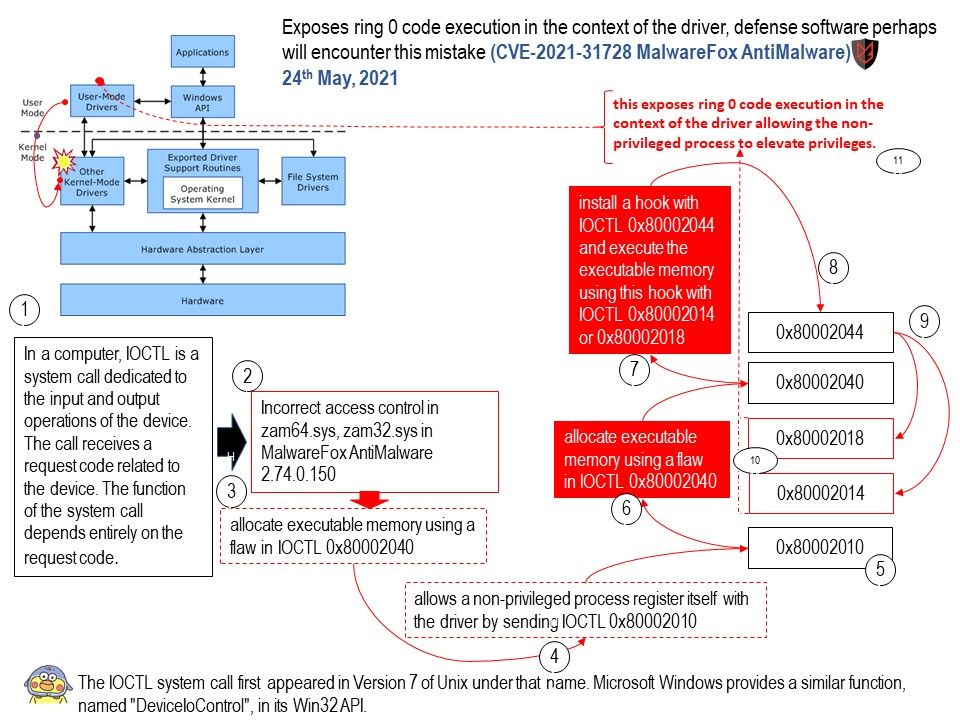
Preface: Nouveau is a free and open source graphics card driver. It is written for Nvidia’s graphics card and can also be used in the NVIDIA Tegra series of system chips. This driver is written by a group of independent software engineers. Nvidia sometimes will be assistance.
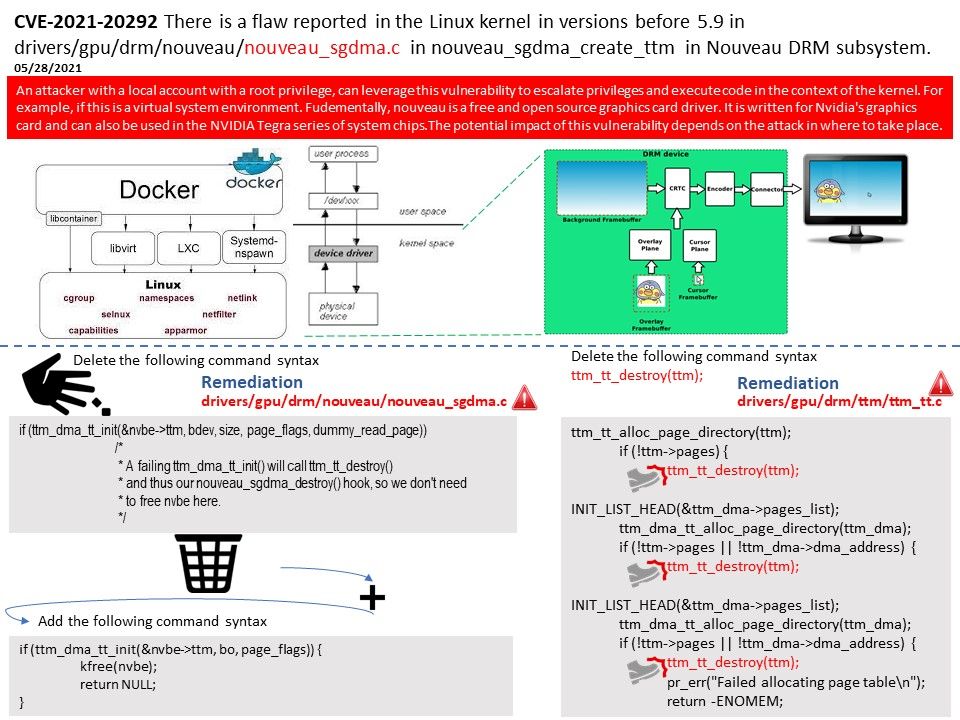
Background: What is DRM subsystem? The Direct Rendering Manager (DRM) is a subsystem of the Linux kernel responsible for interfacing with GPUs of modern video cards. DRM exposes an API that user-space programs can use to send commands and data to the GPU and perform operations such as configuring the mode setting of the display.
Vulnerability details:
There is a flaw reported in the Linux kernel in versions before 5.9 in drivers[/]gpu[/]drm[/]nouveau[/]nouveau_sgdma[.]c in nouveau_sgdma_create_ttm in Nouveau DRM subsystem. An attacker with a local account with a root privilege, can leverage this vulnerability to escalate privileges and execute code in the context of the kernel. For example, if this is a virtual system environment. Fundamentally, nouveau is a free and open source graphics card driver. It is written for Nvidia’s graphics card and can also be used in the NVIDIA Tegra series of system chips.The potential impact of this vulnerability depends on the attack in where to take place.
Workaround: Kernel with CONFIG_SLAB_FREELIST_HARDENED=y option enabled should not be affected with this flaw.
Remedy: This was fixed for Fedora with the 5.7.16 stable kernel updates.
(1).jpg?width=1920&height=1080&fit=bounds)
.jpg?width=1920&height=1080&fit=bounds)