Synopsis: Retrospectively of 2019 Apache load balancer setup – Install Apache on the Load Balancer Server. Enable Proxy Server Modules. Configure Apache Load Balancing. The Apache server architecture includes the Apache Core and modules. Nginx found 2004, it is a performance-oriented HTTP server. Compared with Apache and lighttpd, it has the advantages of less memory and higher stability.
NGINX performs 2.5 times faster than Apache according to a benchmark test performed by running up to 1,000 simultaneous connections. Apache runs on all operating systems such as UNIX, Linux or BSD and has full support for Microsoft Windows. Nginx had equivalent capability. However the performance on Windows is not as stable as that on UNIX platforms.
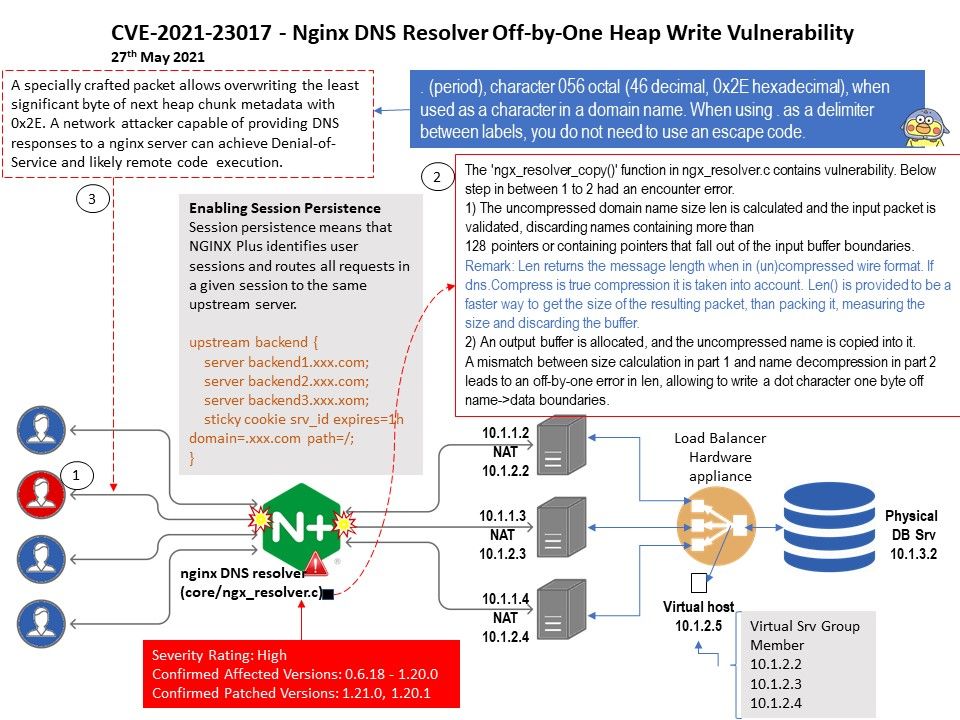
Vulnerability details: On May 26, Nginx issued a security announcement to fix a DNS resolver vulnerability in the nginx resolver (CVE-2021-23017). Due to an error in ngx_resolver_copy() processing DNS responses, when the “resolver” is used in the nginx configuration file During the command, an unauthenticated attacker can forge a UDP packet from a DNS server, construct a specially crafted DNS response and cause 1 byte of memory to be overwritten, resulting in a denial of service or arbitrary code execution.
Vendor Reference: http://mailman.nginx.org/pipermail/nginx-announce/2021/000300.html