Preface: We install and configure a caching plugin which will speed up the delivery of page assets to your visitors, since these content will have been generated beforehand. The result will be a faster loading page, and reduced wait times for all operations.
Background: A caching plug-in will speed up the web application response. For websites with very high traffic (load balancing),
we install and configure object caching plugins, such as Redis or Memcache.
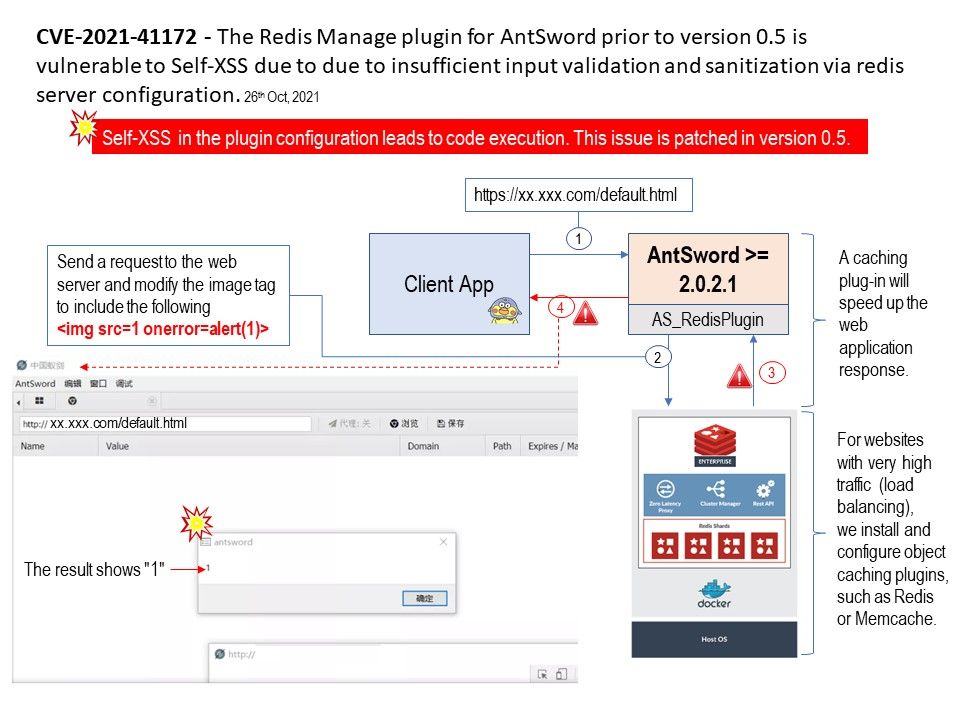
Vulnerability details: Redis is an open source (BSD licensed), in-memory data structure store, used as a database, cache, and message broker. AS_Redis is an AntSword plugin for Redis. The Redis Manage plugin for AntSword prior to version 0.5 is vulnerable to Self-XSS due to due to insufficient input validation and sanitization via redis server configuration. Self-XSS in the plugin configuration leads to code execution. This issue is patched in version 0.5.
How does Self-XSS work? Self-XSS operates by tricking users into copying and pasting malicious content into their browsers’ web developer console. Usually, the attacker posts a message that says by copying and running certain code, the user will be able to hack another user’s account.
Question: With reference to the attached picture, do you think it is really a self-xss vulnerability?
Official CVE announcement – https://nvd.nist.gov/vuln/detail/CVE-2021-41172