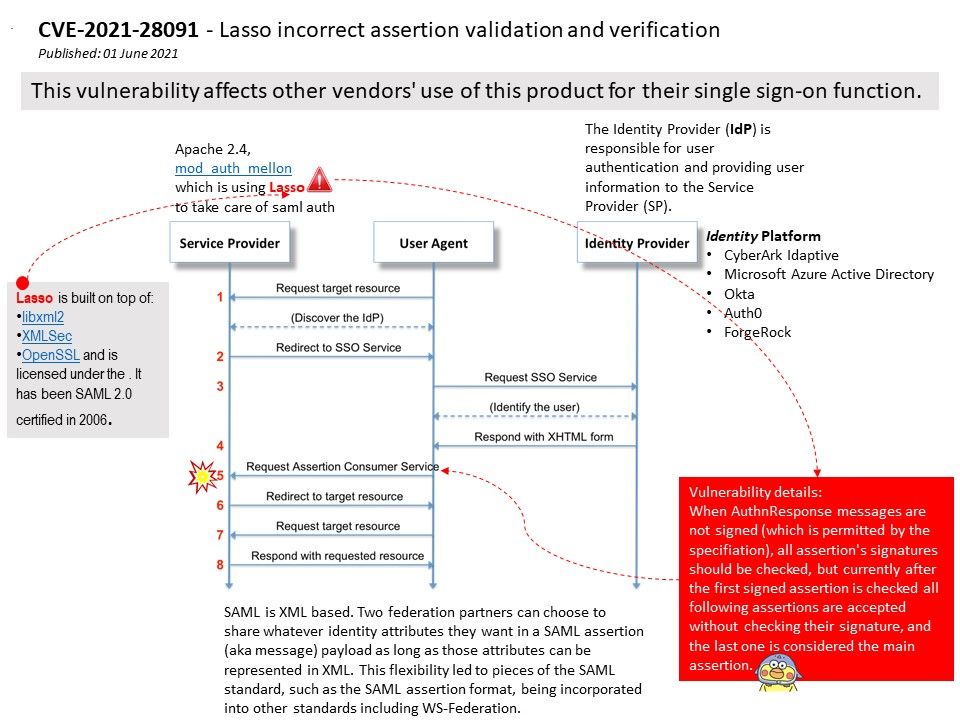
Preface: This vulnerability affects other vendors’ use of this product for their single sign-on function.
Background: Lasso is a free software C library aiming to implement the Liberty Alliance standards; it defines processes for federated identities, single sign-on and related protocols.Lasso is built on top of libxml2, XMLSec and OpenSSL and is licensed under the GNU General Public License (with an OpenSSL exception).
Vulnerability details: Lasso incorrect assertion validation and verification. When AuthnResponse messages are not signed (which is permitted by the specification), all assertion’s signatures should be checked, but currently after the first signed assertion is checked all following assertions are accepted without checking their signature, and the last one is considered the main assertion.
IMPACT:
- SOGo and PacketFence packages use the vulnerable Lasso library so it was impacted.
- Cisco (Adaptive Security Appliance (ASA), Content Security Management Appliance (SMA), Email Security Appliance (ESA), FXOS software, Web Security Appliance (WSA), and Firepower Threat Defense (FTD) as being affected)
Reference URL – https://blogs.akamai.com/2021/06/sogo-and-packetfence-impacted-by-saml-implementation-vulnerabilities.html