Preface: SD-WAN (Software-Defined WAN) is a service that overlays the hybrid network infrastructure, including SD-WAN routing. An intelligent software layer manages both MPLS WAN and other connections.
Both 5G and SD-WANs are independent technologies, but together they allow businesses to access their vital applications with the reliability, coverage, and speed that 5G provides.
Background: SD-WAN Edges perform deep application recognition, application and packet steering, performance metrics and end to end quality of service in addition to hosting virtual network function (VNF) services.
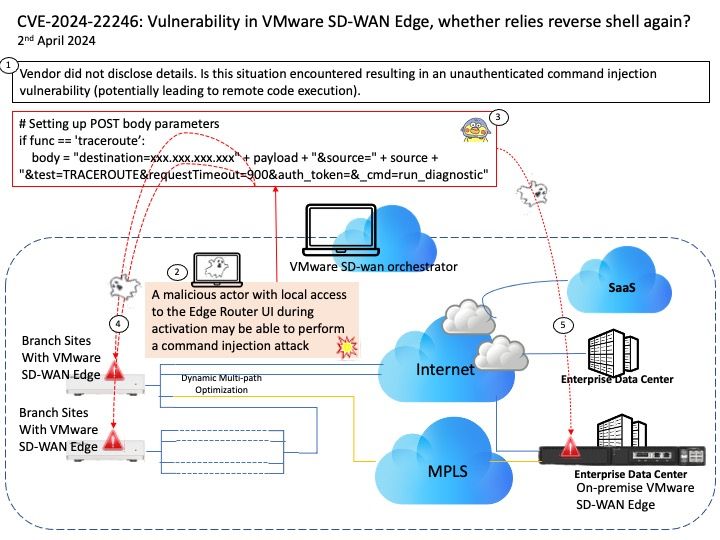
Vulnerability details: Unauthenticated Command Injection vulnerability in SD-WAN Edge (CVE-2024-22246)
VMware SD-WAN Edge contains an unauthenticated command injection vulnerability potentially leading to remote code execution. VMware has evaluated the severity of this issue to be in the Important severity range with a maximum CVSSv3 base score of 7.4.
Known Attack Vectors -A malicious actor with local access to the Edge Router UI during activation may be able to perform a command injection attack that could lead to full control of the router.
Official announcement: Please refer to the link for details – https://www.vmware.com/security/advisories/VMSA-2024-0008.html