difference between both these languages is C is a procedural programming language and does not support classes and objects, while C++ is a combination of both procedural and object-oriented programming languages.
Usually C compiler doesn’t add boundaries check for memory access. Sometimes due to code error, there is read or write from outside the buffer, such an error is usually hard to detect.