Preface: In the modern digital world. Digital signatures replace traditional handwritten signatures for identity verification. In the past, pattern matching methods were used to confirm signature integrity through human observation. The integrity of digital signatures is ensured through the Elliptic Curve Digital Signature Algorithm (ECDSA).
Background: Elliptic Curve Digital Signature Algorithm (ECDSA) is a cryptographic algorithm used by Bitcoin to ensure that funds can only be used by their legitimate owners. The private key is a secret number known only to the person who generated it.
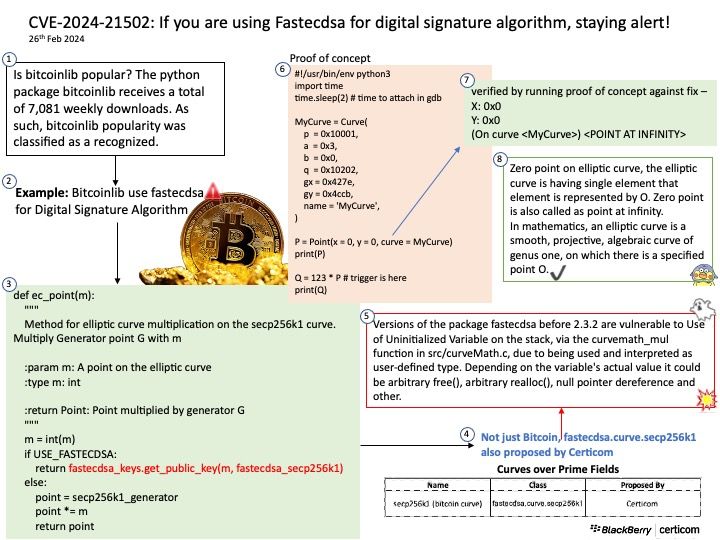
Is bitcoinlib popular? The python package bitcoinlib receives a total of 7,081 weekly downloads. As such, bitcoinlib popularity was classified as a recognized.
Fastecdsa efficient faster than the ecdsa package. There are several examples, how to use fastecdsa package. It proven that fastecdsa capable work with bitcoinlib.
In security point of view, fastecdsa are secure.There is no nonce reuse, no branching on secret material, and all points are validated before any operations are performed on them. Timing side challenges are mitigated via Montgomery point multiplication. Nonces are generated per RFC6979. The default curve used throughout the package is P256 which provides 128 bits of security.
Vulnerability details: Versions of the package fastecdsa before 2.3.2 are vulnerable to Use of Uninitialized Variable on the stack, via the curvemath_mul function in src/curveMath.c, due to being used and interpreted as user-defined type. Depending on the variable’s actual value it could be arbitrary free(), arbitrary realloc(), null pointer dereference and other. Since the stack can be controlled by the attacker, the vulnerability could be used to corrupt allocator structure, leading to possible heap exploitation. The attacker could cause denial of service by exploiting this vulnerability.
Official announcement: Please refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2024-21502