Preface: It is possible to trigger Rowhammer bit flips on DDR4 devices on AMD Zen 2 and Zen 3 systems despite deployed TRR mitigations, said researchers at ETH Zurich.
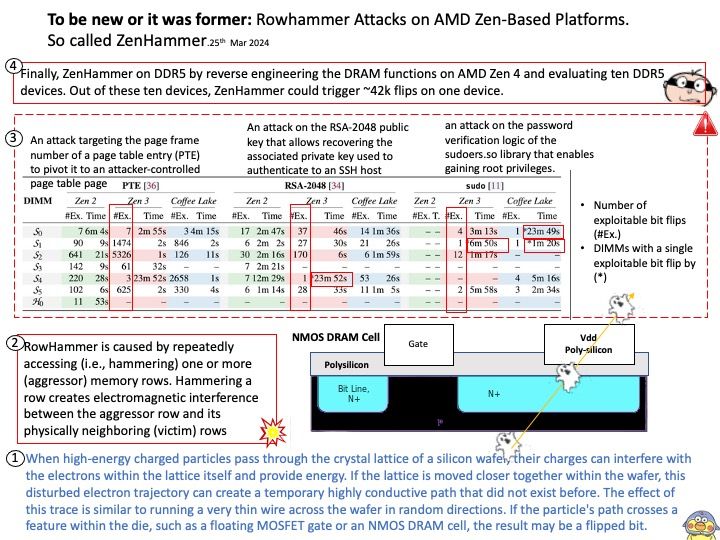
Background: When high-energy charged particles pass through the crystal lattice of a silicon wafer, their charges can interfere with the electrons within the lattice itself and provide energy. If the lattice is moved closer together within the wafer, this disturbed electron trajectory can create a temporary highly conductive path that did not exist before. The effect of this trace is similar to running a very thin wire across the wafer in random directions. If the particle’s path crosses a feature within the die, such as a floating MOSFET gate or an NMOS DRAM cell, the result may be a flipped bit.
Vulnerability details: On February 26, 2024, AMD received new research related to an industry-wide DRAM issue documented in “ZENHAMMER: Rowhammering Attacks on AMD Zen-based Platforms” from researchers at ETH Zurich. The research demonstrates performing Rowhammer attacks on DDR4 and DDR5 memory using AMD “Zen” platforms. Given the history around Rowhammer, the researchers do not consider these rowhammering attacks to be a new issue.
Mitigation: Please see the following official announcement for details – https://www.amd.com/en/resources/product-security/bulletin/amd-sb-7021.html