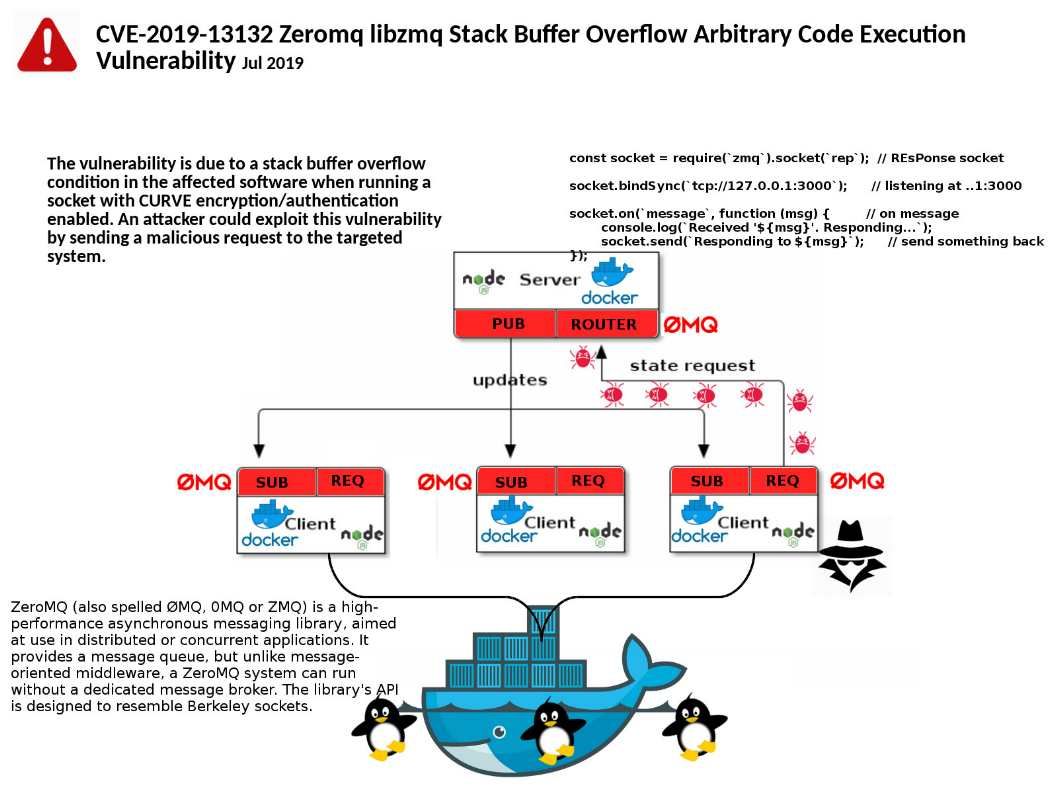
Preface: Message queues are unnecessary and cause a lot of overhead (setup such system cab be a lot of work).
Product background: Zeromq libzmq
A simple synchronous system will just receive a request from the client, perform an operation (anything from retrieving some data from the server to uploading an image) and return a response.
Vulnerability details: A vulnerability in ZeroMQ libzmq could allow an unauthenticated, remote attacker to execute arbitrary code on a targeted system. The problem was that a stack overflow and
overwrite the stack with arbitrary data, due to a buffer overflow in
the library. All versions from 4.0.0 and upwards are affected.
Reference: The stack is the temporary memory where variables are stored while a function is executing. The memory will be cleaned up automatically when job done.
Remedy: ZeroMQ has released a software update. For more information, see url: https://github.com/zeromq/libzmq/releases