Preface: A two-stage bootloader actually consists of two bootloaders after each other. The first being small with the sole purpose of loading the second one. The second one can then contain all the code needed for loading the kernel.
Background: Secure boot is a security standard developed to help make sure that a device boots using only software that is trusted by the Original Equipment Manufacturer (OEM). When the device starts, the firmware checks the signature of each piece of boot software. If the signatures are valid, the device boots, and the firmware gives control to the operating system.
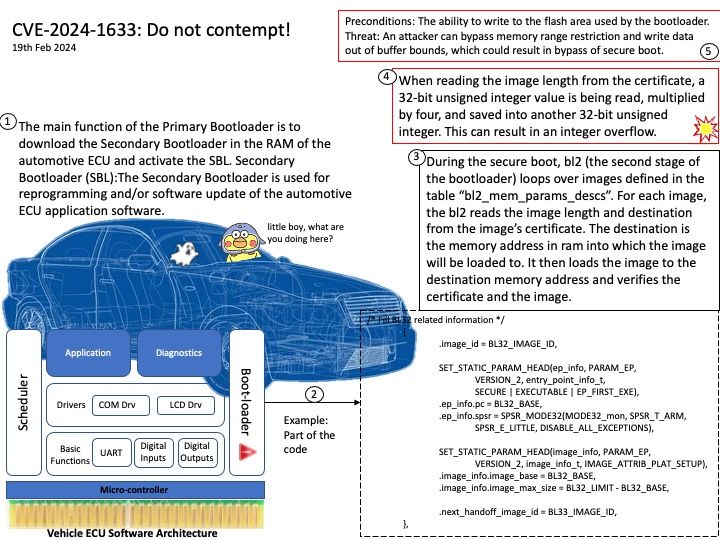
Vulnerability details: During the secure boot, bl2 (the second stage of the bootloader) loops over images defined in the table “bl2_mem_params_descs”. For each image, the bl2 reads the image length and destination from the image’s certificate. Because of the way of reading from the image, which base on 32-bit unsigned integer value, it can result to an integer overflow. An attacker can bypass memory range restriction and write data out of buffer bounds, which could result in bypass of secure boot.
Reference:
An integer overflow occurs when you attempt to store inside an integer variable a value that is larger than the maximum value the variable can hold.
A 32-bit unsigned integer. It has a minimum value of 0 and a maximum value of 4,294,967,295 (inclusive).
Official details: Please refer to the link for details –