Preface: Trusted Firmware-A (TF-A) provides a reference implementation of secure world software for Armv7-A, Armv8-A and Armv9-A, including a Secure Monitor executing at Exception Level 3 (EL3) and a Secure Partition Manager running at Secure EL2 (S-EL2) of the Arm architecture.
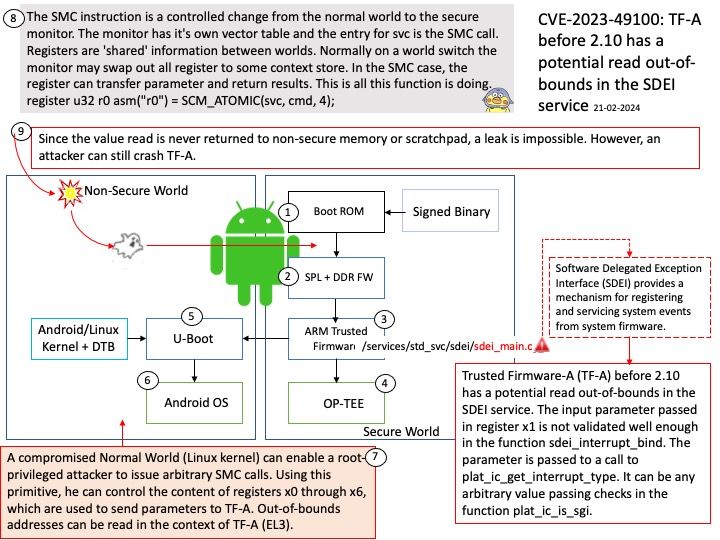
Background: Software Delegated Exception Interface (SDEI) provides a mechanism for registering and servicing system events from system firmware. This specification defines a standard interface that is vendor-neutral, interoperable, and software portable. The interface is offered by a higher Exception level to a lower Exception level, in other words, by a Secure platform firmware to hypervisor or hypervisor to OS or both.
System events are high priority events, which must be serviced immediately by an OS or hypervisor. These events are often orthogonal to normal OS operation and the events can be handled, even when the OS is executing within its own critical section with interrupts masked. System events can be provided to support: Platform error handling (RAS), Software watchdog timer, Sample-based profiling & Kernel debugger.
Vulnerability details: Trusted Firmware-A (TF-A) before 2.10 has a potential read out-of-bounds in the SDEI service. The input parameter passed in register x1 is not validated well enough in the function sdei_interrupt_bind. The parameter is passed to a call to plat_ic_get_interrupt_type. It can be any arbitrary value passing checks in the function plat_ic_is_sgi. A compromised Normal World (Linux kernel) can enable a root-privileged attacker to issue arbitrary SMC calls. Using this primitive, he can control the content of registers x0 through x6, which are used to send parameters to TF-A. Out-of-bounds addresses can be read in the context of TF-A (EL3). Because the read value is never returned to non-secure memory or in registers, no leak is possible. An attacker can still crash TF-A, however.
Official announcement: Please refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2023-49100