24th May, 2021
Preface: It let you avoid malware infection in your computer. MalwareFox can detect and remove malware in precise way. MalwareFox Antimalware at low cost comparing to other competitors.
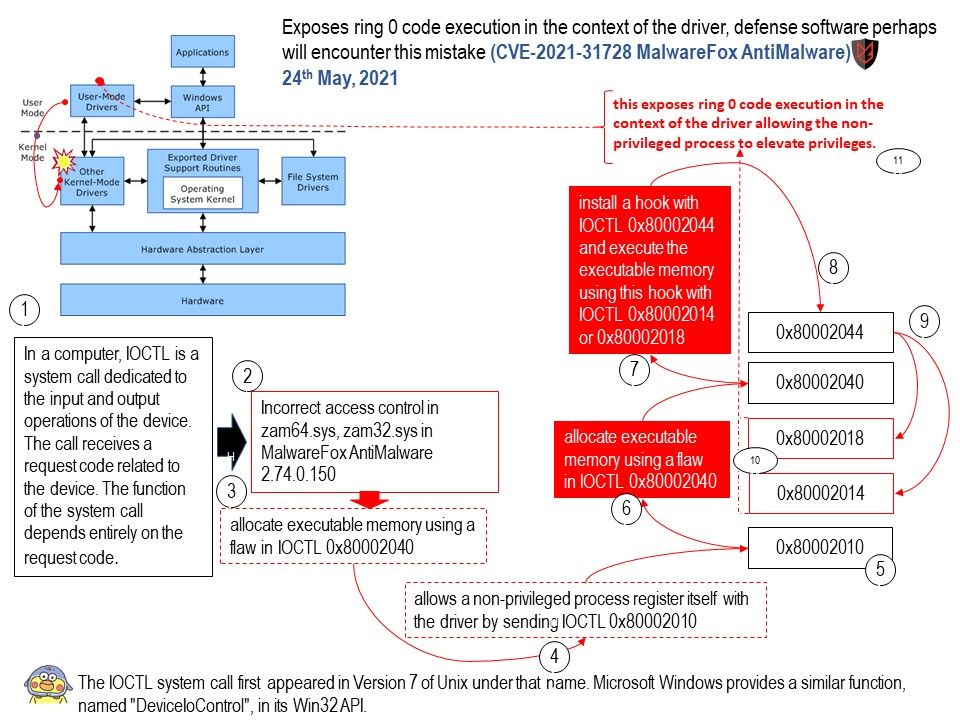
Background: In a computer, ioctl is a system call dedicated to the input and output operations of the device. The call receives a request code related to the device. The function of the system call depends entirely on the request code.
Remark: The ioctl system call first appeared in Version 7 of Unix under that name. Microsoft Windows provides a similar function, named “DeviceIoControl”, in its Win32 API.
Vulnerability details: IOCTL 0x80002040 exposes kernel memory allocation in the NonPagedPool where a user-mode string is copied into the target buffer, this buffer can be used for shellcode by forcing the input data to be larger than 0x1000 bytes, a buffer larger than 0x834 will cause a STATUS_ACCESS_VIOLATION. Hacker must trick the IOCTL into failing and forgetting to free the buffer, you can then search SystemBigPoolInformation for the newly allocated buffer with the shellcode.
* When writing to a file Microsoft sets the bufferSize to 4096 bytes, but when reading they are using [0x1000].
Official details: As of today, vendor does not provide update related to this matter. Their homepage can be found in the following link – https://www.malwarefox.com/