Preface: Because when using TLS to transmit static content, the data needs to be read into user space and encrypted before the encrypted data can be transmitted. Facebook found that in the process of using TLS, it will spend 2% of the CPU processing copy from/to user space, and 10% of the CPU will be used for encryption.
Background: ktls is informed when data is queued to the socket and the strparser mechanism is used to delineate the records. Upon read request, records are retrieved from the socket and passed to decryption routine.
Linux kernel provides TLS connection offload infrastructure. Once a TCP connection is in ESTABLISHED state user space can enable the TLS Upper Layer Protocol (ULP) and install the cryptographic connection state.
ktls can operate in three modes: Software crypto mode (TLS_SW) , Packet-based NIC offload mode (TLS_HW) and Full TCP NIC offload mode (TLS_HW_RECORD)
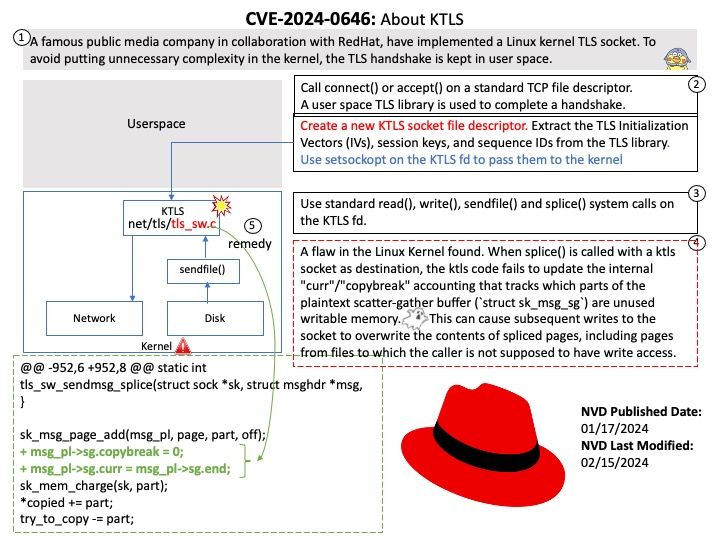
Vulnerability details: An out-of-bounds memory write flaw was found in the Linux kernel’s Transport Layer Security functionality in how a user calls a function splice with a ktls socket as the destination. This flaw allows a local user to crash or potentially escalate their privileges on the system.
Official details: Please refer to the link for details –https://nvd.nist.gov/vuln/detail/CVE-2024-0646