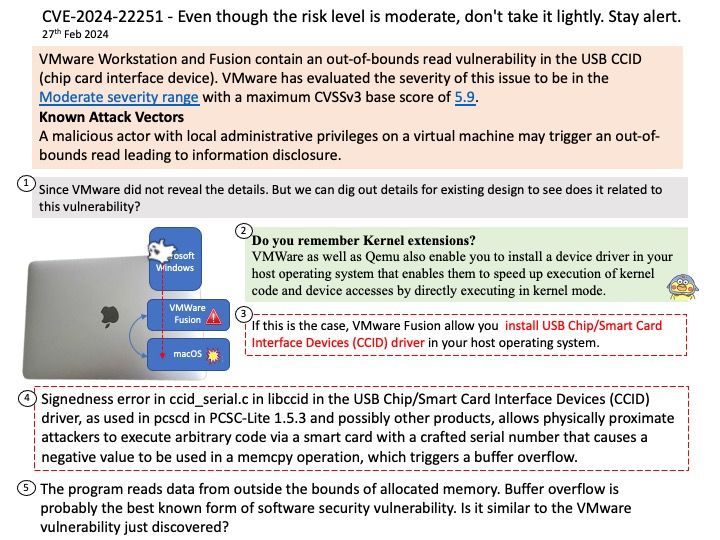
Preface: Kernel extensions – VMWare as well as Qemu also enable you to install a device driver in your host operating system that enables them to speed up execution of kernel code and device accesses by directly executing in kernel mode.
Background: VMware Fusion is a software hypervisor developed by VMware for macOS systems. It allows Macs with Intel or the Apple M series of chips to run virtual machines with guest operating systems, such as Microsoft Windows, Linux, or macOS, within the host macOS operating system.
Vulnerability details: VMware Workstation and Fusion contain an out-of-bounds read vulnerability in the USB CCID (chip card interface device). VMware has evaluated the severity of this issue to be in the Moderate severity range with a maximum CVSSv3 base score of 5.9.
Known Attack Vectors: A malicious actor with local administrative privileges on a virtual machine may trigger an out-of-bounds read leading to information disclosure.
Official announcement: Please refer to the official announcement for details – https://www.vmware.com/security/advisories/VMSA-2024-0005.html