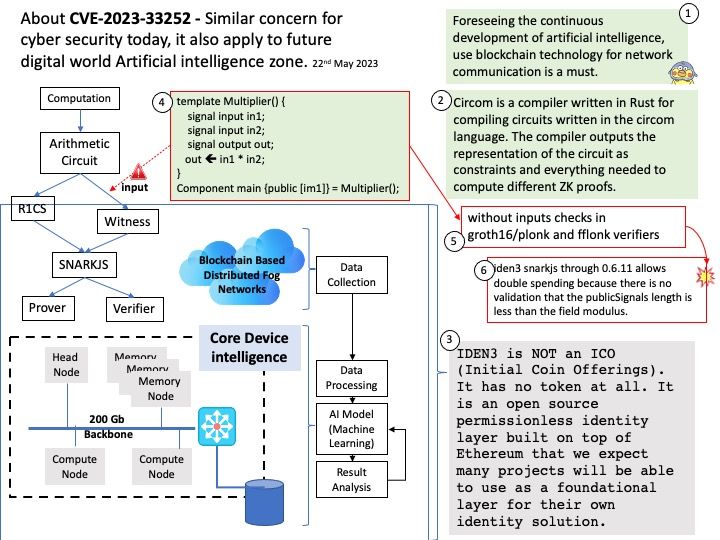
Preface: Foreseeing the continuous development of artificial intelligence, use blockchain technology for network communication is a must.
A blockchain is a distributed database or ledger shared among nodes in a computer network. They are known for their key role in maintaining a secure and decentralized record of transactions in cryptocurrency systems, but they are not limited to the use of cryptocurrencies.
Background: IDEN3 is NOT an ICO (Initial Coin Offerings). It has no token at all. It is an open source permissionless identity layer built on top of Ethereum that we expect many projects will be able to use as a foundational layer for their own identity solution.
What are Initial Coin Offerings? ICOs are another form of cryptocurrency that businesses use in order to raise capital. Through ICO trading platforms, investors receive unique cryptocurrency “tokens” in exchange for their monetary investment in the business.
Ref: Circom is a compiler written in Rust for compiling circuits written in the circom language. The compiler outputs the representation of the circuit as constraints and everything needed to compute different ZK proofs.
Vulnerability details: iden3 snarkjs through 0.6.11 allows double spending because there is no validation that the publicSignals length is less than the field modulus.
References:
https://github.com/iden3/snarkjs/commits/master/src/groth16_verify.js
https://github.com/iden3/snarkjs/tags