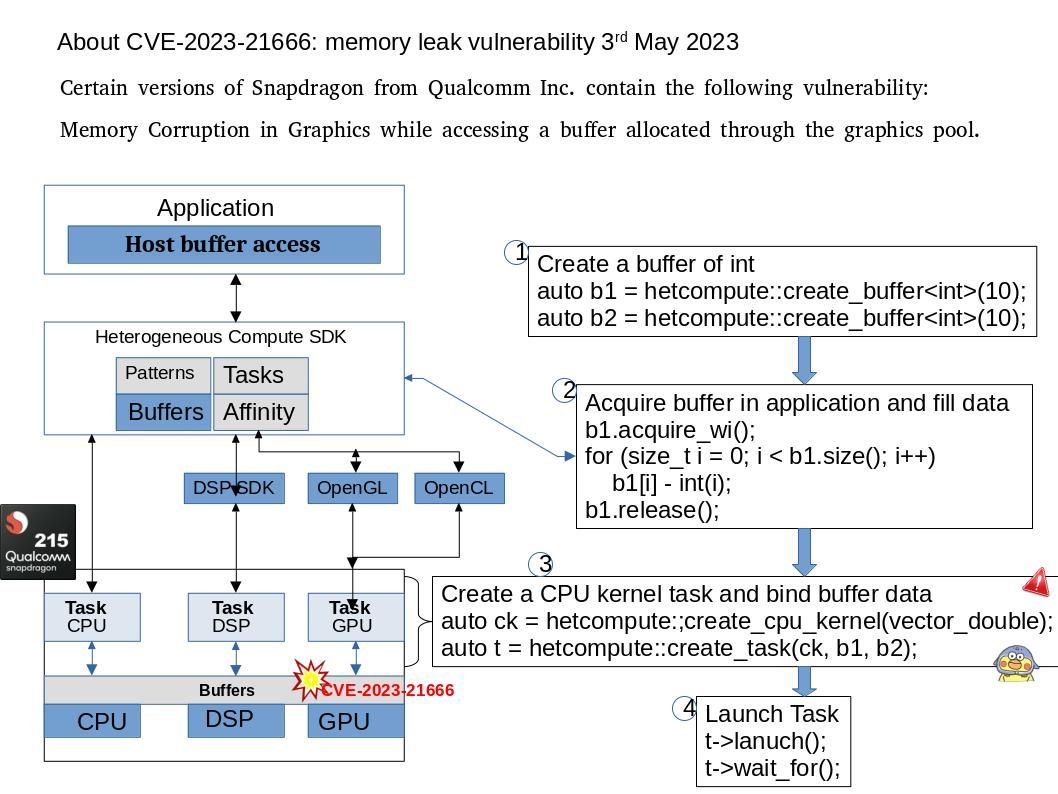
Preface: The product does not sufficiently track and release allocated memory after it has been used. Such design weakness will belongs to CWE-401.
Background: Snapdragon Heterogeneous Compute SDK: provides developers with the ability to allocate work to any of the three processors on Snapdragon. The SDK provides C++ API’s for the Kryo CPU and Adreno GPU, the latter of which interacts through OpenGL and OpenCL calls.
Vulnerability details: Improper Release of Memory Before Removing Last Reference (`Memory Leak`) in Graphics.
Solution: Official announcement, please refer to the link – https://git.codelinaro.org/clo/la/kernel/msm-4.19/-/commit/9968fcdd9d1c853d0c6472307510a81f5db398da