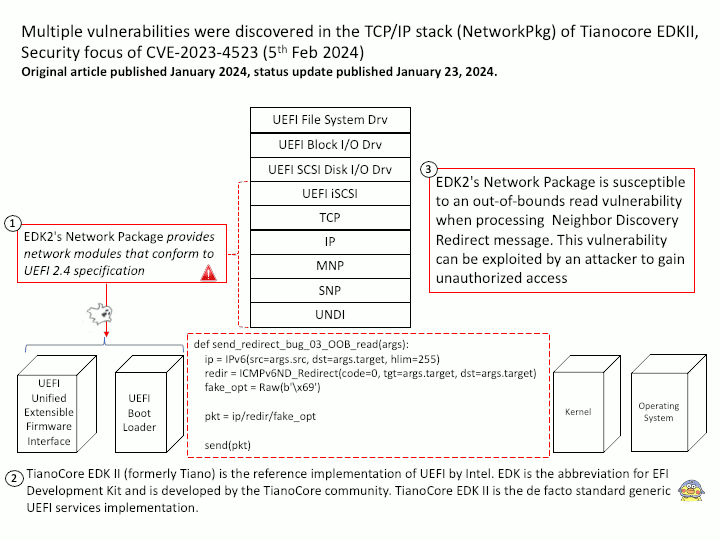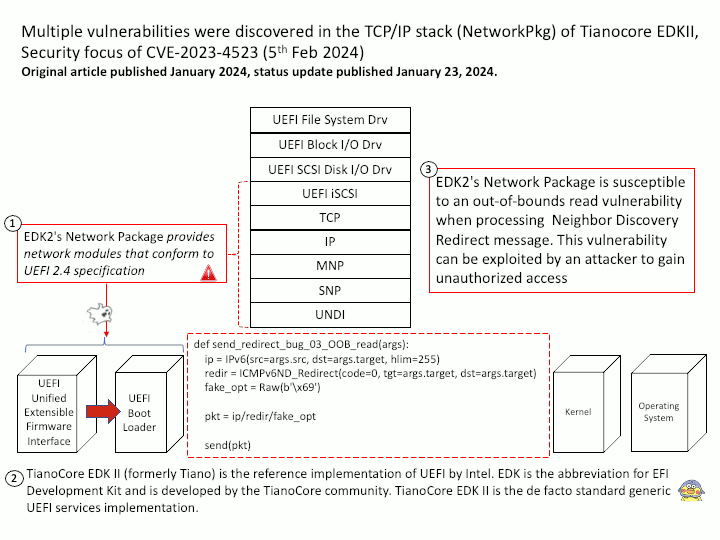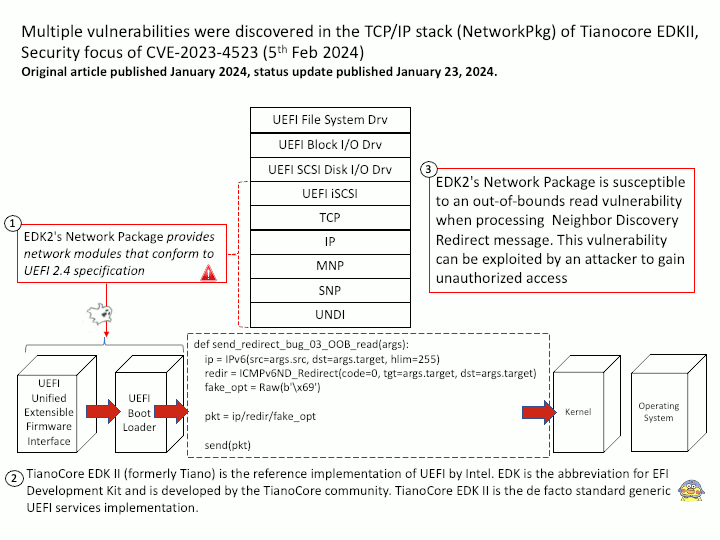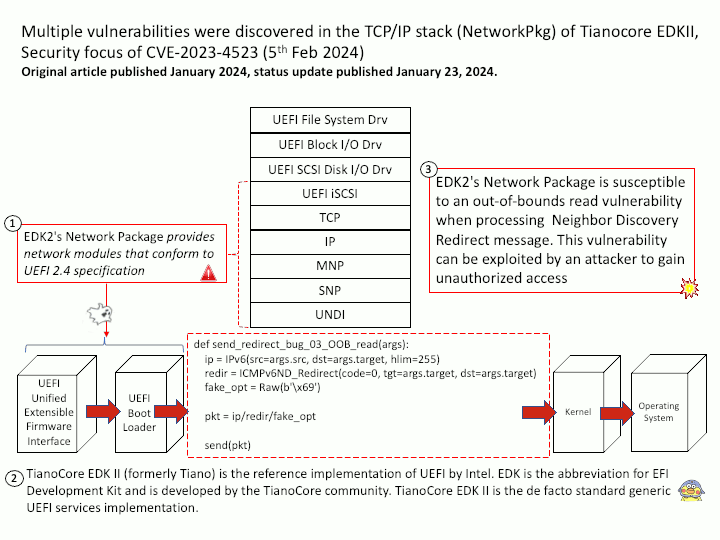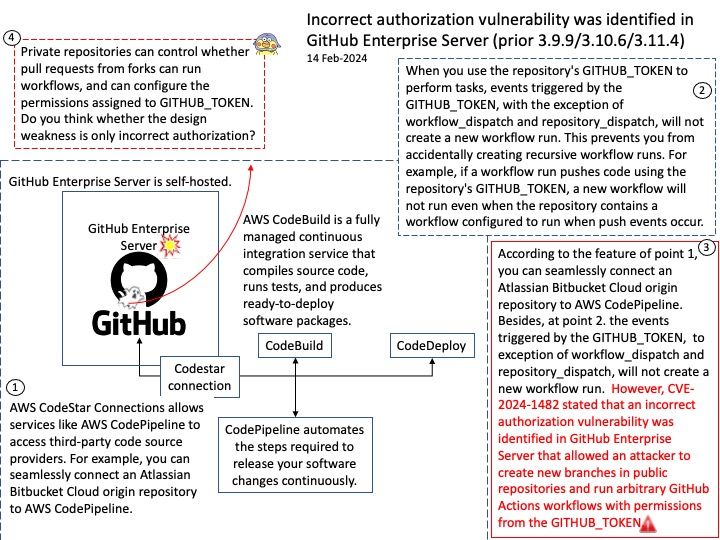
Preface: The main difference between the products is that GitHub Enterprise Cloud is hosted by GitHub, while GitHub Enterprise Server is self-hosted. GitHub Enterprise Cloud includes an enterprise account that lets you manage multiple organizations.
Sign in to the AWS Management Console and open the Developer Tools Console: https://console[.]aws[.]amazon[.]com/codesuite/settings/connections. Select Settings > Connections, then select Make a connection. To establish a connection to an installed GitHub Enterprise Server repository, select GitHub Enterprise Server.
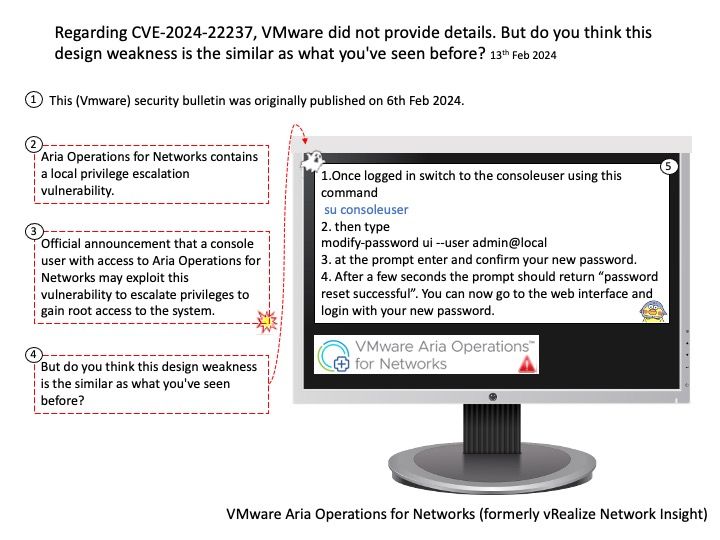
Background: The GITHUB_TOKEN is an automatically generated secret that lets you make authenticated calls to the GitHub API in your workflow runs. Actions generates a new token for each job and expires the token when a job completes.
To modify the permission of the GITHUB_TOKEN, we can make the change at the enterprise, organisation or repository level. To do this go to settings, select Actions then General, here we will find the Workflow Permissions sections.
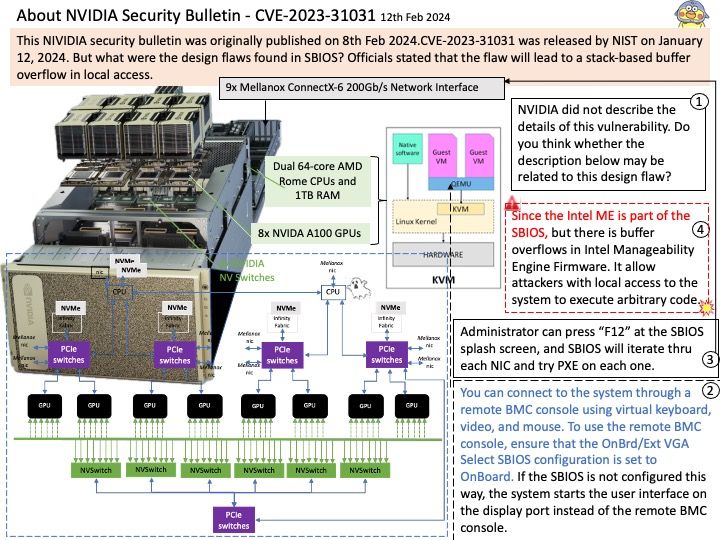
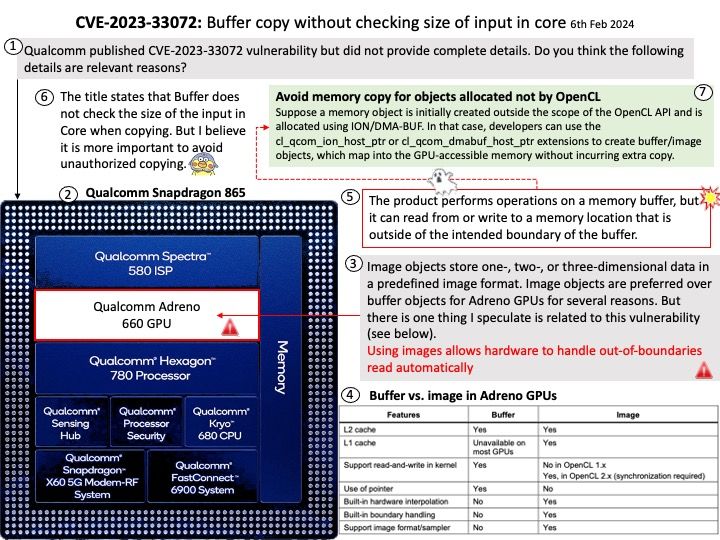
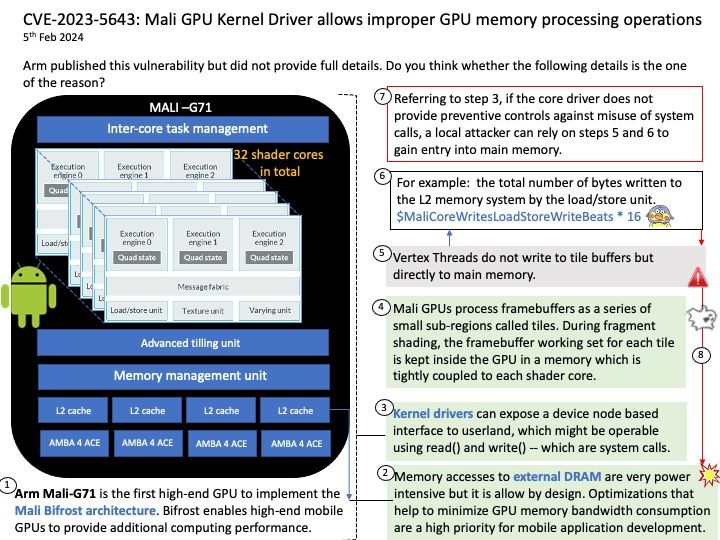
Vulnerability details: An incorrect authorization vulnerability was identified in GitHub Enterprise Server that allowed an attacker to create new branches in public repositories and run arbitrary GitHub Actions workflows with permissions from the GITHUB_TOKEN. To exploit this vulnerability, an attacker would need access to the Enterprise Server. This vulnerability affected all versions of GitHub Enterprise Server after 3.8 and prior to 3.12, and was fixed in versions 3.9.10, 3.10.7, 3.11.5. This vulnerability was reported via the GitHub Bug Bounty program.
Official details: Please refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2024-1482