Preface: There are plenty of astronomical events every year.
In the evenings of 26 May 2021, it was total lunar eclipse. Do you believe rumours of super moon (astronomical phenomenon)?
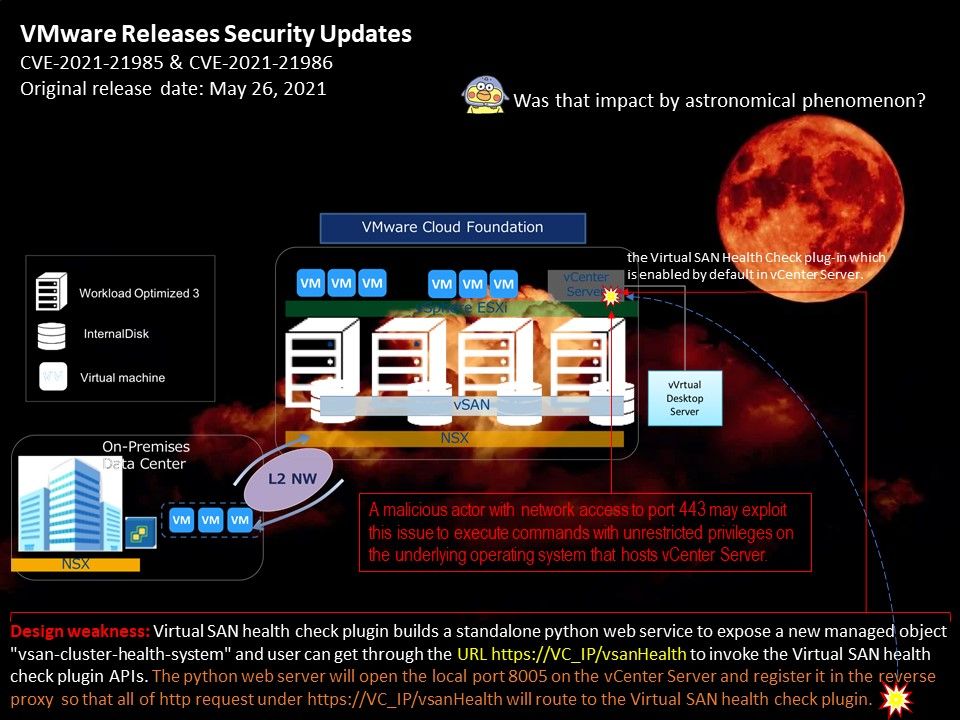
Background: Virtual SAN Health check plugin checks all aspects of a Virtual SAN configuration. It implements a number of checks on hardware compatibility, networking configuration and operations,
advanced Virtual SAN configuration options, storage device health as well as virtual machine object health. The Virtual SAN Health Check plug-in which is enabled by default in vCenter Server.
Vulnerability details: The vSphere Client (HTML5) contains a remote code execution vulnerability due to lack of input validation in the Virtual SAN Health Check plug-in which is enabled by default in vCenter Server.
A remote attacker could exploit some of these vulnerabilities to take control of an affected system.
CVE-2021-21985 – VMSA-2021-0010 (Virtual SAN Health Check Plugin)
CVE-2021-21986 – VMSA-2021-0010 (Virtual SAN Health Check, Site Recovery, vSphere Lifecycle Manager, and VMware Cloud Director Availability Plugins)
Workaround: Plugins must be set to “incompatible.” On vCenter Linux and Windows platforms, simply disabling plugins from within the UI will not prevent exploitation.
Official announcement – https://www.vmware.com/security/advisories/VMSA-2021-0010.html